On This Page
Configuring User Identity
Overview
For supported devices only, the User Identity feature is available by configuring LDAP. User groups are validated from the Domain DN (Base DN) tree of the LDAP server.
Some additional LDAP customizations are possible. Contact Tufin Support for assistance.
Prerequisites
If you require a LDAP generated certificate, you should retrieve the certificate before configuring the user identity and open the certificate in a text editor. The certificate is in the following format:
-----BEGIN CERTIFICATE----- MIIFLDCCBBSgAwIBAgIkAhwR/6TVLmdRY6hHxvUFWc0+Enmu/Hu6cj+G2FIdAgID aFXCMA0GCSqGSIb3DQEBBQUAMBYxFDASBgNVBAMMC3dpbGxla2UuY29tMB4XDTA5 .... .... -----END CERTIFICATE-----
Configure User Identity
-
Select Admin
 > User Identity
> User Identity -
Select Configure LDAP for User Identity:
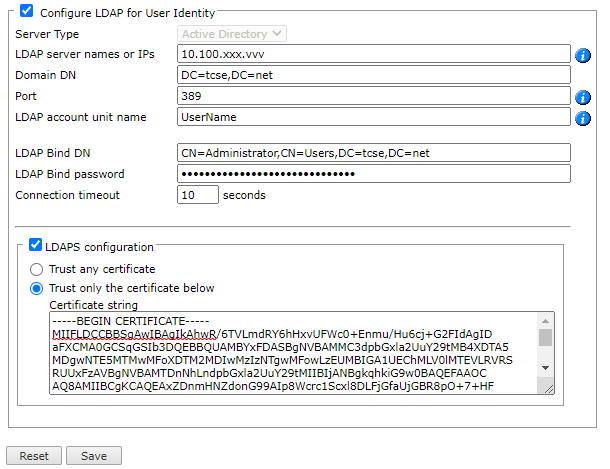
-
Configure the following fields:
The only supported RDNs for DN fields are: CN, OU, and DC. Do not use other RDNs.-
Server Type: SecureTrack currently supports Active Directory.
-
LDAP server names or IPs: Resolvable hostname or address of the Active Directory server.
When you use LDAP over SSL, enter the name the value from the 'Issued To' field of the server certificate.
For LDAP server redundancy, enter multiple server names or IP addresses separated by a space or a comma.
-
Domain DN:: The domain's Distinguished Name (also known as Base DN). You cannot use the DN "root".
-
The Port used by Active Directory, according to the following table:
Active Directory Configuration
Regular LDAP (no SSL)
Encrypted LDAP (SSL)
Standalone
389
636
Global Catalog
3268
3269
-
LDAP account unit name: For Check Point devices, the LDAP account must be set. Enter the LDAP account unit name configured in the MDA/CMA/SMC.
-
LDAP Bind DN: LDAP user that has permission to read all LDAP objects and attributes that exist in the LDAP base DN.
This field must contain a value.
- LDAP Bind password: Password of the LDAP Bind DN.
- Connection timeout: The number of seconds that the authenticated connection is available before it must re-authenticate.
-
-
For LDAP over SSL, select LDAPS configuration and select one of the following:
-
Trust any certificate: Automatically accept the certificate presented by the Active Directory server, such as a self-signed certificate.
-
Trust only the certificate below: Copy the certificate generated in LDAP and paste it in the Certificate string field.
The certificate starts with
-----BEGIN CERTIFICATE-----
and ends with
-----END CERTIFICATE-----.
-
-
Click Save.
Update the Name of an LDAP Server Field
- See the Tech Note Configure LDAP Vendor Attributes for User Identity.
How Do I Get Here?
In SecureTrack, go to: Admin ![]() > User Identity
> User Identity
