On This Page
Configuring LDAP (Active Directory) Authentication
SecureTrack supports LDAP external authentication of users, when installed on Red Hat or CentOS Linux, or on TufinOS (Tufin appliance). Microsoft Active Directory 2000, 2003, 2008,2008, 2012, and 2016 are supported. SecureTrack uses TLS 1.2, 1.1, and 1.0 to negotiate SSL/TLS with the LDAPS server for authentication, and uses LDAP version 3 as the protocol to perform administrative binds and retrieve attributes.
To configure SecureTrack to use Active Directory
-
In Active Directory, configure two groups: One for SecureTrack Administrators, and the other for SecureTrack Users.
-
Add the relevant Active Directory users to each group: users who should receive Administrative permissions for SecureTrack - to the Administrators group, and other users - to the Users group.
If you have configured your system for managing multi-domains, users in the SecureTrack Administrators group will initially be Super Administrators; they can subsequently be changed in the Users page to Multi-Domain Administrators. Users in the SecureTrack Users group will initially be Multi-Domain Users; they can subsequently be changed in the Users page to Domain Users.
-
In Settings view, select the Configuration tab.
-
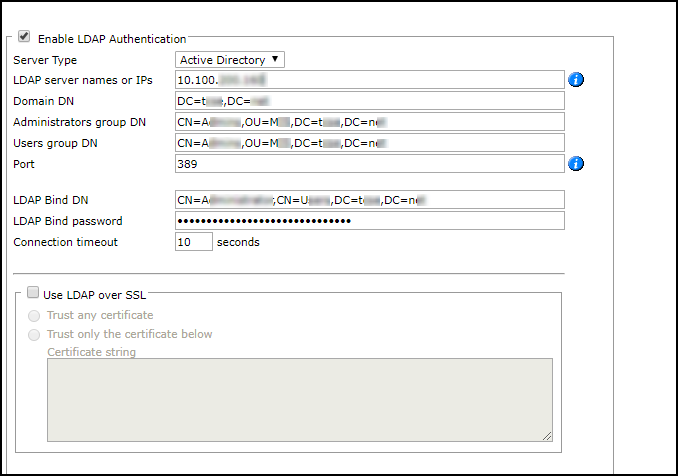
Select External Authentication, and select Enable LDAP Authentication:
-
Configure the following values:
The only supported RDNs for DN fields are: CN, OU, and DC. Do not use other RDNs.-
LDAP server names or IP: Resolvable hostname or address of the Active Directory server.
When you use LDAP over SSL, enter the name the value from the 'Issued To' field of the server certificate.
For LDAP server redundancy, enter multiple server names or IP addresses separated by a space or a comma. -
Domain DN: The domain's Distinguished Name (also known as Base DN). Make sure to use the DN of the desired Domain DN root.
-
Administrators group DN: The Distinguished Name (DN) of the SecureTrack Administrators group on the Active Directory.
-
Users group DN: The Distinguished Name (DN) of the SecureTrack Users group on the Active Directory.
-
The Port used by Active Directory, according to the following table:
Active Directory Configuration
Regular LDAP (no SSL)
Encrypted LDAP (SSL)
Standalone
389
636
Global Catalog
3268
3269
-
LDAP Bind DN: LDAP user that has permission to read all LDAP objects and attributes that exist in the LDAP base DN.
This field should always contain a value.
-
LDAP Bind password: Password of the LDAP Bind DN.
-
Connection timeout: The number of minutes that the authenticated connection is available before it must re-authenticate.
-
-
To use LDAP over SSL, select Use LDAP over SSL and select either:
-
Trust any certificate - Automatically accept the certificate presented by the Active Directory server, such as a self-signed certificate.
-
Trust only the certificate below - In the Certificate string box, paste the public key (certificate) from the Active Directory server.
-
-
Click Save.
When each LDAP user logs in for the first time, SecureTrack automatically generates a matching local user account with default settings according to user type (Domain admin or User) as set by group membership. For Users, default settings include no device permissions. An Administrator (in the Multi-Domain scheme: a Super Administrator) must then assign permissions for the domains.
How Do I Get Here?
In SecureTrack, go to Admin ![]() > External Authentication.
> External Authentication.
