On This Page
Searching in Policy Browser
Overview
Policy Browser lets you search for rules in the device policies according to device and according to policy and policy documentation metadata. You can then view the results and edit the metadata. You can export the results to a PDF or schedule a report of rules in the Rule Documentation Report.
The search applies to the display of rules for all matching devices, so that when you select a different device you only see the rules that match the filter.
Searches in the source and destination fields will return all rules that contain the specified host within contained groups and subnets. For example, searching in the source field for the host 1.1.1.1 will return all rules that have the following the source field:
- 1.1.1.1
- 1.1.1.0/24
- ANY
- a group that contains either 1.1.1.1, 1.1.1.0/24, or ANY
Note the following search limitations:
- IPv6 objects are shown for all devices; use the text search to find IPv6 addresses in the source and destination (IPv6 is not supported for F5)
- If a search match includes an IP address, and the same address is negated in a separate rule, the search results will include the IP address.
- You cannot search for non-continuous IP addresses
Defining a search
-
Select the devices to search in with:
-
Select from dropdown list - Click on the down arrow of the search box to see all available devices, and select the device to search in.
-
Enter text of a device name - You can enter text in the device field to filter the list of devices and select a device.
-
-
Enter the search criteria that defines the rules to show.
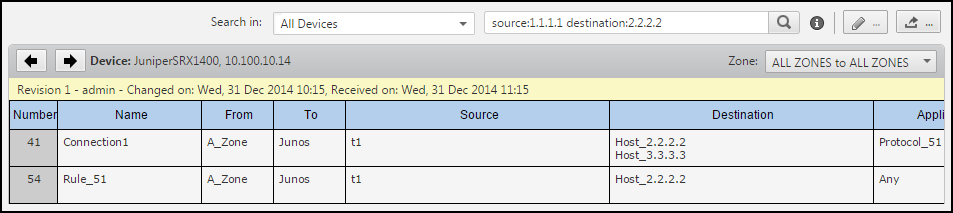
Enter one or more words to search for in rule or metadata details:
-
text1 text2– Returns rules where text1 is found in the rule or metadata fields and text2 is found in the rule or metadata fields. (Not case-sensitive) -
" "– Returns rules with the exact phrase in one of the rule or metadata fields, for example,"web server" -
<fieldname>:<text>– Returns rules with the text in the specified field, for example:source: 192.168.1.1The rule field names are: name, rulenumber, source, destination, log, service, action (reject, deny, drop, refuse, discard; or allow, accept, permit), comment/description, fromzone, tozone, application, user, priority
For Cisco ACI, the name field returns Contracts, the source and destination field returns Consumers or Providers, and the service field returns Filters.
For Palo Alto, the following additional rule field names are available: tags, profile. For Palo Alto Panorama, the tags field also returns rules that contain Dynamic Groups based on Panorama tags in the match criteria.
The metadata field names are: violations, technicalowner, ticketid, businessowner, expirationdate (requires the format: YYYYMMDD), businessowneremail, applicationname, applicationowner, ruledescription, advancedoptions, certificationstatus, certificationdate, certificationexpirationdate
If you specify more than one field in the search, only rules with both field values are shown.
-
<fieldname>.isempty:<true/false>Returns all rules where the specified <fieldname> is empty (true) or filled (false), for example: comment.isempty:trueSupported fields are: advancedoptions, applicationname, applicationowner, businessowner, businessowneremail, comment, expirationdate, log, profile, ruledescription, tags, technicalowner, ticketid, violations, certificationdate, certificationexpirationdate, and certificationstatus
service:<text>– Returns rules with either the name of a service or the protocol/port number of a predefined serviceprotocol:<number>– Returns rules with the specified protocol number (0-255) in the rule serviceport:<number>- Returns rules with the specified port number (0-65535) in the rule serviceRule.isdisabled:<true/false>- Returns all rules that are disabled (true) or are enabled (false)rulelocation:<text>- Returns rules where the rule location field matches (for example,rulelocation: “mydevice”) or contains the specified text (for example,rulelocation:mydevice)shadowed:<true/false>– Returns rules that are shadowed (true) or are not shadowed (false), for example:shadowed:truelasthitgreater:<number>– Returns rules with last hit greater than the specified (non-negative) number of days before the current daylastmodifiedgreater:<number>– Returns rules with last modification date greater than the specified (non-negative) number of days before the current dayapplasthitgreater:<number>– Returns rules where the last hit for an application is greater than the specified number of days before the current day (Click on the rule to see usage information)userlasthitgreater:<number>– Returns rules where the last hit for a user is greater than the specified number of days before the current day (Click on the rule to see usage information)violationcreationdategreater:<date>– Returns rules where the violation creation date is after than the date specified, required format: YYYYMMDD (Click on the rule to see usage information)certificationstatus:<certified/decertified>– Returns all rules where the specified certification status is certified or decertified, for example,certificationstatus:certifiedcertificationstatus.isempty:<true/false>– Returns all rules where the specified certification status is empty (true) or filled (false), for example,certificationstatus.isempty:truecertificationdate:<date>– Returns rules where the certification date is before the specified date, required format: YYYYMMDDcertificationdate.isempty:<true/false>– Returns all rules where the specified certification date is empty (true) or filled (false), for example,certificationdate.isempty:truecertificationexpirationdate:<date>– Returns rules where the certification expiration date is before the specified date, required format: YYYYMMDDcertificationexpirationdate.isempty:<true/false>– Returns all rules where the specified certification expiration date is empty (true) or filled (false), for example,certificationexpirationdate.isempty:true- tags:<text> - Returns all rules that contain the specified text as part of the tag (Not case-sensitive)
-
profile.<profiletype>:<text>– Returns all rules that specify a profile of type <profile type> which contains the specified text in its name (Not case-sensitive)Recognized profile types for <profiletype> are: antivirus, antispyware, vulnerabilityprotection, urlfiltering, datafiltering, fileblocking, wildfireanalysis, securitygroup, logforwarding
Note: If a Security Profile Group contains a profile of type <profiletype> which contains the specified text in its name, then rules containing the Security Profile Group will also be returned.
permissiveness.level:<high/medium/low>– Returns rules with the specified permissiveness level indicating how much traffic is allowed by the rule.inprogressticketid:<number>– Returns all rules that have a ticket in progress (for actions such as Rule Decommission) matching the specified ticket ID, for example,nprogressticketid:769
-
-
