On This Page
Access Request Sections
Overview
|
|
This topic is intended for SecureChange handlers who are responsible for processing change requests. |
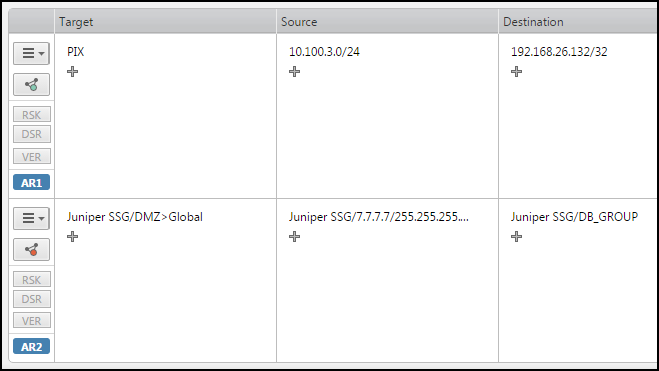
The Access Request field contains these sections: Target, Source, Destination, User (if enabled), Service/Application Identity, Action and Comment
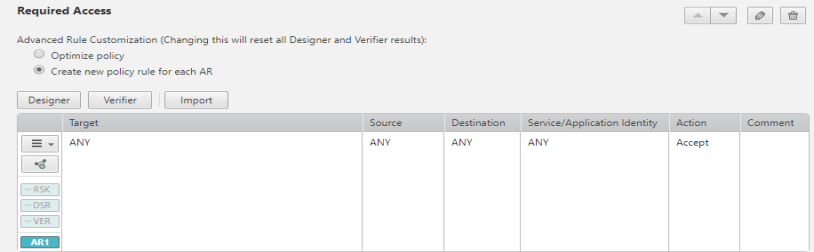
When a request has the Access Request field, you define the target and traffic flow for the request. The source and destination IP addresses are validated when the request ticket is created.
Access Request Options
Click ![]() to access the following additional options:
to access the following additional options:
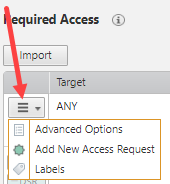
Advanced Options
For more information, see Advanced Options.
Add New Access Request
This option adds another table where the user can define another traffic flow to request.
Delete Access Request
Use this option to remove the traffic flow from the request.
Labels
Use this option to manage labels for the traffic flow.
Access Request Tools
The Access Request field contains the following additional tools. When you run any of these tools, they run on all access requests in the ticket:
Topology
![]() - When topology is enabled, SecureChange finds the devices and subpolicies that are relevant to the access request and lets the Designer suggest firewall changes with the correct IP addresses.
- When topology is enabled, SecureChange finds the devices and subpolicies that are relevant to the access request and lets the Designer suggest firewall changes with the correct IP addresses.
For NAT environments, NAT translations will be accounted for in the calculations.
![]() - When topology is disabled (non topology mode), you must manually choose the devices and subpolicies that are relevant to the access request and specify the correct IP addresses. Designer will calculate the rule changes required on the policies you selected. We recommend using non topology mode when the topology map is not yet fully constructed. Using access requests in topology mode with an incomplete topology may give incorrect results.
- When topology is disabled (non topology mode), you must manually choose the devices and subpolicies that are relevant to the access request and specify the correct IP addresses. Designer will calculate the rule changes required on the policies you selected. We recommend using non topology mode when the topology map is not yet fully constructed. Using access requests in topology mode with an incomplete topology may give incorrect results.
For NAT environments, NAT translations will be accounted for in the calculations. You may need to create one access request with an IP address before NAT and another access request with an IP address after NAT. Risk Analysis - Shows you if the requested access violates corporate security policy configured in SecureTrack.
For an access request with topology mode enabled, if a manually selected target device is not in the path, Designer and Verifier cannot suggest or verify changes.
To reduce the possibility of performance degradation and security issues resulting from implementing wide-ranging change suggestions that may be related to your access request, if you plan to select a target device that is outside the known topology, you must use non topology mode.
Designer
Use this tool to obtain precise recommendations for how to change a rulebase by using topology and current rulebase data in SecureTrack. The tool can also automatically implement these changes for devices where Provisioning is supported.
Verify
Use this tool to check the last policy for the device to make sure that the change is included in the policy.
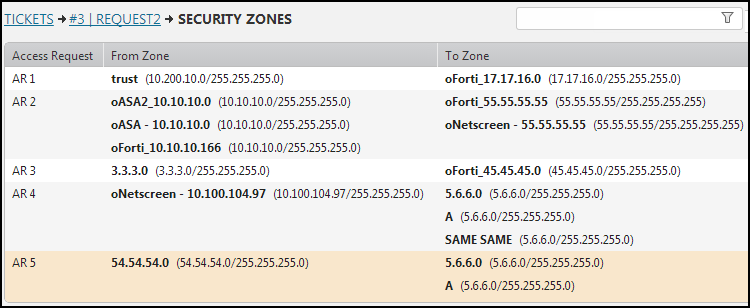
Security Zones
When handling a task containing an Access Request field, you can use the Security Zones tool to retrieve the source and destination security zone information to use for analyzing the request from a security standpoint.
Security Zones are not available when SecureTrack is configured for Multi-Domain deployment.
The automation tools are only available if it is enabled for the step in the workflow configuration before the requester opens the ticket.
To view the security zone information:
- In the Access Request field, click Security Zones:
For each access request, you can see:
- From Zone: Each source zone is listed with the access request's source objects that belong to its zone. The objects are in parentheses.
- To Zone: Each destination zone is listed with the access request's destination objects that belong to its zones. The objects are in parentheses.
Hover over the zone name to see what type of zone it is.