On This Page
Path Analysis
Overview
The path analysis feature allows you to investigate whether there is a path between selected sources and destinations, and which devices exist in the path which may block specific traffic. You can investigate a path based on specific services such as HTTP or SSH.
You can drill down to see details of the path such as the routes, interfaces, and matching policy rules of each device in a path. For physical devices, this allows you to see all devices in the path and the relevant routing information for the devices. For cloud platforms, you can analyze the virtual private clouds or networks to make sure that they are connected.
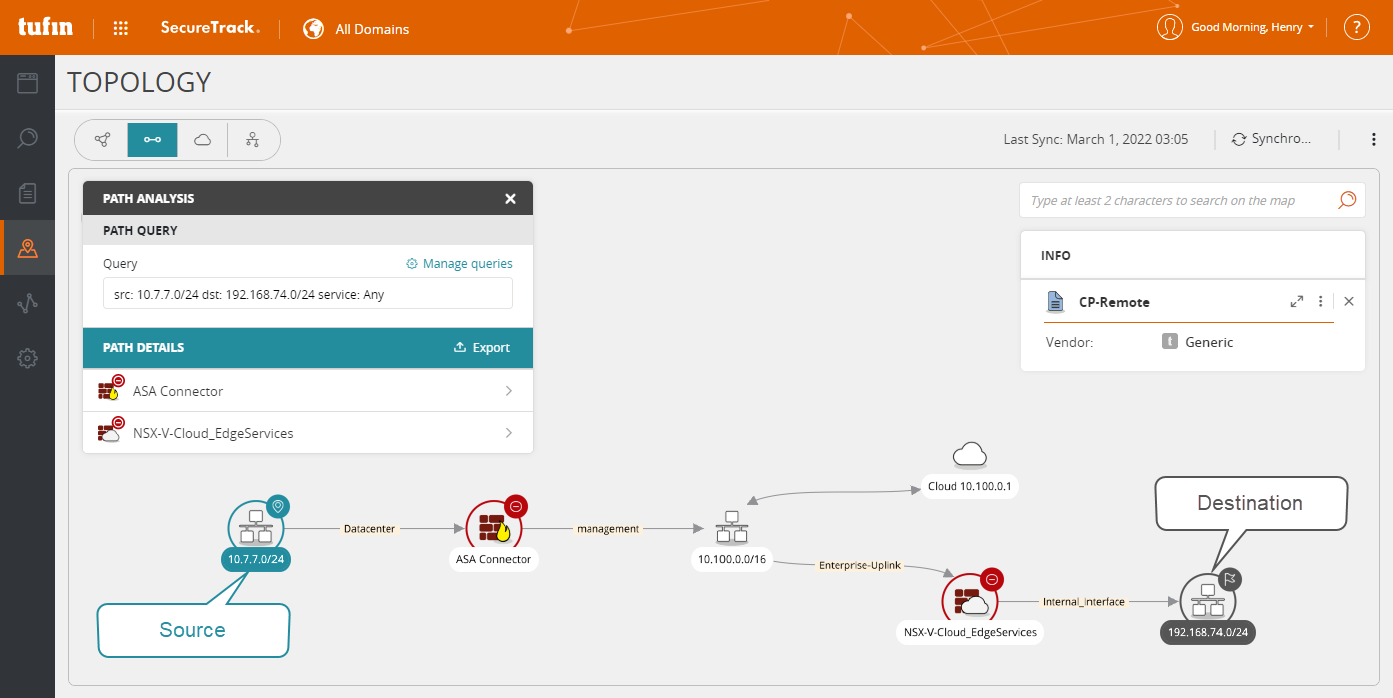
In the following example, path analysis identified the most direct route from the Source device 10.7.7.0/24 (identified with 

The map shows the selected path in the order of the minimum distance (least number of hops) from any source to any destination. Devices with an equal distance between the source and destination are listed in alphabetical order.
Path Analysis Icons
The icons on a path analysis map are:
|
Icon |
Meaning |
Description |
|---|---|---|

|
Start point | First element that SecureTrack can identify in each path. If the start point is not in an identified network, SecureTrack shows the start point in a cloud. |

|
Routes traffic | Device that allows traffic. |

|
Drops traffic | Device includes a rule that blocks traffic. |

|
Incomplete path | Source traffic goes to this point, but does not reach the destination. |

|
End point | Last element that SecureTrack can identify in each path. If the next device in the path is an unmonitored device, SecureTrack shows the end point in a cloud. |
|
|
Directional arrow |
Direction of the modeled traffic (Traffic can also be bidirectional) |
If there is an incomplete path, the devices with missing routing data are colored black.
What Can I Do Here?
Run a Path Query
-
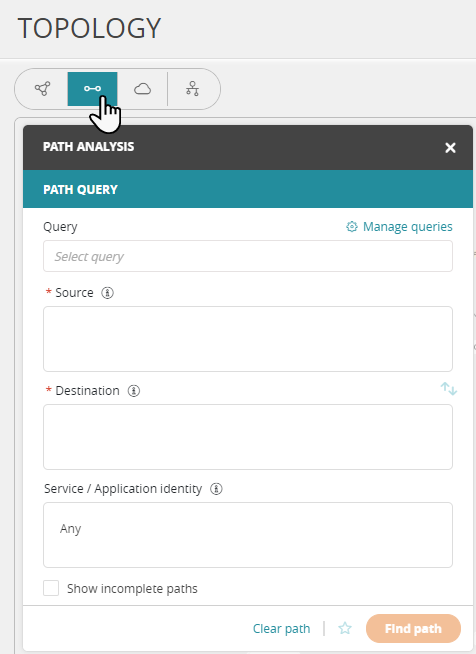
On the map, click
 . The Path Analysis panel appears.
. The Path Analysis panel appears. -
Enter one or more Sources and Destinations using any of the following methods:
-
Select a saved query and run it.
-
Right-click on a device on the map and select Add to Source or Add to Destination.
-
Type the first few letters of the host, subnet, IP range, LDAP users, or group name and select the device from the auto-filled list.
-
IPv4 addresses are supported for all devices; and IPv6 is supported for specific devices. See SecureTrack Features by Vendor.
-
For Palo Alto Panorama devices, enter a non-default port for applications by entering the port name in brackets, multiple ports should be separated with a comma, for example
Facebook(TCP 100, TCP 101, HTTP). -
To enter a user group, type user.name in front of the group. For example: user.name/QA-devices.
-
From R24-1 path queries for Check Point targets will no longer be able to contain LDAP and other object types together in the same source field. Instead, you must create separate queries for each source type. -
-
(Optional) In the Service / Application identity field, enter (lowercase) services / application identities (see predefined services, predefined application identities).
-
Click Find Path.
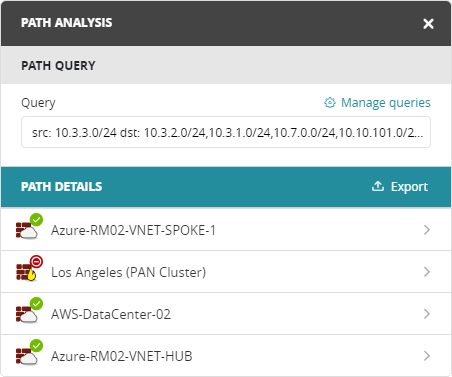
The Path Analysis panel displays devices in the path between the source and destination.
You can click on a device to see details, including the incoming interfaces (for cloud, coming from) and the next devices (for cloud, going to).
(Note that running this command changes the default setting by suppressing the map every time you open the Map page.)
From R23-2 PHF3:
From R24-1 PHF1 and later:
To view the map, click Load Map.
Search capabilities are unavailable when the map is suppressed.
To restore map behavior use these commands:
From R23-2 PHF3:
From R24-1 PHF1 and later:
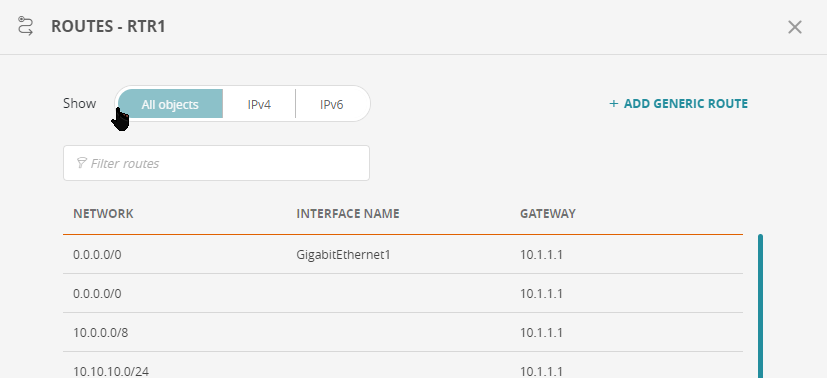
Show Routes For a Monitored Device
-
Run a path query.
-
Right click on a monitored device and select Show routes. The routes window appears.
-
To filter the list, select All objects, IPv4 or IPv6, or enter text in the field Filter routes
-
To add a generic route, click on + ADD GENERIC ROUTE.
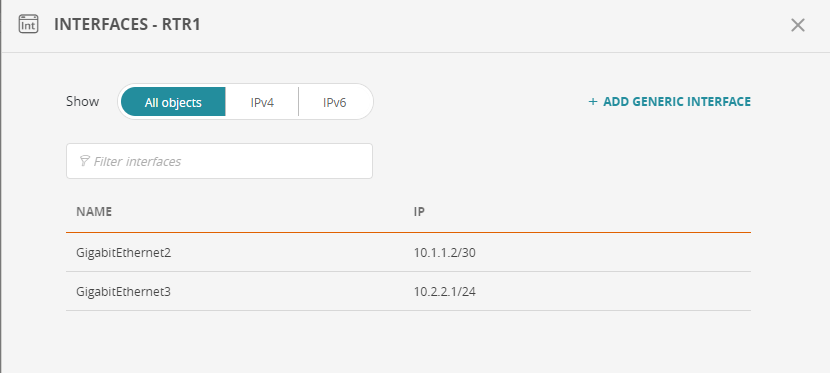
Show Interfaces of a Monitored Device
-
Run a path query.
-
Right click on a monitored device and select Show interfaces. The interfaces window appears.
-
To filter the list, select All objects, IPv4 or IPv6, or enter text in the field Filter interfaces
-
To add a generic interface, click on + ADD GENERIC INTERFACE.
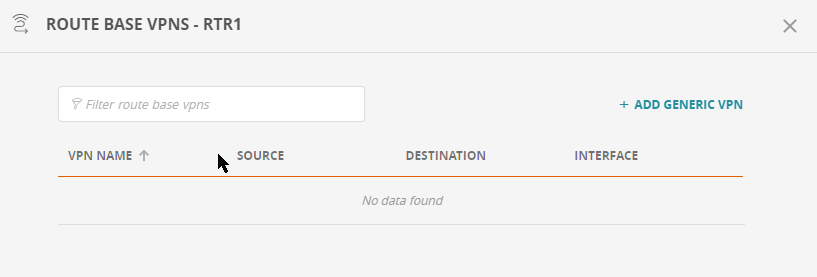
Show Route-Base VPNs for a Monitored Device
-
Run a path query.
-
Right click on a monitored device and select Show route-base VPNs. The route-base VPNs window appears.
-
To filter the list, enter text in the field Filter route-base vpns
-
To add a generic VPN, click on + ADD GENERIC VPN.
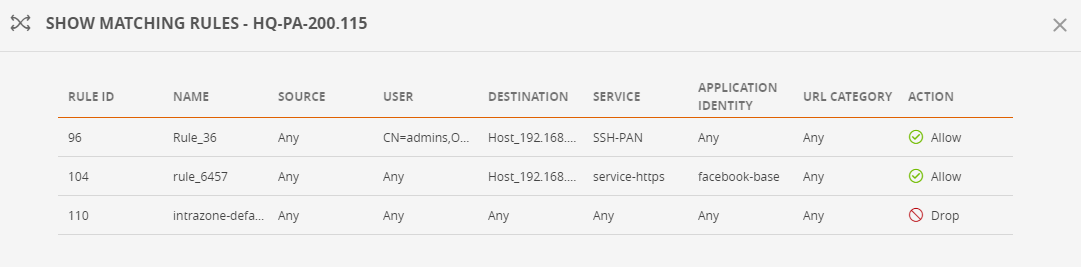
Show Matching Rules for a Monitored Device
-
Run a path query.
-
Right click on a monitored device that blocks traffic, and select Matching rutes. The rules window appears.
All rules that block the traffic are listed.
-
To filter the list, enter text (not available on all device types).
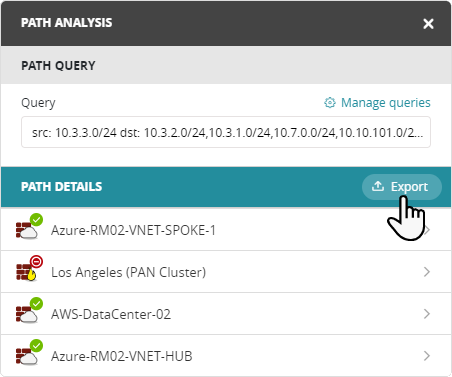
Export Path Report as a PDF File
Click Export next to the search result to generate a PDF report with details of the path, including matching rules, interfaces, and NAT information. If there are multiple paths, you can select which paths to include in the report. The report includes a map of the paths and details of each device in a path.
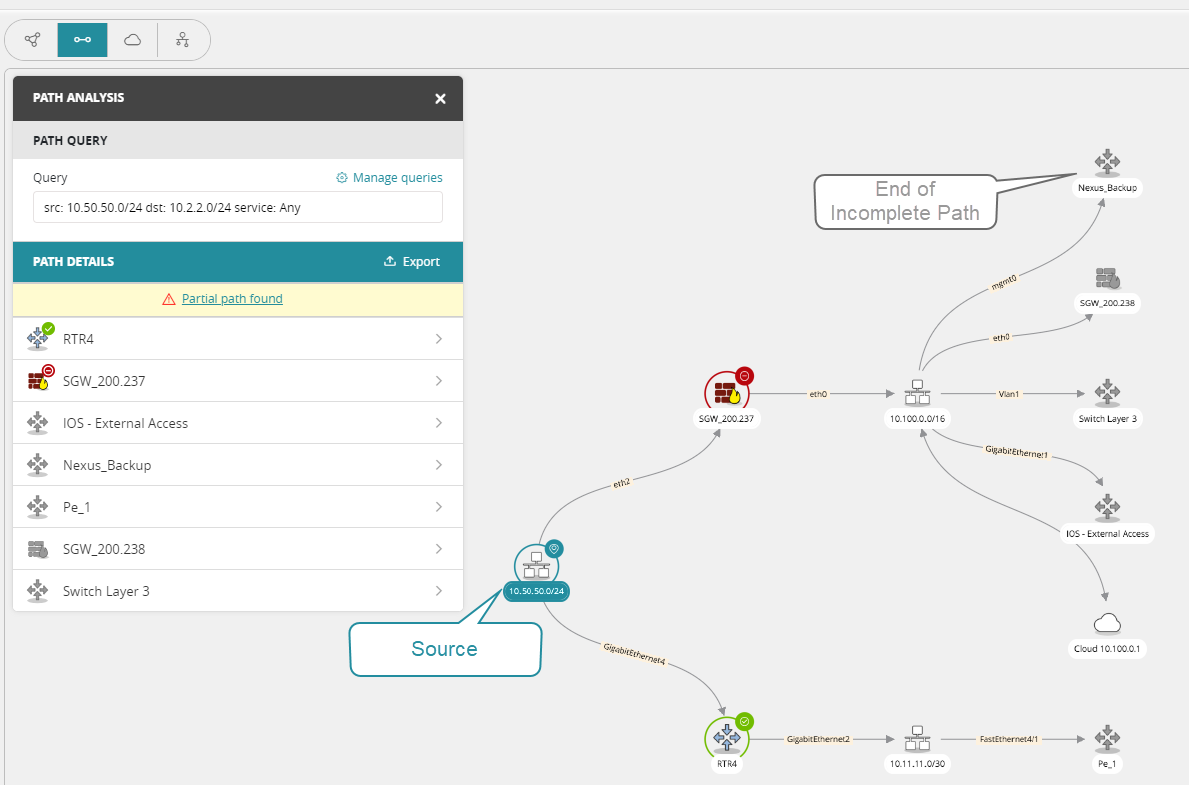
Investigate Incomplete Paths
An incomplete path is where there is no path between the source and destination
If path analysis is unable to identify a path, it give you the option to view an incomplete path which shows devices that the source can reach, but cannot continue to the destination without adjusting the device settings.
The grey items in the following image are connected to the source, which is colored blue, but cannot continue to the destination.
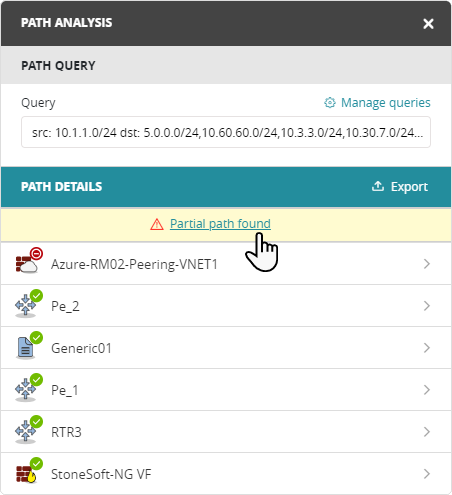
Investigate Partial Paths
A partial path is a path were a source has no path to one or more destinations.
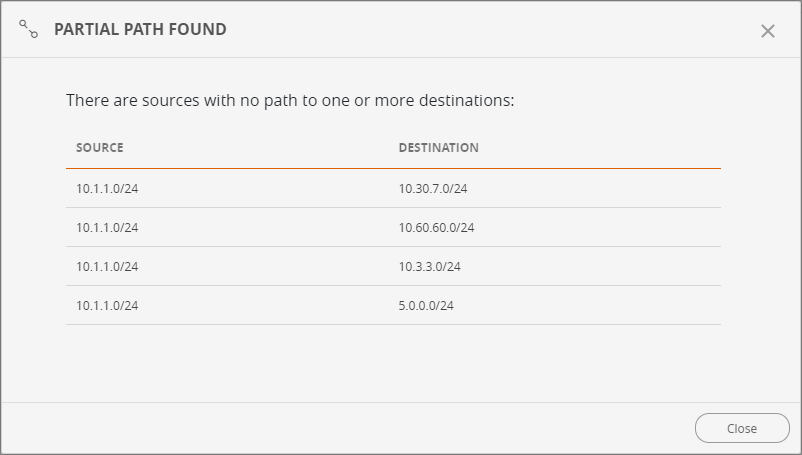
In the Path Analysis panel, click Partial path found to view details of the partial path
SecureTrack displays a list of sources that have no path to one or more destinations:
Save a Query
Click Manage queries to create and manage path queries.
How Do I Get Here?
- In SecureTrack, click Map
 .
. - Click
 .
.