On This Page
Enforcing Best Practices Using USP
Managing network security is an increasingly complex and complicated task, with a typical network consisting of both physical and virtual devices from multiple vendors. Take proactive control of your network security by creating, monitoring, and enforcing best practice policies with SecureTrack's Unified Security Policy.
This topic will show you how to create a best practices matrix for identifying, monitoring and blocking Risky Services, and for enforcing the use of rule properties for devices.
What is a USP?
A Unified Security Policy (USP) is a matrix listing all the security zones in your environment and identifying what traffic is allowed between the zones. This lets you control your actual versus desired network segmentation, highlighting policy violations before a change is made on the network so as not to break compliance or expose the network to unnecessary risk. Maintaining the desired network segmentation is a difficult task given the long and complex rulebases and constant influx of change requests. The USP lets you centrally manage policy violations and exceptions for continuous compliance and risk management and to streamline operations.
Overview
To implement best practices or the compliance regulations of a standard, you need to create a USP Matrix containing the compliance zones required by the standard. The compliance zones are placeholder zones into which you place your network zones, using SecureTrack zone hierarchies. Your existing zones can then be collected into these compliance zones, to ensure compliance monitoring of your entire network. To ensure that you maintain ongoing compliance as your network topology evolves, we recommend that you periodically review the hierarchy of your compliance zones.
Zones of protection are unique to each company and vary based on their specific critical cyber asset structure and segmentation. The granularity of the connections between the zones of protection, internal networks, and the internet will also vary by company. The Best Practices USP is a matrix of five example zones: Internet, data center, PM (product management), RnD and sales.
Create the USP
To create a USP that implements Best Practices:
- Create compliance zones required by the best practice or compliance standard.
- Create a Unified Security Policy matrix comprised of all the compliance zones.
- Identify and implement the allowed and blocked connections as connection relationships between the zones.
- Identify and implement any regulation exceptions required by your specific environment in the matrix, and document the reason for the exception.
- Identify and add network zones to the compliance zones you created.
To add network zones to a compliance zone, see the documentation for Zone Hierarchy.
Best Practices Policy for Rule Properties
To create a matrix for enforcing best practices for rule properties of a device, create a matrix that specifies ANY as the USP service and identifies the specific properties to enforce. All device rules that violate the properties requirements specified in the matrix will appear in SecureTrack as violations.
This sample CSV implements the following best practices matrix for rule properties:
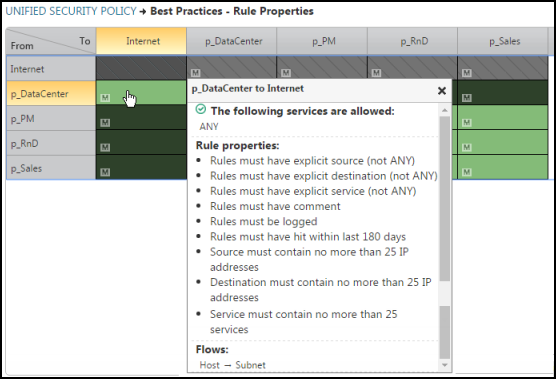
Each entry in the matrix specifies ANY as the USP service, and lists the restrictions for rule property and flow. Customize the matrix to suit your specific best practice policy requirements.
Best Practices Policy for Risky Services
To create a matrix for enforcing best practices for risky services, create a matrix that identifies and blocks all the services you define as risky. All device rules that violate the risky services requirements specified in the matrix will appear in the SecureTrack violations dashboard.
This sample CSV implements the following best practices matrix for risky services:
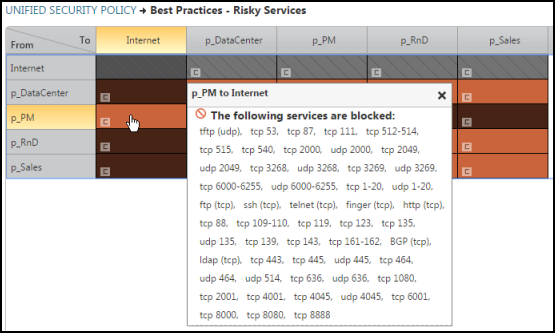
Each entry in the matrix specifies all the services you want to block. Customize the matrix to suit your specific risky services policy requirements.
