On This Page
Configuring Zscaler Syslogs
Overview
You must configure your Zscaler environment so that TOS can collect traffic log information.
Prerequisites
Add a Zscaler device to SecureTrack with at least one of the following enabled:
-
Collect traffic logs for rule usage analysis
-
Collect traffic logs for object usage analysis
To adjust the configuration of devices already monitored in SecureTrack, see Configure a Monitored Device > Edit configuration.
Configure Zscaler Syslogs for TOS
In Zscaler, verify that you have a Nanolog Streaming Service (NSS) server that can send TCP syslogs. In the NSS Feed tab, create an NSS feed, and define the following fields, so that TOS can retrieve syslog data from Zscaler:
|
Field |
Value |
|---|---|
|
Feed Name |
Type a name to identify this feed. |
| NSS Type | Select NSS for Firewall. |
|
NSS Server |
Select the NSS Server. |
|
Status |
Select Enabled. |
| SIEM Destination Type | Select IP Address or FQDN. |
| SIEM IP Address | IP address or FQDN for the TOS server. |
| SIEM TCP Port | 601 (by default). You can overwrite this value with the TCP Syslog VIP. See Syslog VIP. |
|
Log Type |
Select Firewall Logs. |
|
Firewall Log Type |
Select Aggregate Logs. |
| Feed Output Type | Select CSV. |
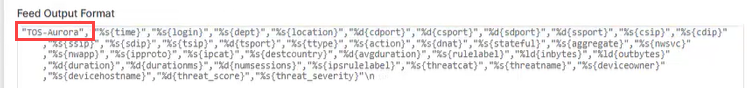
| Feed Output Format |
Edit this format and add a unique identifier. You use this identifier for the Log ID when configuring the Zscaler device. For example: This match insures that TOS will recognize the syslog and analyze it correctly with the relevant Zscaler device. |
| Duplicate Logs | Select Disabled. |
| Firewall & IPS Policy Actions | Select only Allow rules to reduce the amount of traffic sent to TOS. You can add additional filters based on requirements from your organization, but these filters will impact TOS analysis. |
After configuring Zscaler to allow TOS to pull traffic information, you can use TQL queries in the Rule Viewer (timeLastHit) to identify the Last Hit date.