On This Page
Zone Mapping
Overview
Zone mapping (also called MZTI - mapping zones to interfaces) lets you define your security policy for network traffic between zones and device interfaces. This feature further refines your unified security policies (USPs), where you define policies for routes crossing from one zone to another. Zone mapping definitions determine when a violation is logged for the device.
What Can I See?
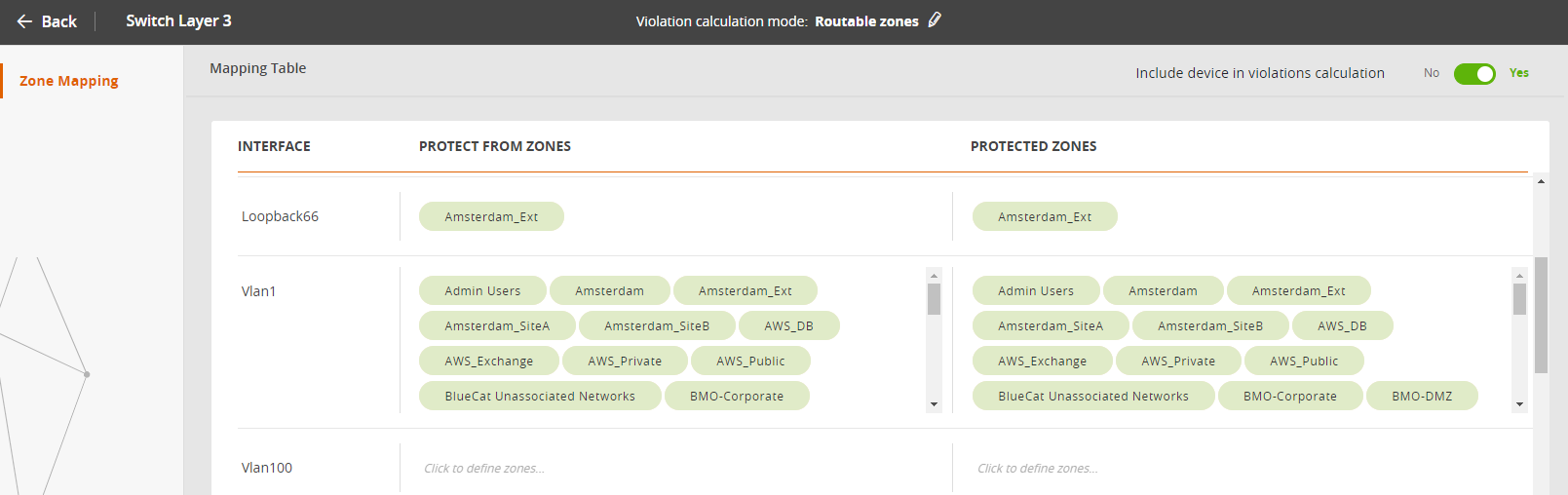
The Zone Mapping page displays the zones that will be considered connected to the device when determining violations in USPs. The zones are listed separately for each interface in two separate groups:
- Protected From Zones: zones in routes that bring traffic to each device interface
- Protected Zones: zones in routes that receive traffic from each device interface
The protection policy referred to above for both of these groups of zones applies only from one interface to another. A violation is never counted for routes to and from the same interface.
The zones associated with each interface are added automatically, based on their topology. For each device interface, SecureTrack finds the security zone that contains the IP address of the interface and associates that zone with the interface. In addition to the IP address match, SecureTrack also uses routing tables to associate the zones with interfaces (see Zone Mapping). Only zones used in one or more USPs will be included. The Internet zone is added automatically only when the Violation Calculation Mode is set to Connected Zones.
What Can I Do Here?
Specify Connected Zones
When you select a device from the Device Viewer, the zone mapping window appears.
If you want to add zones that do not appear or exclude those that have been added automatically based on topology, you can do that manually.
Manually Adding Zones
Zones that are not added automatically based on topology can be added manually. To add a zone to an interface, click in the desired cell and then start to type the name of the zone you want to add. Auto-complete will fill in matching zone names as you type and you can select as needed. Once added, an icon indicates that the zone was added manually, e.g.![]()
To remove a manually added zone, hover over it and click X.
Excluding Automatically Added Zones
To exclude an automatically-added zone from being mapped to the interface, hover over it and click X. The icon color changes to grey and the text changes to strikethrough.
![]()
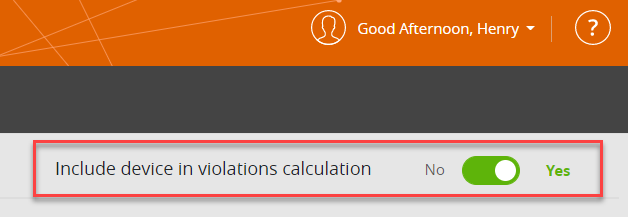
Switch Violation Calculation On/Off
You can include or exclude the device in violation calculations.
- No: Routes to/from this device will never be considered in violation calculations. SecureTrack ignores all other settings on this page.
- Yes: Routes to/from this device will be considered in violation calculations. This is the default setting.
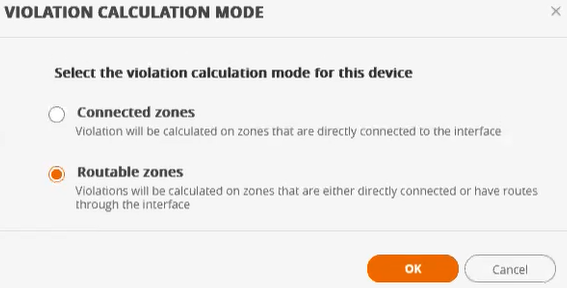
Set Violation Calculation Mode
A route can span (hop) a number of devices and zones before or after a device, which is connected directly to the current device. The violation calculation mode specifies whether these hops should be included in the violation calculation.
There are two possible modes:
- Connected Zones: SecureTrack only considers the zone of the directly-connected device.
- Routable Zones: SecureTrack considers zones of all devices on the route.
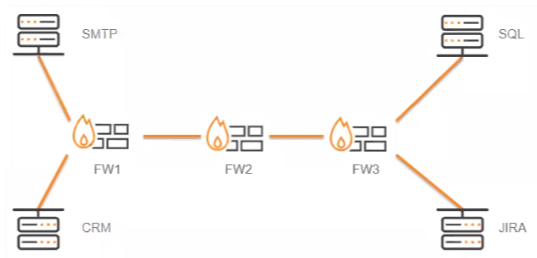
Here is an example of a network:
For our example, we will use the access request from the SMTP server to the SQL server:
-
If you select Routable Zones, SecureTrack considers the zones for all three firewalls (FW1, FW2, and FW3) in the violation calculation.
-
If you select Connected Zones, SecureTrack considers only the zone of the device in the final hop of the route (FW3) in the violation calculation.
How Do I Get Here?
Click Monitoring ![]() > Device Viewer and select a device.
> Device Viewer and select a device.