On This Page
Clone Network Object Policy Field
|
|
This topic is intended for SecureChange workflow owners, who are responsible for creating and maintaining workflows. |
When you configure workflow steps, the Clone Network Object Policy field (formerly known as Clone Server Policy) lets you add the access permissions for new servers into your security policy, modeled on an existing server in your security policy. For example, you can add new servers 2.2.2.2 and 3.3.3.3 to your network, which require the exact access permissions defined in your security policy for server 1.1.1.1. The Clone Network Object Policy workflow will add the new servers 2.2.2.2 and 3.3.3.3 to all rules and object groups in your security policy that includes server 1.1.1.1.
See SecureChange Features by Vendor for devices that support this workflow.
Below are some examples where a Clone Network Object Policy workflow can be used:
- Before decommissioning a server, a duplicate server can be added and run in parallel with the server which is to be decommissioned.
- An extension of an existing domain is required due to business needs, for example, the addition of a new domain controller or an extension to the web servers of an application.
- For cloning a network. For example, when a new office-department is added and requires the same network access (mails and LDAP) as other departments.
Implementation Logic
The following examples demonstrate the implementation principles which apply to both hierarchical policies and non-hierarchical policies:
- Designer will always try to reuse an existing object. If a server already exists in an object, Designer will add the additional server(s) to this object rather than create a new object.
- When creating a new object, Designer will always try to add the object at the same location as the existing server.
- Rules containing overriding objects or overriding groups will not be automatically copied to a new policy, avoiding the possibility of an incorrect suggestion. Instead Designer will provide a manual change suggestion for the overriding object which can be implemented by the handler.
Creating a Clone Network Object Policy Field
When you configure the Clone Network Object Policy field in a workflow step, the Field display name and Tooltip text are the same for every step that the field is added to. All other settings apply only to the current step:
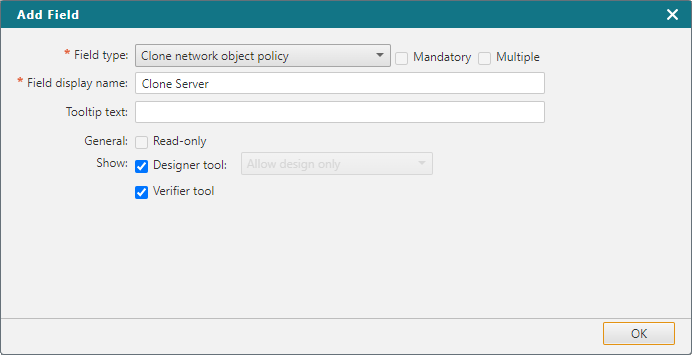
General
- Read-only - The handler of this step can view the contents but not edit values of the field.
Show
-
Designer tool - Lets the handler open the Designer, which gives precise recommendations for editing all matching rules and groups in all the policies of the selected targets.
For each step that you enable the Designer tool, you can allow the handler to:
-
Allow all: Allow all Designer capabilities supported by this workflow.
-
Allow design only: Run the Designer recommendations for policy updates.
-
Allow update only: Provision the Designer recommendations by saving the policy updates to devices. (For devices where Provisioning is supported)
-
Allow commit only: Commit the current policy from the management device onto associated child firewall devices. (For management devices where Committing Changes is supported)
-
Allow design and update only: Perform both design and update processes.
-
Allow update and commit only: Perform both update and commit processes.
-
-
Verifier tool - Lets the handler open the Verification tool, to verify if the requested access can or cannot be validated.
