On This Page
Implement NERC CIP v5 Using USP
You can implement NERC CIP v5 compliance that is tailored to your specific business requirements and network topology using a Unified Security Policy (USP). View compliance reports from the violations dashboard at any time, and verify compliance with each specific regulation. If a regulation is not in compliance, identify the specific device and rule that is causing the violation.
Overview
To implement best practices or the compliance regulations of a standard, you need to create a USP Matrix containing the compliance zones required by the standard. The compliance zones are placeholder zones into which you place your network zones, using SecureTrack zone hierarchies. Your existing zones can then be collected into these compliance zones, to ensure compliance monitoring of your entire network. To ensure that you maintain ongoing compliance as your network topology evolves, we recommend that you periodically review the hierarchy of your compliance zones.
NERC zones of protection are unique to each company, and vary based on their specific critical cyber asset structure and segmentation. The granularity of the connections between the zones of protection, internal networks, and the internet will also vary by company.
The NERC CIP compliance zones are:
- EACMS - Network for managing cyber assets that perform electronic access control or electronic access monitoring of the Electronic Security Perimeter(s) or BES Cyber Systems
- PACS - Network for managing physical access control systems, such as motion sensors, electronic lock control mechanisms, and badge readers
- Control Center - Network for managing the NERC assets
- Substation - Network for managing smaller generators that are not co-located with the control center
- Corporate - Internal corporate network
- DMZ
- Internet
Create the USP
To create a Unified Security Policy that implements NERC CIP v5:
Before you create this USP, make sure all the required compliance zones have been created (see Network Zones).
- From the menu, go to Browser
 > USP Viewer.
> USP Viewer. - Click +ADD UNIFIED SECURITY POLICY.
-
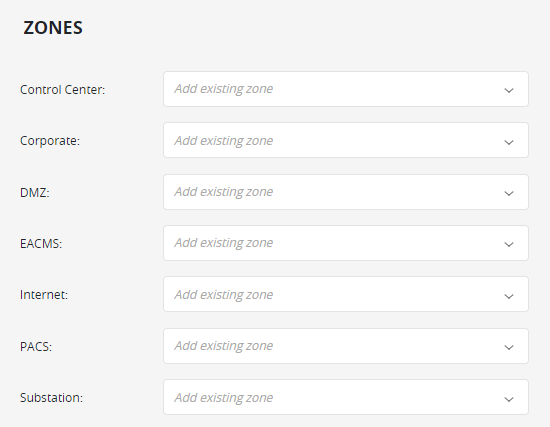
Select NERC CIP from the menu. The zones required for NERC CIP appear.
-
For each required zone displayed, select the appropriate compliance zone.
-
(optional) Enter the USP description.
-
Click Create.
The NERC CIP USP has now been created. You can click on the card to view the matrix in the USP Builder and modify the policy as needed.
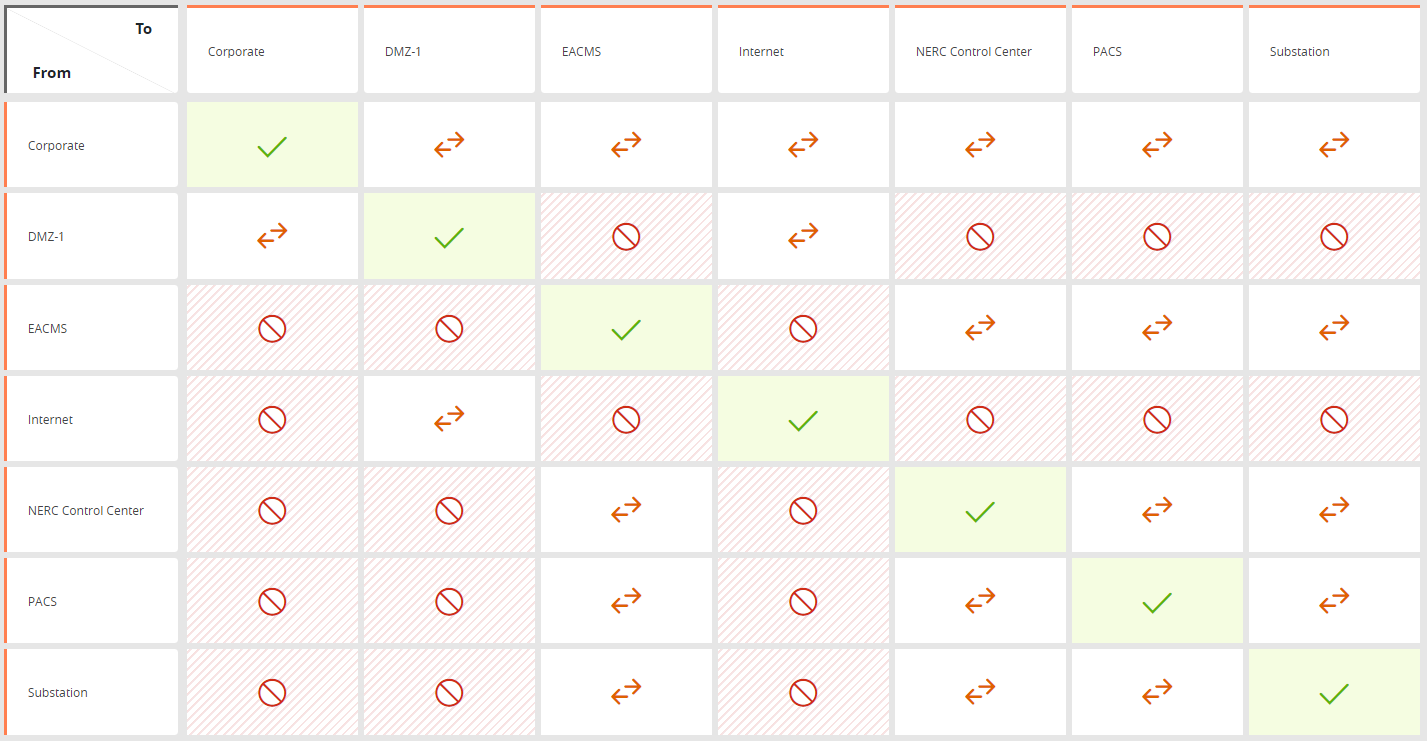
The following requirements are defined in the USP matrix:
|
Source / Destination |
EACMS |
PACS |
Control Center |
Substation |
Corporate |
DMZ |
Internet |
|
EACMS |
|
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2, CIP 7 R1.1
|
|
PACS |
CIP 5 R1.5 CIP 5 R1.1 |
|
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2, CIP 7 R1.1
|
|
Control Center |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
|
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2, CIP 7 R1.1
|
|
Substation |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
CIP 5 R1.5 CIP 5 R1.1 |
|
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2, CIP 7 R1.1
|
|
Corporate |
CIP 5 R2.1
|
CIP 5 R2.1
|
CIP 5 R2.1
|
CIP 5 R2.1
|
|
Best Practice
|
Best Practice
|
|
DMZ |
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2
|
CIP 5 R1.2
|
Best Practice
|
|
Best Practice
|
|
Internet |
CIP 5 R1.2, CIP 7 R1.1
|
CIP 5 R1.2, CIP 7 R1.1
|
CIP 5 R1.2, CIP 7 R1.1
|
CIP 5 R1.2, CIP 7 R1.1
|
Best Practice
|
Best Practice
|
|
NERC CIP regulation 005-5 Rule 1.5 (ANY not allowed in source or destination) and Rule 1.1 (comments in all rules, Last hit < 90) applies to all cells in the matrix.
NERC CIP v5 Regulations
CIP-005-5 Table R1 – Electronic Security Perimeter
|
Requirement |
Unified Security Policy Implementation |
|
|
1.1 |
All applicable Cyber Assets connected to a network via a routable protocol shall reside within a defined ESP. |
All rules related to a NERC zone must comply with the following requirements:
|
|
1.2 |
All External Routable Connectivity must be routed through an identified Electronic Access Point (EAP). |
|
|
1.3 |
Require inbound and outbound access permissions, including the reason for granting access, and deny all other access by default. |
|
|
1.5 |
Have one or more methods for detecting known or suspected malicious communications for both inbound and outbound communications. |
Configure the matrix to deny access to the cyber assets in the NERC zones to all traffic that has ANY as a source, destination, or service. Services not explicitly identified will be denied when the access type is restricted. |
CIP-005-5 Table R2 – Interactive Remote Access Management
|
Requirement |
Unified Security Policy Implementation |
|
|
2.1 |
Utilize an Intermediate System such that the Cyber Asset initiating Interactive Remote Access does not directly access an applicable Cyber Asset. |
Configure the matrix to allow only the designated intermediate systems to the cyber assets in the NERC zones using the access type restricted. |
CIP-007-5 Table R1– Ports and Services
|
Requirement |
Unified Security Policy Implementation |
|
|
1.1 |
Where technically feasible, enable only logical network accessible ports that have been determined to be needed by the Responsible Entity, including port ranges or services where needed to handle dynamic ports. If a device has no provision for disabling or restricting logical ports on the device then those ports that are open are deemed needed. |
Configure the matrix to deny access to the cyber assets in the NERC zones from the internet using the access type blocked |