On This Page
Adding Check Point R8x MDS Devices
After you upgrade a monitored Check Point MDS device to R8x, you must upgrade the device in SecureTrack to use Check Point R8x support. A CMA can be assigned to an MDS after the initial configuration is complete.
Prerequisites
You will need to complete the following prerequisite steps to add Check Point Multi-Domain Security (MDS) devices to SecureTrack:
-
Configure the Check Point server for OPSEC communication with SecureTrack.
-
Configure the Check Point device to use your SecureTrack server as a GUI client.
The SecureTrack server is displayed in a revision in the GUI client column.
-
Create a Check Point user with Rest API Access to retrieve revisions:
-
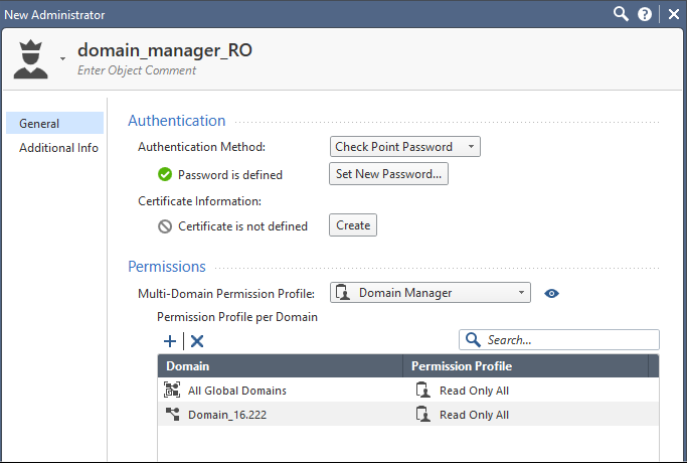
SecureTrack uses Check Point APIs to connect to (and monitor) Check Point R8x devices. A user with the Domain Manager profile who has the Read Only All Permission Profile configured for All Global Domains with the required collection access via the Check Point APIs can retrieve revisions for the device.
To allow the SecureChange Designer tool to provision changes to Check Point devices, the API user must have a Read/Write All permission profile or a customized profile with API and change permissions for all policies and objects.On an MDS:
-
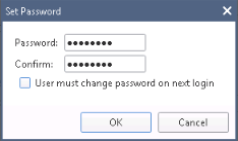
To maintain the password you defined for the Check Point user with REST API access, in Set Password, uncheck User must change password on next login.
-
Monitoring a Check Point Device
-
In TOS Aurora, go to Monitoring
 > Manage Devices.
> Manage Devices. -
Select the appropriate device type.

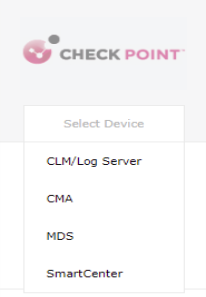
-
Configure the device settings:
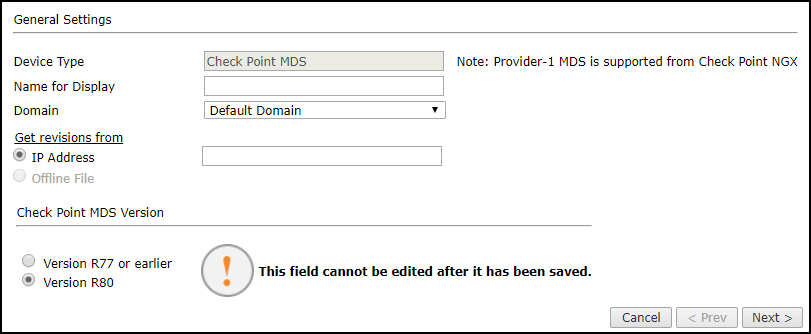
Depending on the Check Point server type, some or all of the following options will appear:
-
Device Type: Check Point MDS (filled automatically)
-
Name for Display
-
Domain: Available only if you have configured your system for managing multi-domains and All Domains is currently selected. Select the domain to which to add the device. The Domain can only be entered when adding a device; to change the Domain, you must migrate the device.
-
Get revisions from: One of the following:
-
IP Address: Revisions are retrieved automatically
-
Offline File: (If available) Revisions are manually uploaded to SecureTrack for Offline Analysis
This option is not available for R80.x MDS devices
-
-
ST server: In a distributed deployment, select which TOS Aurora cluster monitors this device (not shown in image)
-
Check Point MDS version: Select the Check Point version installed on the MDS:
-
Version R77 and below
-
Version R8x
After you save the device configuration, you cannot change this setting.
-
-
-
Click Next.
-
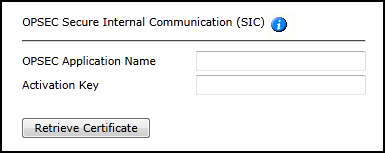
Configure OPSEC Secure Internal Communication (SIC):
-
Enter TOS Aurora's OPSEC Application Name as you defined it for this Check Point server (case sensitive).
-
Enter the Activation Key as defined when the OPSEC object was created.
-
Click Retrieve Certificate to setup encrypted communication between SecureTrack and the Check Point device.
The certificate appears, and the following message is displayed:

-
-
Click Next.
-
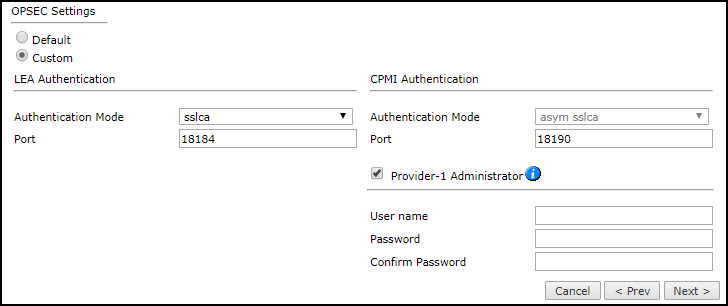
In the OPSEC Settings:
-
Select Custom.
-
Configure the LEA Authentication fields:
-
Authentication Mode - Some options require you to enter an SL or FWN1 Secret Key in the Authentication Keyssection and Establish Authentication Key.
-
Port
-
-
Configure the CPMI Authentication fields:
-
Authentication Mode - asym sslca (filled automatically)
-
Port
-
-
To include monitoring of the Global Database for a Provider-1 MDS, select Provider-1 Administrator and configure the Provider-1 Superuser credentials.
For Global Database monitoring, TOS Aurora must also be set as a valid GUI client for the MDS.
-
-
Click Next.
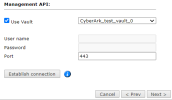
- For MDS devices with R8x, in the Management API settings:
- Enter the credentials for an administrator on the Check Point device. To use a vault server that contains access credentials, select Use Vault and select the server. For more information, see Configuring a Vault Server.
- Enter the port that the Check Point device uses for REST API connections.
- Click Establish Connection to setup encrypted communication between SecureTrack and the Check Point device. The certificate appears, and the following message appears:

-
Click Next.
-
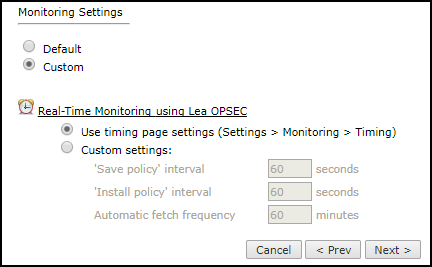
In the monitoring settings, do one of the following:
-
To use timing settings from the Timing configuration for this device, select Default.
-
To define specific timing settings for this device, select Custom, then select Custom settings, and configure:
-
'Save policy' interval: When a Save Policy event is followed within this time interval by an Install Policy event for the same policy, SecureTrack tries to combine the two events into a single revision. The default value is 60 seconds.
-
'Install policy' interval: When two or more Install Policy events for the same policy occur within this time interval, SecureTrack combines the events into a single Install Policy revision (Default: 60 seconds)
-
Automatic fetch frequency: Frequency (in minutes) for automatic fetch
-
-
-
Click Next.
-
You can test the communication with the Check Point server by clicking Test Connectivity:
-
Click Save.
The Check Point device is shown in the Device Configuration list.
If you use non-standard LEA authentication, see Non-Standard LEA Authentication.
-
If you have a secondary Check Point management server, configure SecureTrack to communicate with the secondary server in the event of a failover.
Define an Internet Object
To customize the device object that represents the Internet, see Define Internet Object.
How Do I Get Here?
In SecureTrack, go to Monitoring ![]() > Manage Devices.
> Manage Devices.