On this page
SecureTrack RADIUS Authentication
Overview
SecureTrack supports RADIUS external authentication of users. To have your users authenticate to SecureTrack with a RADIUS password, you must configure the connection to the RADIUS server. You can enter the details for a primary and a secondary RADIUS server.
RADIUS authentication for SSH users can be enabled in TufinOS, allowing you to add RADIUS authenticated users to TufinOS. This requires that you specify the correct interface IP in /etc/hosts.
See also SecureChange RADIUS Authentication.
Configure SecureTrack to use RADIUS authentication
-
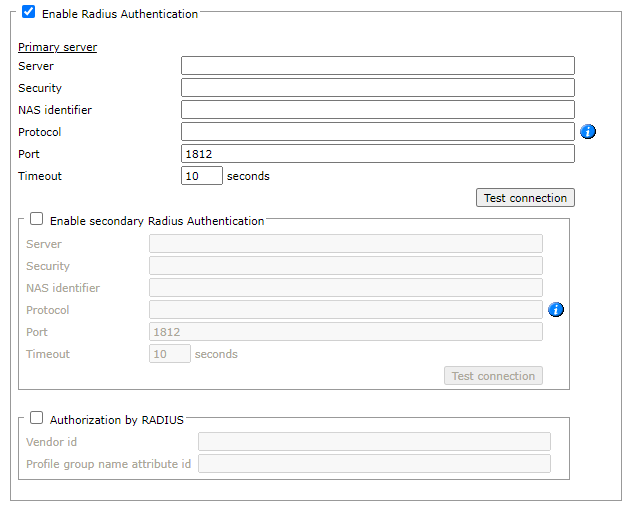
Select Enable RADIUS Authentication:
-
For each RADIUS server in the organization (Primary and Secondary), enter the server details from your organizational RADIUS administrator:
- Server: The resolvable name or IP address of the RADIUS server.
- Security: The password for SecureTrack to access the RADIUS server.
- NAS identifier: Identifier configured on the RADIUS server, which will be included with all user authentication requests. If nothing is entered, SecureTrack will send the NAS-IP-Address attribute containing the node's external IP address.
- Protocol: Enter one of the following supported values: PAP, CHAP, EAPMD5, EAPMSCHAPv2, MSCHAPv1, or MSCHAPv2
- Port: Port number
- Timeout: The number of seconds SecureTrack tries to connect to the RADIUS server before giving up.
- Click Test Connection to make sure that SecureTrack successfully connects to the RADIUS server.
-
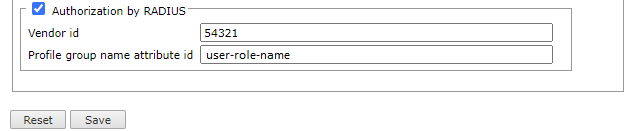
To enable Authorization by RADIUS:
- Check the Authorization by RADIUS box.
-
Configure the Vendor Specific Attribute that specifies the profile group and role of the authenticated user by entering the:
-
Vendor id
-
Profile group name attribute id
- Click Save.
For more information on using RADIUS for authorization, see Add a New Profile Group (for RADIUS users only).
Users that are configured to use RADIUS authentication can login.
How do I get here?
SecureTrack > Admin ![]() > External Authentication > User Servers.
> External Authentication > User Servers.
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague