On This Page
Monitoring Microsoft Azure Cloud Platform
Overview
TOS Aurora monitors the Microsoft Azure Resource Manager (RM) platform for policy revision changes.
To see which TOS features are supported for your device, review the feature support table. Classic rules - rules that have been configured on the firewall directly and not included in Azure firewall policies - are not supported.
Prerequisites
To complete the Microsoft Azure configuration procedures, you must have the following connection information for Microsoft Azure Resource Manager:
|
ID Information |
Description |
|---|---|
|
Subscription ID |
The ID for an active Azure subscription - see Find your Azure subscription (Microsoft documentation) |
|
Tenant ID |
A Tenant represents a single organization, and is the dedicated instance of Azure Active Directory (AD) you receive when you sign up for Azure AD services. Each Tenant is completely isolated, and all your data and identity information is kept distinct and separate from other Tenants - see Get Tenant ID. |
|
Application ID |
An Application ID (also referred to as a Client ID) is the unique ID provided by Azure Active Directory (AD) for any registered application. You must register an application in your Tenant to authenticate the application to access to your network or data. See |
|
Application Secret |
An Application Secret (also known as a Client Secret, Shared Secret, or Keys) is credentials used by an application to authenticate itself to a Tenant when signing in to Azure AD - see Get application ID and authentication key. These keys do not refer to key vaults. |
Additional information from Microsoft documentation:
Add a Microsoft Azure Device
-
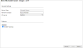
Select the appropriate device type:
-
Configure the device settings:
- Name for Display
-
Domain: Available only if you have configured your system for managing multi-domains and All Domains is currently selected. Select the domain to which to add the device. The Domain can only be entered when adding a device; to change the Domain, you must migrate the device.
-
ST server: In a distributed deployment, select which TOS Aurora cluster monitors this device (not shown in image)
- Enable Topology: Collects routing information for building the network Interactive Map.
-
Click Next.
-
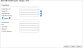
Configure the TOS Aurora connection to the Microsoft Azure device, according to the parameters required by the device:
-
If you connect to the device with a proxy server, select Proxy and enter the HTTPS Proxy Hostname or IP, Port, Username, and Password.
-
Click Next.
-
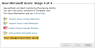
In Monitoring Settings, do one of the following:
- To use real-time monitoring and timing settings from the Timing page, select Default.
Otherwise, select Custom and configure the monitoring mode and settings.
- In Periodic Polling, select Custom settings and configure the Polling frequency: How often TOS Aurora fetches the configuration from each device.
If you select 1 day, you can then select the exact time (hour and minute) for the daily polling.
- Click Next.
-
Save the configuration.
The Microsoft Azure device now appears in the Monitored Devices tree.
-
You can now do one of the following:
-
Import Virtual Networks,
-
Import Azure Load Balancers,
-
Import Azure Firewall Policies
-
Add another Microsoft Azure
-
- Click Done.
Importing Virtual Networks requires that the vnet has at least one VNIC.
How Do I Get Here?
In TOS Aurora, go to Monitoring ![]() > Manage Devices.
> Manage Devices.