On This Page
Configuring the NSM to Send Syslogs
Syslog traffic must be configured to arrive to SecureTrack from the IP and/or host name of the device.
Syslog proxy is supported for specific devices. For more information on syslog proxy support for supported devices, see Configuring Devices to Send Logs.
Only rules that are marked for logging in the device are included in the syslogs.
To define SecureTrack as a syslog server on the NSM:
- Make sure that the IP address of each Juniper NetScreen device is configured identically on both SecureTrack and on the NSM.
For JunOS devices, you must configure each device to send syslogs directly to SecureTrack.
- Log into the NSM.
-
In the navigation pane, under Action Manager, select Action Parameters:
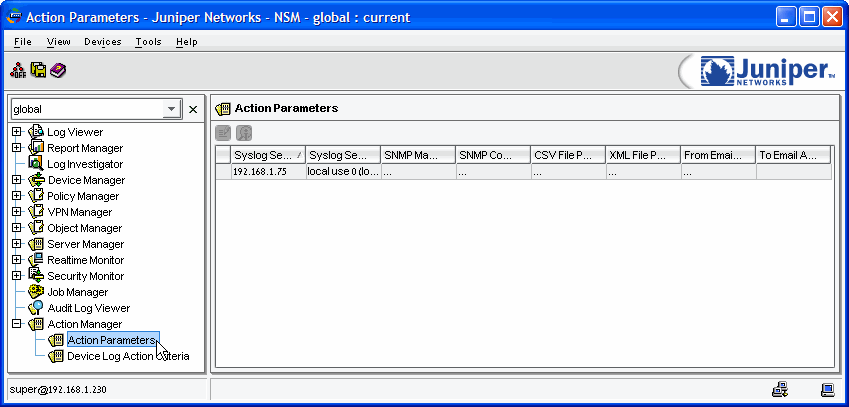
-
In the Action Parameters pane, double-click the entry row:
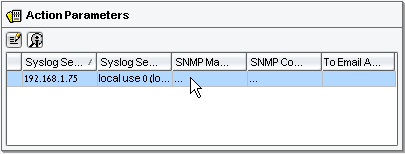
-
In the Action Parameters window, enter the following:
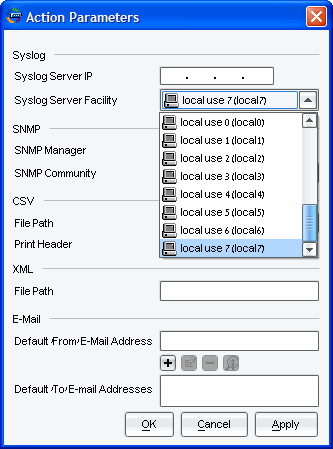
- Syslog Server IP: the IP address of the SecureTrack server, remote collector or distribution server that is managing the device
-
Syslog Server Facility: Select local use 7 (local7)
If you need to use a different facility, you can, in which case you'll also need to configure SecureTrack as described in this tech note.
Click OK.
-
In the navigation pane, under Action Manager, select Device Log Action Criteria:
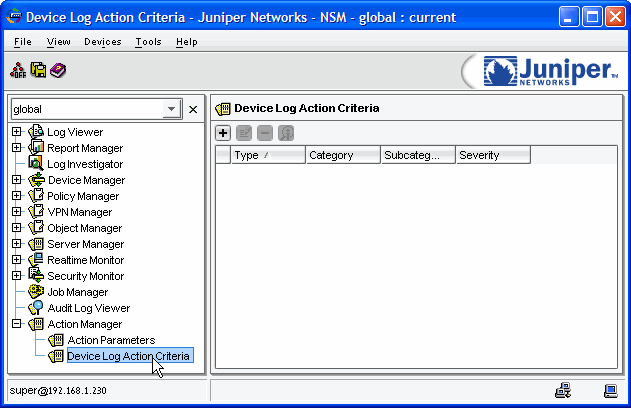
-
To enable identification of users who made policy changes and the time of those policy changes, do the following:
-
Click the plus sign:
-
By Category, select Config (predefined):
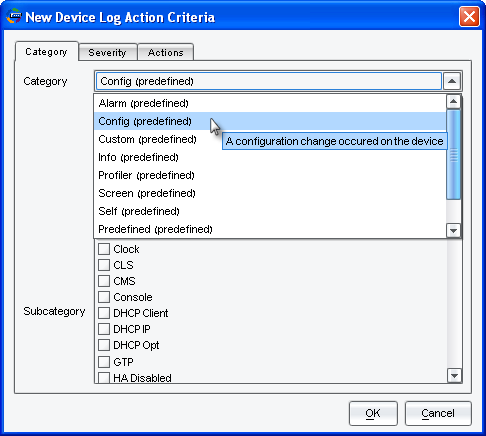
No Subcategory should be selected.
-
In the Actions tab, select Syslog Enable:
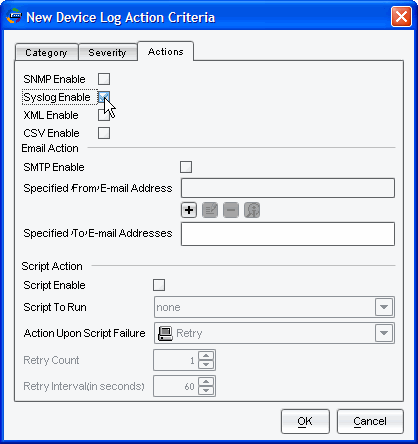
- Click OK.
-
-
To enable Usage reporting, do the following:
-
Click the plus sign:

-
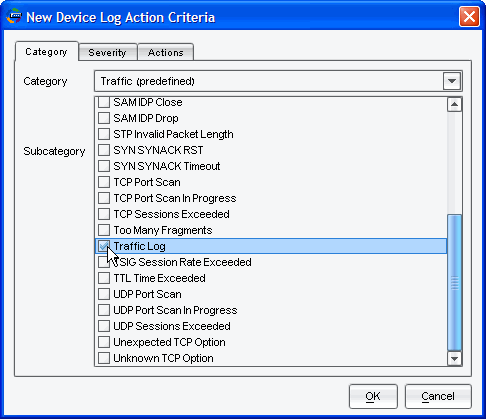
By Category, select Traffic (predefined):
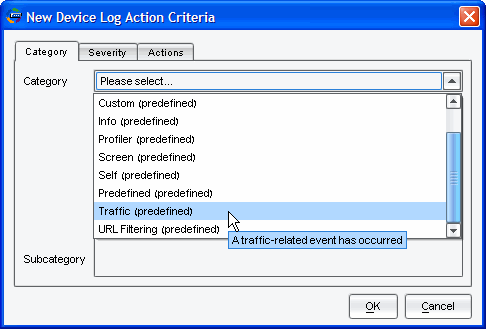
-
For Subcategory, select Traffic Log:
-
In the Actions tab, select Syslog Enable:

- Click OK.
-
