On This Page
Implementing ISO 27001:2022 Using USP
Overview
ISO 27001 identifies the requirements for establishing, implementing, maintaining, and continuously improving an Information Security Management System (ISMS). You can implement controls for ISO 27001 compliance that are tailored to your specific business requirements and network topology using a Unified Security Policy (USP).
Overview
To implement best practices or the compliance regulations of a standard, you need to create a USP Matrix containing the compliance zones required by the standard. The compliance zones are placeholder zones into which you place your network zones, using SecureTrack zone hierarchies. Your existing zones can then be collected into these compliance zones, to ensure compliance monitoring of your entire network. To ensure that you maintain ongoing compliance as your network topology evolves, we recommend that you periodically review the hierarchy of your compliance zones.
Network segmentation is unique to each company, and therefore varies based on their specific critical cyber asset content. The granularity of the connections between the zones of protection, internal networks, and the internet will also vary by company.
ISO 27002, which provides guidance on ISO 27001 controls implementation, makes the following recommendations for compliance zones:
- Divide large networks into separate network domains (segments)
- Consider physical and logical segregation
- Define domain perimeters
- Define traffic rules between domains
- Use authentication, encryption, and user-level network access control technologies
- Consider integration of the organization’s network and segments with those of business partners
In addition, ISO 27002, provides further guidance on network segmentation:
- Criteria-based segmentation: Predefined rules to establish perimeters and create new segments can reduce future administration efforts. Examples of criteria include the following:
- Trust Level: external public segment, staff segment, server segment, database segment, suppliers segment
- Organizational Unit: HR, Sales, Customer Service
- Combinations: external public access to Sales and Customer Service
- Use of physical and logical segmentation: Depending upon the risk level indicated in the risk assessment, it may be necessary to use physically separated infrastructures to protect the organization’s information and assets (for example top-secret data flowing through a fiber dedicated to management staff), or you can use solutions based on logical segmentation like Virtual Private Network (VPN).
- Access rules for traffic flowing: Traffic between segments, including those of allowed external parties, should be controlled according to the need to transmit/receive information. Gateways, like firewalls and routers, should be configured based on information classification and risk assessment. A specific case of access control applies to wireless networks, since they have poor perimeter definition. The recommendation is to treat wireless communication as an external connection until the traffic can reach a proper wired gateway before granting access to internal network segments.
The USP matrix can be customized to include any zones required by your specific network design, following the ISO 27001 recommendations.
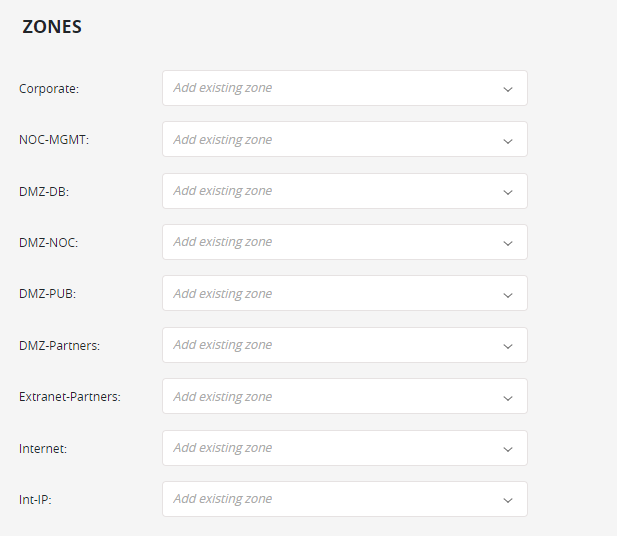
The ISO 27001 compliance zones are:
- NOC-MGMT: Network for general IT security management tools interface (GUI)
- Corporate: Internal corporate network
- DMZ-DB: Network for back-end database servers
- DMZ-NOC: Network for network operations center tools, such as SNMP monitoring, jump servers
- DMZ-PUB: Network for servers that have connections allowed from public networks (e.g. Internet)
- Extranet-Partners: Network dedicated for business partner access
- DMZ-Partners: network for storage of partners data
- Int-IP: Network holding the company Intellectual Property (for example, source code)
- Internet
Create a USP that implements ISO 27001 section A.8.22
Before you create this USP, make sure all the required compliance zones have been created (see Network Zones).
- From the menu, go to Browser
 > USP Viewer.
> USP Viewer. - Click +ADD UNIFIED SECURITY POLICY.
-
Select ISO 27001 from the menu. The zones required for ISO 27001 appear.
-
For each required zone displayed, select the appropriate compliance zone.
-
(optional) Enter the USP description.
-
Click Create.
The ISO 27001 USP has now been created. You can click on the card to view the matrix in the USP Builder and modify the policy as needed.
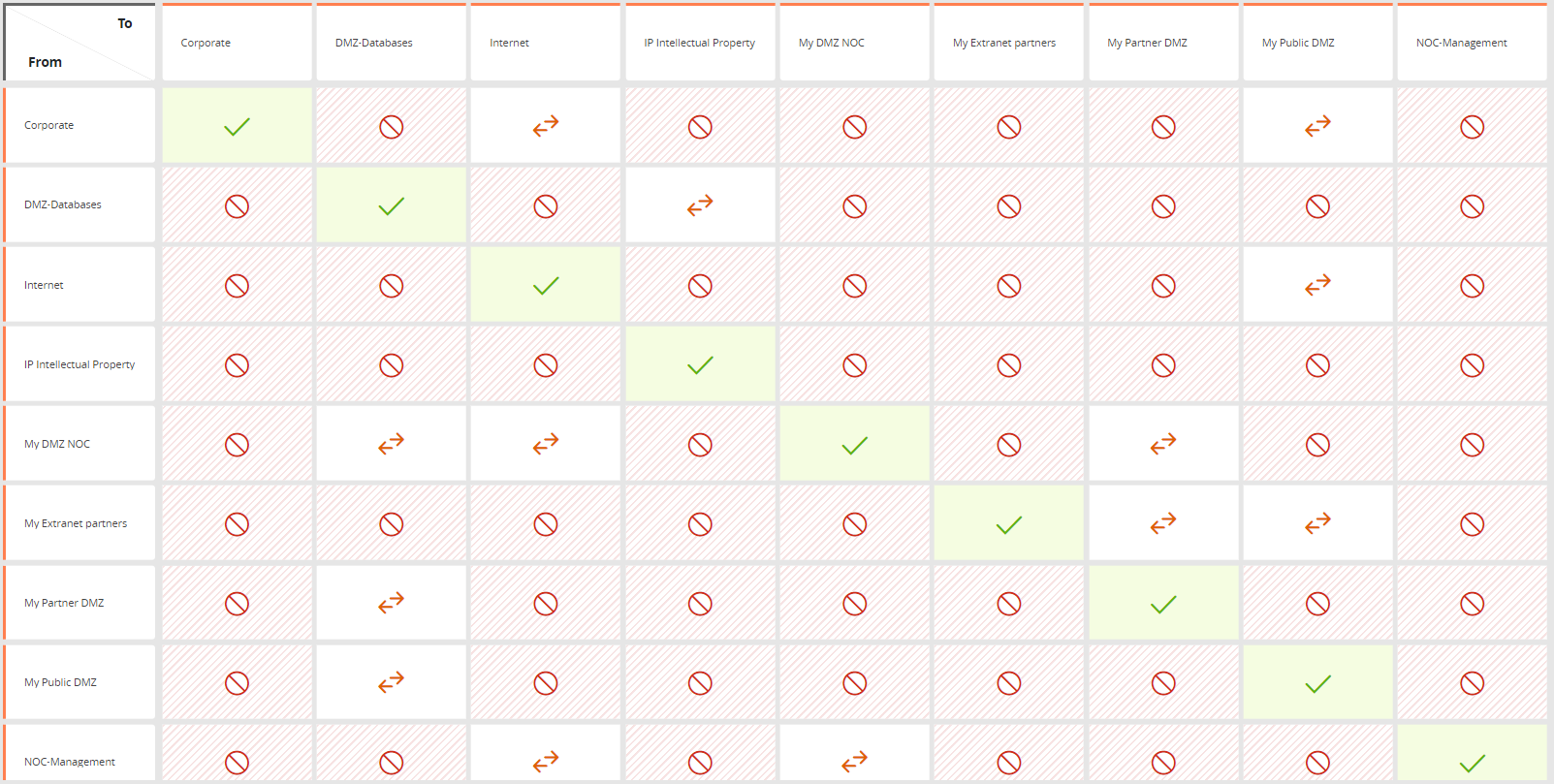
The Corporate Security Policies (CSPs) implemented in this USP include the following:
- CSP 1.1: Traffic from the Internet to internal networks is not permitted.
- CSP 1.2: Traffic from the Internet is only permitted to the public DMZ (DMZ-PUB), and is restricted to web and email via standard ports.
- CSP 1.3: Traffic from the partners (Extranet-Partners) is only permitted to the partner DMZ (DMZ-Partners) and public DMZ (DMZ-PUB), and is restricted to web and email via standard ports.
- CSP 1.4: Traffic from IT network (NOC-MGMT) is only permitted to DMZ-NOC and Internet, and is restricted to approved management traffic only.
- CSP 1.5: Traffic from DMZ-PUB to DMZ-DB is permitted, and is restricted to SQL only.
- CSP 1.6: Traffic from DMZ-NOC to DMZ-DB and Internet is permitted, without any restrictions.
- CSP 1.7: Traffic from DMZ-NOC to DMZ-Partners is permitted, and is restricted to encrypted management traffic only.
- CSP 1.8: Traffic from DMZ-DB to Int-IP is permitted, and is restricted to SQL only.
- CSP 1.9: Traffic from DMZ-Partners to DMZ-DB is permitted, and is restricted to SQL only.
- CSP 1.10: Traffic from corporate to DMZ-PUB is permitted, and is restricted to web and email via standard ports.
- CSP 1.11: Traffic from corporate to Internet is permitted, without any restrictions.
- CSP 1.12: Traffic from Int-IP to anywhere is blocked.
- CSP 2.1: Logging must be enabled for traffic allowed into the following zones: DMZ-DB, DMZ-NOC, DMZ Partners.
- CSP 2.2: Logging must be enabled for all traffic into Int-IP.
- CSP 2.3: 'ANY' may not be used in the source, destination or service when access is granted into the following zones: DMZ-DB, DMZ-NOC, DMZ Partners.
The blocked services and protocols based on the CSPs are:
|
From Zone |
To Zone |
Details |
Corporate Security Policy |
Services Checked |
|---|---|---|---|---|
|
Corporate |
DMZ-PUB |
Restrict access to web and email using the standard ports. |
CSP 1.10 |
http;https;tcp 110;smtp;imap |
|
Corporate |
Internet |
Traffic is not restricted. |
CSP 1.11 |
All access requests must have an explicit source, destination, and service |
|
DMZ-DB |
Int-IP |
Restrict access to SQL only. |
CSP 1.8, CSP 2.2 |
tcp 1433;udp 1434;tcp 1434;tcp 4022;tcp 1443;tcp 1025-65535 |
|
DMZ-NOC |
DMZ-DB |
All network traffic is allowed. Logging must be enabled. |
CSP 1.6, CSP 2.1, CSP 2.3 |
Any All access requests must have an explicit source, destination, and service |
|
DMZ-NOC |
DMZ-Partners |
Restricted to encrypted management traffic only. Logging must be enabled. |
CSP 1.7, CSP 2.1, CSP 2.3 |
tcp 22;tcp 443 |
|
DMZ-NOC |
Internet |
All network traffic is allowed. Logging must be enabled. |
CSP 1.6, CSP 2.1, CSP 2.3 |
Any All access requests must have an explicit source, destination, and service |
|
DMZ-Partners |
DMZ-DB |
Restrict access to SQL only. Logging must be enabled. |
CSP 1.9, CSP 2.1 |
tcp 1433;udp 1434;tcp 1434;tcp 4022;tcp 1443;tcp 1025-65535 |
|
DMZ-PUB |
DMZ-DB |
Restrict access to SQL only. Logging must be enabled. |
CSP 1.5, CSP 2.1, CSP 2.3 |
tcp 1433;udp 1434;tcp 1434;tcp 4022;tcp 1443;tcp 1025-65535 |
|
Extranet-Partners |
DMZ-Partners |
Restrict access to web and email using the standard ports. Logging must be enabled. |
CSP 1.3, CSP 2.1, CSP 2.3 |
http;https;tcp 110;smtp;imap |
|
Extranet-Partners |
DMZ-PUB |
Restrict access to web and email using the standard ports. |
CSP 1.3 |
http;https;tcp 110;smtp;imap |
|
Int-IP |
Any |
No outbound traffic allowed because this zone contains sensitive corporate intellectual property. |
CSP 1.12 |
All traffic must be blocked |
|
Internet |
DMZ-PUB |
Restrict access to web and email using the standard ports. |
CSP 1.2 |
http;https;tcp 110;smtp;imap |
|
Internet |
Corporate, DMZ-DB, DMZ-NOC, DMZ-Partners, Extranet-Partners, Int-IP, NOC-MGMT |
Traffic from the Internet to internal networks is not permitted |
CSP 1.1, CSP 2.1, CSP 2.3 |
All traffic must be blocked |
|
NOC-MGMT |
DMZ-NOC |
Restrict access to only approved management protocols. |
CSP 1.4, CSP 2.1, CSP 2.3 |
tcp 161;tcp 162;tcp 10161;tcp 10162;udp 161;udp 162;udp 10161;udp 10162 |
|
NOC-MGMT |
Internet |
Restrict access to web and email using the standard ports. |
CSP 1.4 |
http;https;tcp 110;smtp;imap |
ISO 27001 Requirements
Tufin Orchestration Suite directly helps enforce the following ISO 27001 controls:
A.8.32 Change Management
|
Requirement |
|
Tufin Orchestration Suite Implementation |
|---|---|---|
|
A.8.32 |
Change management: Changes to information processing facilities and information systems shall be subject to change management procedures. |
SecureChange implements workflow change automation that utilizes risk analysis to prevent unauthorized or risky device policy changes. |
A.8.22 Segregation of Networks
|
Requirement |
|
Tufin Orchestration Suite Implementation |
|---|---|---|
|
A.8.22 |
Segregation in networks: Groups of information services, users, and information systems shall be segregated in the organization's networks. |
Tufin helps you manage network segmentations, and identify and prevent connectivity and compliance violations. The SecureTrack dashboard gives on-going visibility of USP compliance status, as well as identifying the security gaps in your device policies. |