On This Page
Preparing a CSV
Prerequisites
You must define your security zones before you can import a security zone matrix.
Procedure
When you create a matrix file to import, you must include the following fields:
-
From zone - The name of the source network zone in Browser > Zones
-
To zone - The name of the destination network zone in Browser > Zones
-
Severity - The severity assigned to the violation: low, medium, high, critical
-
Access Type - Traffic from the source zone and to the destination zone must be:
- Allow all - All traffic is allowed
- Block all - All traffic is blocked
- Allow only - Traffic is allowed only if the traffic service is in the list of services
- Block only - Traffic is blocked only if the traffic service is in the list of services
-
Services (for Allow Only or Block Only access) - The services that are allowed to pass from the source zone and to the destination zone. See list of Tufin Predefined Services.
-
You can enter multiple values separated by a semicolon, for example: tcp 80; icmp 8
-
You can enter a range of ports, for example: tcp 67-68
-
You can enter any so that all services are allowed.
-
Rule Properties (for Allow Only or Block Only access) - The rules that match the specified traffic requirements are allowed:
-
EXPLICIT_SOURCE - Rules must have an explicit source, not the ANY value
-
EXPLICIT_DESTINATION - Rules must have an explicit destination, not the ANY value
-
EXPLICIT_SERVICE - Rules must have an explicit service, not the ANY value
-
HAS_COMMENT - Rules must have text in the comment field
-
IS_LOGGED - Rules must be configured to create log entries
-
LAST_HIT_WITHIN {DAYS: X} - Rules must have hits within the last X number of days
-
SOURCE_MAX_IP {COUNT:X} - Source must contain less than X IP addresses
-
DESTINATION_MAX_IP {COUNT:X} - Destination must contain less than X IP addresses
-
SERVICE_MAX_SERVICES {COUNT:X} - Service must contain less than X services
- Flows (for Allow Only or Block Only access) - The rules that match the specified traffic requirements are allowed or blocked. Flows are defined by host and subnet objects. Host objects are any object, multiple objects or group of objects where each object represents one IP address. Subnet objects are any object, multiple objects or group of objects where each object represents more than one IP address, not including ANY or Internet.
- HOST_TO_HOST - Rules where the source and destination of the traffic flow are defined by hosts objects
- SUBNET_TO_HOST - Rules where the source of the traffic flow is defined by subnet objects and the destination is defined by host
- HOST_TO_SUBNET - Rules where the source of the traffic flow is defined by host objects and the destination is defined by subnet objects
Separate multiple values with a semicolon, for example: IS_LOGGED; Last_Hit_Within {days: 90}
To enforce Rule Properties on all services, set the Access Type to Allow Only and Service to Any, then add the desired Rule Properties.
The syntax for the flow requirement is either:
To enforce flows on any service, set the Access Type to Allow Only and Service to Any, then add the desired flows.
The rows of the USP matrix must be preceded by a line with each of the headings above, followed by the lines of the matrix data.
from zone,to zone,severity,access type,services,rule properties,flows,description
Sample Code
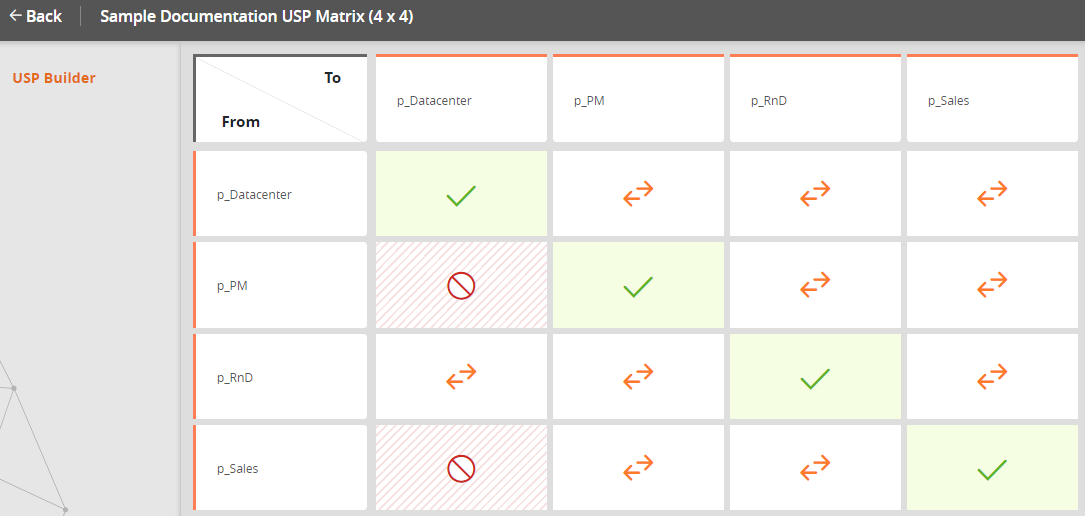
The sample code shown below creates a sample 4x4 USP matrix. After importing the zones and the USP, you will have the following USP:
The sample code adds the zones required by the USP matrix. You must import the zones via Browser > Zones before importing the USP matrix.
#Zone Properties,, zone name,description, p_Datacenter,, p_PM,, p_RnD,, p_Sales,, p_WebServers,, #Zone Hierarchy,, parent,child, p_Datacenter,p_WebServers, #Zone Subnets,, zone name,subnet,description p_Datacenter,192.168.1.1/255.255.0.0, p_PM,10.100.10.1/255.255.255.0, p_RnD,172.16.1.1/255.255.0.0, p_RnD,2001:0db8:85a3:0000:0000:8a2e:0370:7334/36,IPv6 address p_Sales,10.100.2.0/255.255.255.0, p_WebServers,192.168.10.0/255.255.255.0, #Zone Security Groups zone name,security group name,description p_Sales, SecGrp_Sales, Sales VMs p_WebServers, SecGrp_Web, Web Server VMs
The sample code shown below creates a 4x4 USP matrix.
from zone, to zone, severity, access type, services, rule properties, flows
p_Datacenter,p_Datacenter,high,allow all,,,
p_Datacenter,p_PM,low,allow only,ssh,HAS_COMMENT;IS_LOGGED;LAST_HIT_WITHIN {days:90},
p_Datacenter,p_RnD,low,allow only,ssh,HAS_COMMENT;IS_LOGGED;LAST_HIT_WITHIN {days:90},host_to_host
p_Datacenter,p_Sales,low,allow only,any,HAS_COMMENT;IS_LOGGED;LAST_HIT_WITHIN {days:90},host_to_subnet
p_PM,p_Datacenter,high,block all,,,
p_PM,p_PM,high,allow all,,,
p_PM,p_RnD,low,block only,telnet,,host_to_host
p_PM,p_Sales,low,block only,telnet,,host_to_host
p_RnD,p_Datacenter,high,allow only,https;ssh,EXPLICIT_SOURCE;EXPLICIT_DESTINATION,
p_RnD,p_PM,low,block only,telnet,,
p_RnD,p_RnD,high,allow all,,,
p_RnD,p_Sales,low,block only,telnet,,subnet_to_host
p_Sales,p_Datacenter,high,block all,,,
p_Sales,p_PM,low,allow only,https;ssh;tcp 3306;udp 53;tcp 67-68,SOURCE_MAX_IP {COUNT:10};DESTINATION_MAX_IP {COUNT:10},
p_Sales,p_RnD,low,allow only,https;ssh;tcp 3306;udp 53;tcp 67-68,SERVICE_MAX_SERVICES {COUNT:3};EXPLICIT_SERVICE,
p_Sales,p_Sales,high,allow all,,,