On This Page
Implementing NIST 800-53 Using USP
You can implement NIST 800-53 regulation compliance that is tailored to your specific business requirements and network topology using a Unified Security Policy (USP). View compliance reports from the violations browser at any time, and verify compliance with each specific regulation. If a regulation is not in compliance, identify the specific device and rule that is causing the violation.
Overview
To implement best practices or the compliance regulations of a standard, you need to create a USP Matrix containing the compliance zones required by the standard. The compliance zones are placeholder zones into which you place your network zones, using SecureTrack zone hierarchies. Your existing zones can then be collected into these compliance zones, to ensure compliance monitoring of your entire network. To ensure that you maintain ongoing compliance as your network topology evolves, we recommend that you periodically review the hierarchy of your compliance zones.
The required NIST 800-53 compliance zones are:
- Corporate
- DMZ
- Internet
- Database
- Wireless Network
- Admin Network
- Application
- Users Network
- VoIP
Create the USP
To create a Unified Security Policy that implements NIST 800-53:
Before you create this USP, make sure all the required compliance zones have been created (see Network Zones).
- From the menu, go to Browser
 > USP Viewer.
> USP Viewer. - Click +ADD UNIFIED SECURITY POLICY.
-
Select NIST 800-53 from the menu. The zones required for NIST 800-53 appear.
-
For each required zone displayed, select the appropriate compliance zone.
-
(optional) Enter the USP description.
-
Click Create.
The NIST 800-53 USP has now been created. You can click on the card to view the matrix in the USP Builder and modify the policy as needed.
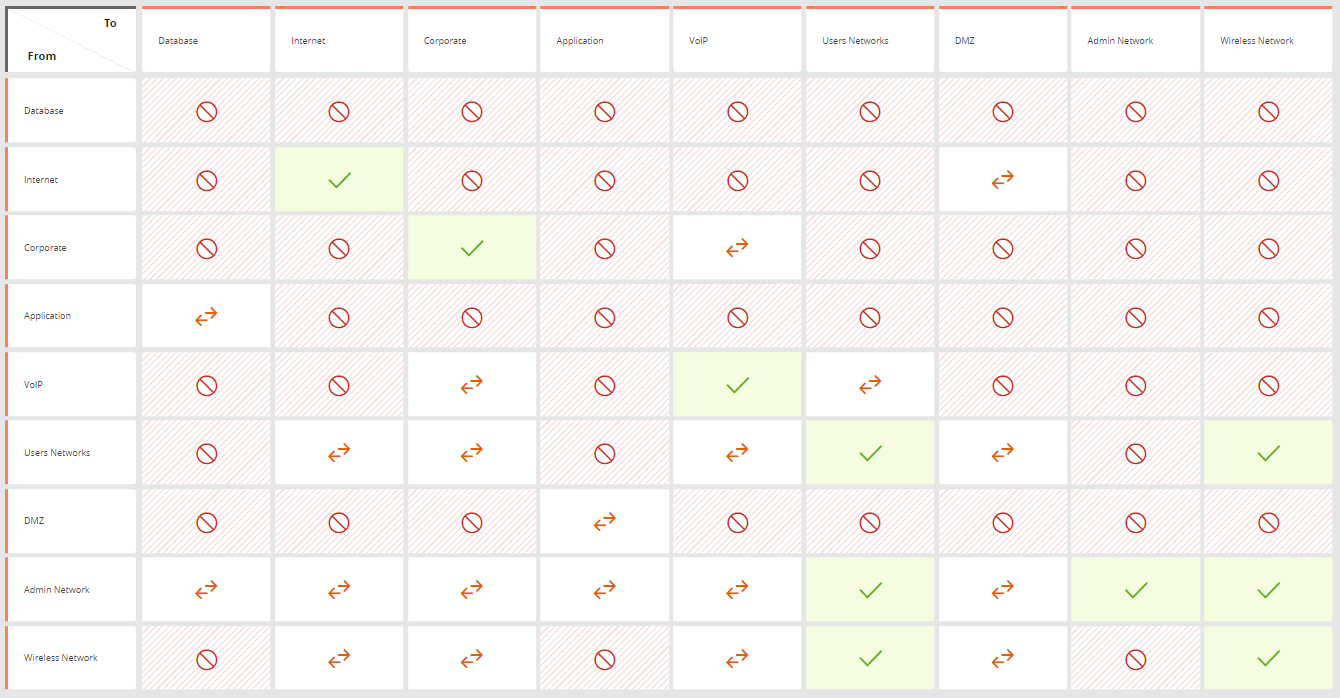
The following requirements are defined in the USP matrix:
|
Source / Destination |
Admin Network |
Application |
Corporate |
Database |
DMZ |
Internet |
Users Networks |
VoIP |
Wireless Networks |
|
Admin Network |
Allow All |
Block all |
Block all |
Block all |
Block all |
Block all |
Block all |
Block all |
Block all |
|
Application |
Allow only RDP |
Block all |
Block all |
Block all |
Allow only TCP 8080 |
Block all |
Block all |
Block all |
Block all |
|
Corporate |
Allow only
RDP |
Block all |
Block all |
Block all |
Block all |
Block all |
Allow only ssh |
Allow only
tcp 53 |
Allow only
tcp 53 |
|
Database |
Allow only
ssh
RDP |
Allow only tcp 1433 |
Block all |
Block all |
Block all |
Block all |
Block all |
Block all |
Block all |
|
DMZ |
Allow only ssh |
Block all |
Block all |
Block all |
Block all |
Allow only tcp 80
|
Allow only tcp 80
|
Block all |
Allow only tcp 80
|
|
Internet |
Allow only
tcp 80 |
Block all |
Block all |
Block all |
Block all |
Allow all |
Allow only tcp 80
|
Block all |
Allow only tcp 80
|
|
Users Networks |
Allow all |
Block all |
Block all |
Block all |
Block all |
Block all |
Allow all |
Allow only
tcp 5060 |
Allow all |
|
VoIP |
Allow only
tcp 5060 |
Block all |
Allow only
tcp 5060 |
Block all |
Block all |
Block all |
Allow only
tcp 5060 |
Allow all |
Allow only
tcp 5060 |
|
Wireless Networks |
Allow all |
Block all |
Block all |
Block all |
Block all |
Block all |
Allow all |
Block all |
Allow all |