On This Page
Configuring the Organizational LDAP Settings
To be able to import LDAP users and user groups into SecureChange, SecureChange must be able to communicate with the organizational LDAP server. Microsoft Active Directory and Novell eDirectory are supported as LDAP servers. More than one LDAP server can be configured.
-
Obtain the relevant information from the organizational LDAP administrator.
-
Log into SecureChange, at:
https://<server>/securechangeworkflow -
Go to Settings > LDAP:
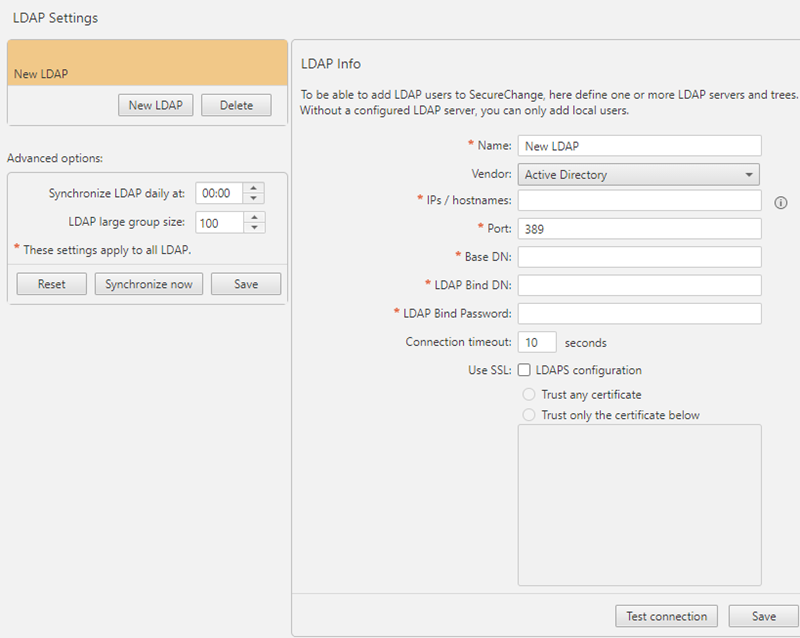
-
Click New LDAP, and configure these settings:
-
Name - A name for this connection
-
Vendor - Select Microsoft Active Directory or Novell eDirectory
-
IPs/hostnames - The IP addresses or resolvable hostnames of the LDAP servers.
If you change the IP address or hostname of the LDAP server, you must click Synchronize now in the Advanced Options in order to update the list of users in SecureChange.
-
Port - Usually 389 for clear connections or 636 for SSL connections
-
Use SSL - Select if the LDAP server uses SSL
-
Base DN - The base DN of the part of the LDAP tree that should be available to SecureChange
An LDAP member who is not located under the Base DN, even if included in a group located under the Base DN, will not be available for workflow configuration and will not be able to log into SecureChange.
All LDAP members under the Base DN, even if not manually added to SecureChange, will have the permissions applied in SecureChange to the Any User group.
-
LDAP Bind DN - LDAP user that has permission to read all LDAP objects and attributes that exist in the LDAP base DN
-
LDAP Bind Password - Password of the LDAP user specified above.
-
Connection timeout - Number of seconds after which SecureChange stops connection attempts to the LDAP server
-
-
To use LDAP over SSL, select Use LDAP over SSL and select one of the following:
-
Trust any certificate - Automatically accept the certificate presented by the Active Directory server, such as a self-signed certificate.
-
Trust only the certificate below - Copy the certificate generated in LDAP and paste it in the Certificate string field.
The certificate starts with
-----BEGIN CERTIFICATE-----
and ends with
-----END CERTIFICATE-----.
-
-
Repeat steps 4 and 5 for each LDAP server you want to configure.
- Click Save.
Users and Groups no longer accessible with the changed LDAP settings (IP/hostname or Base DN) will be removed from SecureChange. Tasks assigned to these users need to be reassigned.
A confirmation message should appear:
You can also set:
- Synchronize LDAP daily at - A specified time for synchronization
- LDAP large group size - The minimum size of groups that SecureChange does not copy into its user database; You can only add these large groups to the first step of a workflow
How Do I Get Here?
SecureChange > ![]() Settings > LDAP
Settings > LDAP
