On This Page
Unified Security Policy
In the Unified Security Policy™ you can define the requirements that you want to use to govern the resources and traffic on your network. The requirements defined in the Unified Security Policy provide continuous compliance and any violations of those requirements are shown in the Violations browser
In the Unified Security Policy you can create security zone matrices. A security zone matrix is a set of requirements of rule definitions, or traffic that must be blocked or allowed between the security zones. At a glance you can review these requirements in an easy-to-read, color-coded matrix and see if changes need to be made. You can define a matrix with requirements from industry standards, such as NERC CIP, or internal corporate network requirements.
• Only administrators and super administrators can access the Unified Security Policy tab.
• Note: IPv6 is not supported for this TOS feature.
• Note: User Networks zones is not supported for USPs.
Handling addresses that are not associated with any zone
SecureTrack includes a predefined Unassociated Networkszone that includes all private addresses that are not included in any other defined SecureTrack zones.
You can add this zone to any USP matrix and define the behavior of this zone relative to all other zones or to specific zones in the environment.
The Unassociated Networks zone is included in the calculations for Violations in SecureTrack, Risk Analysis in SecureChange, and in Compliance checks in SecureApp.
Getting Started
To create a Unified Security Policy component, you need to:
- Prepare your security zones.
- Create a new security zone matrix.
- Prepare a security zone matrix file.
- Import the security zone matrix file.
- (optional) Configure device and interface preferences for a security zone. This lets you customize the violations results by excluding specific devices from any calculations for a zone, or by indicating that a specific device interface leads to a specific zone.
What can I do on this page?
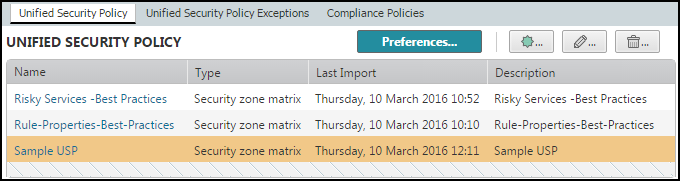
- View a security zone matrix - Click on the name of a security zone matrix to view it.
- Add a security zone matrix - Click
 .
. - Configure Device and Interface Preferences - Click
 to configure the preferences for a security zone matrix. You can exclude one or more devices from a security zone, or indicate that a specific interface leads to a specific zone.
to configure the preferences for a security zone matrix. You can exclude one or more devices from a security zone, or indicate that a specific interface leads to a specific zone. - Edit a security zone matrix - Select a security zone matrix and click
 .
.You can edit the name and description fields.
- Delete a security zone matrix - Select a security zone matrix and click
 .
.
How Do I Get Here?
Audit > Compliance > Unified Security Policy
