On This Page
Configuring a Juniper Netscreen device to Send Syslogs
For SecureTrack to be able to associate syslogs with their respective firewalls, each Netscreen device that sends syslogs to SecureTrack must have a unique hostname.
Syslog traffic must be configured to arrive to the TOS Aurora cluster that monitors the device at the Syslog VIP.
For more information see Sending Additional Information via Syslog.
Syslog proxy is supported for specific devices. For more information on syslog proxy support for supported devices, see Configuring Devices to Send Logs (Configuring Devices to Send Logs).
Only rules that are marked for logging in the device are included in the syslogs.
To define SecureTrack as a syslog server on a Netscreen device:
- Log into the firewall's web interface.
-
In the navigation pane, under Configuration > Report Settings, select Syslog:
-
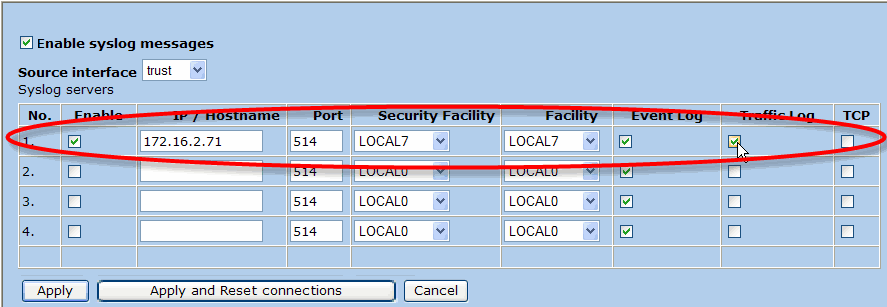
Configure a row with the following settings:
-
Enable: Selected
-
IP/Hostname: The syslog VIP address of the cluster that is managing the device.
The Hostname for the device must be explicitly set via syslog for Real Time Monitoring to retrieve data.
-
Port: 514
-
Security Facility: LOCAL7
-
Facility: LOCAL7
If you need to use a different facility, you can, in which case you'll also need to configure SecureTrack as described in this tech note.
-
Event Log: To enable identification of users who made policy changes and the time of those policy changes, Event Log must be selected.
-
Traffic Log: To enable Usage reporting, Traffic Log must be selected.
-
TCP: Cleared.
-
- Click Apply.
-
In the navigation pane, click Log Settings:
-
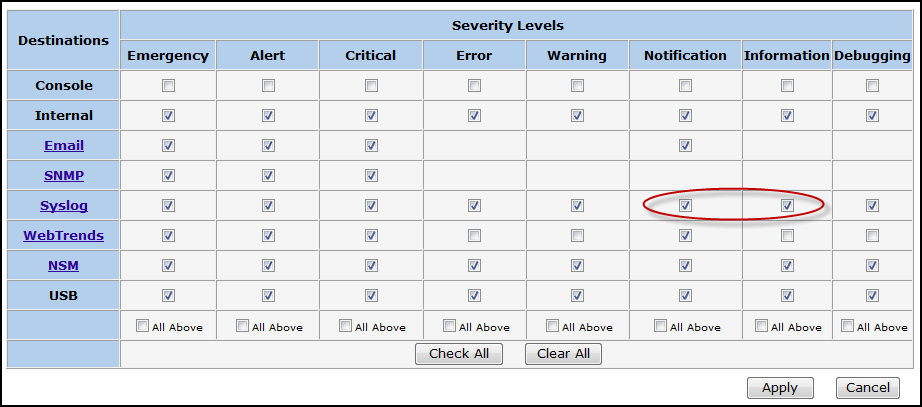
Make sure that in the Syslog row, Notification and Information are selected:
- Click Apply.
