On This Page
Using the Server Decommission Field
As an example of how the Server Decommission field can be used in a workflow, let's use a workflow with these steps:
-
Enter Server Decommission Request - The Server Decommission field can be in the first or any other step in the workflow so that a requester or handler can select the server to decommission:
-
Click in the server field.
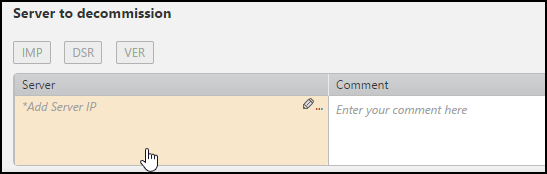
If you are in Multi-Domain Integrated mode, you can also select the domain that the servers are in. The default is to find the specified server in any domain.
-
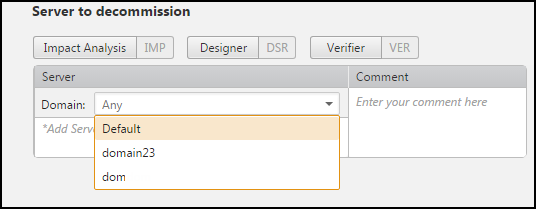
Enter the name of a server, subnet, range of addresses, or enter a list of servers separated by comma or copied from Microsoft Excel.
Addresses with non-continuous network masks are not supported.
You can enter a server as a server name from a monitored firewall, a DNS name, or an IP address.
-
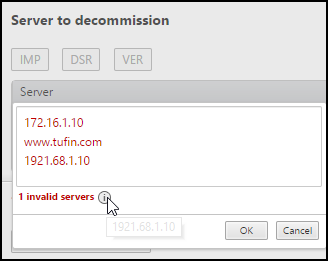
Click OK.
When you click OK, the DNS and IP address values are checked for validity.
-
Click in the comment field.
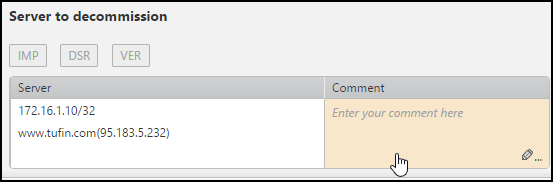
- Enter a comment
- Click outside the field to save the comment.
-
-
Server Decommission Impact Analysis - The impact analysis tool shows where the servers are used in firewall rules across all firewalls:
-
Click Impact Analysis:
-
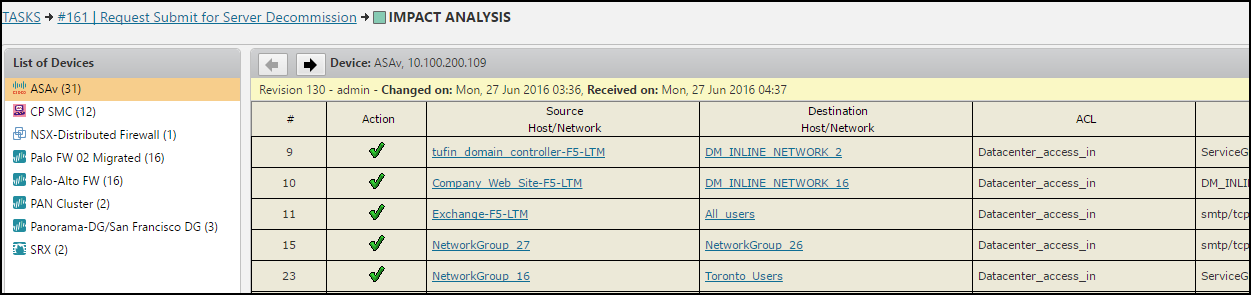
Review the firewall rules where the servers are used, including the relevant domains when you are in Multi-Domain mode.
-
-
Design Server Decommission Changes - The handler can use the Designer to see how to change the firewall rules in order to decommission the servers:
-
Click Designer:
-
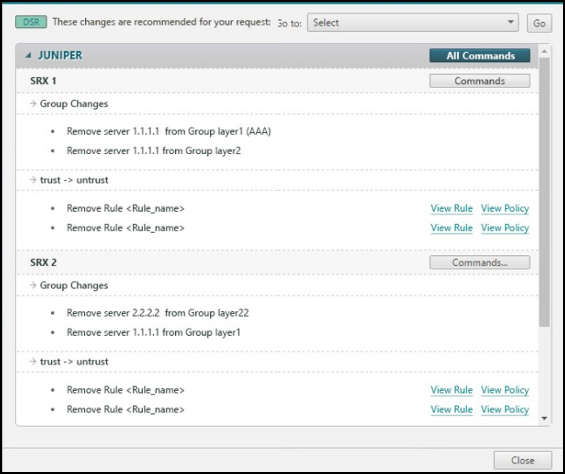
Review the designer instructions.
The instructions can include:
- Remove a rule
- Remove a server from the source or destination of a rule
- Remove a group from a rule
You can review the original server decommission request below the list of instructions.
-
Manually follow the instructions provided by the Designer.
For devices where Provisioning is supported, Designer can implement these changes.
-
-
Verify Server Decommission Changes - The handler can verify that the servers were removed from the firewall rules:
-
Click Verifier:
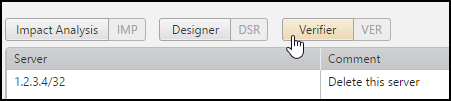
- Review any rules that the servers are still used in.
-
For SecureChange licensing information, see Managing License Allocation.
