On This Page
Advanced Best Practices Using USP
Managing network security is an increasingly complex and complicated task, with a typical network consisting of both physical and virtual devices from multiple vendors. Take proactive control of your network security by creating, monitoring, and enforcing best practice policies with SecureTrack's Unified Security Policy.
This topic will show you how to create advanced best practices USP matrices for identifying, monitoring and blocking risky services, and for enforcing the use of rule properties for devices. Each tool and service used in this example is categorized in one of four risk levels - Critical, High, Medium, Low. A USP matrix is created for each of the risk levels, identifying the restrictions on the services and protocols for that risk level. The required rule properties for all device rules if also defined, and assigned to one of the risk level matrices.
What is a USP?
A Unified Security Policy (USP) is a matrix listing all the security zones in your environment and identifying what traffic is allowed between the zones. This lets you control your actual versus desired network segmentation, highlighting policy violations before a change is made on the network so as not to break compliance or expose the network to unnecessary risk. Maintaining the desired network segmentation is a difficult task given the long and complex rulebases and constant influx of change requests. The USP lets you centrally manage policy violations and exceptions for continuous compliance and risk management and to streamline operations.
Overview
To implement best practices or the compliance regulations of a standard, you need to create a USP Matrix containing the compliance zones required by the standard. The compliance zones are placeholder zones into which you place your network zones, using SecureTrack zone hierarchies. Your existing zones can then be collected into these compliance zones, to ensure compliance monitoring of your entire network. To ensure that you maintain ongoing compliance as your network topology evolves, we recommend that you periodically review the hierarchy of your compliance zones.
Prior to creating the USP, you need to determine the services and protocols currently used in your organization, as follows:
- Identify the services and protocols utilized across your network.
- Determine which services and protocols are or are not allowed between the network zones.
- Assign each service/protocol a compliance risk level in the appropriate zone matrix.
The Advanced Best Practices USP is a matrix of three example zones: Corporate, Internet and DMZ.
To create a USP that implements Advanced Best Practices:
- Create compliance zones required by the best practice or compliance standard.
- Create a Unified Security Policy matrix comprised of all the compliance zones.
- Identify and implement the allowed and blocked connections as connection relationships between the zones.
- Identify and implement any regulation exceptions required by your specific environment in the matrix, and document the reason for the exception.
- Identify and add network zones to the compliance zones you created.
To add network zones to a compliance zone, see the documentation for Zone Hierarchy.
To add the zones used in this topic to TOS, save the Advanced Best Practices - Zones as a CSV file and then import it into SecureTrack > Network > Zones.
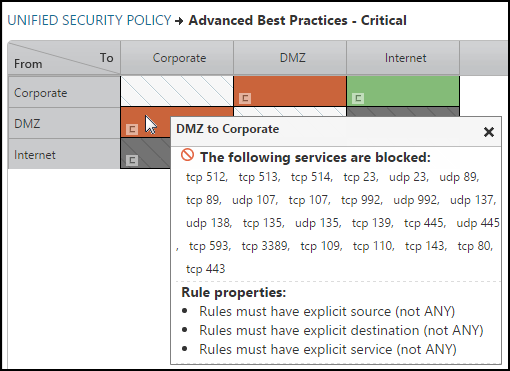
Critical Risk Level Example
The services and protocols identified as critical risk are:
|
From Zone |
To Zone |
Title |
Details |
Services Checked |
|---|---|---|---|---|
|
All |
Corporate DMZ |
Microsoft services |
Risky Microsoft services can pass authentication credentials and data across the network without encryption. Risky Microsoft services can contribute to data leakage. |
137 UDP, 138 UDP, 135 TCP, 135 UDP, 139 TCP, 445 TCP, 445 UDP, 593 TCP, 3389 TCP |
|
All |
Corporate DMZ |
R-services |
Risky R-services can pass authentication credentials and data across the network without encryption. Risky R-services services can contribute to data leakage. R-services can provide direct shell access on server. |
512 TCP, 513 TCP, 514 TCP |
|
All |
Corporate DMZ |
Telnet services |
Telnet services can pass authentication credentials and data across the network without encryption. Telnet services can contribute to data leakage and information exposure. Telnet services can provide direct shell access on server.Telnet services can also be used to launch denial of service attacks and exploits against servers |
23 TCP, 23 UDP, 89 UDP, 89 TCP, 107 UDP, 107 TCP, 992 TCP, 992 UDP |
|
DMZ |
Corporate |
Microsoft services |
Risky Microsoft services can pass authentication credentials and data across the network without encryption. Risky Microsoft services can contribute to data leakage. |
137 UDP, 138 UD, 135 TCP, 135 UDP, 139 TCP, 445 TCP, 445 UDP, 593 TCP, 3389 TCP |
|
DMZ |
Corporate |
POP services |
POP services pass authentication credentials and data across the network without encryption. POP services carry data and contribute to data leakage. |
109 TCP, 110 TCP |
|
DMZ |
Corporate |
IMAP services |
IMAP services pass authentication credentials and data across the network without encryption. IMAP services carry data and contribute to data leakage. |
143 TCP |
|
DMZ |
Corporate |
HTTP/HTTPS services |
HTTP and HTTPS services should not be allowed to Internal networks. |
80 TCP, 443 TCP |
The following requirements should be enforced on all device rules, using USP rule properties:
- All rules must have comments - Documenting rules helps you manage the rule lifecycle, and may be required for audits.
- Rule logging must be enabled - Logging provides ongoing insight into how the rules are utilized.
- Rules may not allow 'Any' service - Allowing any service is more permissive than required. Explicitly specify which services should be allowed.
You can use Automatic Policy Generation to replace overly permissive rules with more optimized rules.
Save this sample Advanced Best Practices - Critical USP matrix as a CSV file and then import it into SecureTrack > Audit > Compliance > Unified Security Policy to create the following USP matrix:
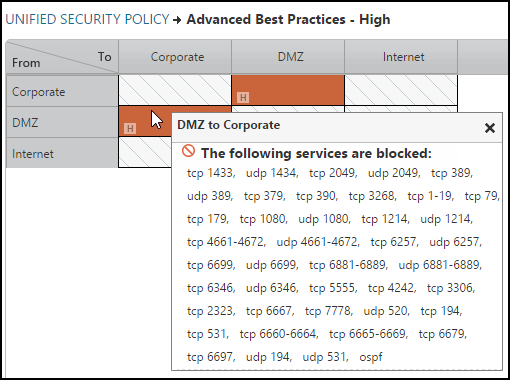
High Risk Level Example
The services and protocols identified as high risk are:
|
From Zone |
To Zone |
Title |
Details |
Services Checked |
|---|---|---|---|---|
|
All |
Corporate DMZ |
Microsoft SQL services |
Microsoft SQL services can pass authentication credentials and data across the network without encryption. Microsoft SQL services can contribute to data leakage. |
1433 TCP, 1434 UDP |
|
All |
Corporate DMZ |
NFS services |
NFS services can pass authentication credentials and data across the network without encryption. NFS services can contribute to data leakage. |
2049 TCP, 2049 UDP |
|
All |
Corporate DMZ |
LDAP services |
LDAP services can pass authentication credentials and data across the network without encryption. LDAP services can contribute to data leakage. |
389 TCP, 389 UDP, 379 TCP, 390 TCP, 3268 TCP |
|
All |
Corporate DMZ |
TCP Small services |
TCP Small services can pass authentication credentials and data across the network without encryption. TCP Small services can contribute to data leakage, information exposure and denial of service attacks. |
1-19 TCP |
|
All |
Corporate DMZ |
Finger services |
Finger services can contribute to data leakage and information exposure. |
79 TCP |
|
All |
Corporate DMZ |
BGP services |
BGP is a dynamic routing protocol used by boarder routers connected to the Internet, it should generally not be allowed to propagate to the Internal networks and DMZ networks. BGP services can contribute to data leakage and information exposure. |
179 TCP |
|
All |
Corporate DMZ |
SOCKS services |
SOCKS services can pass authentication credentials and data across the network without encryption. SOCKS services can contribute to data leakage and information exposure. |
1080 TCP, 1080 UDP |
|
All |
Corporate DMZ |
SNMP services |
SNMP is a network management protocol that can configure and control network equipment, and should be restricted to trusted sources. SNMP services can pass authentication credentials and data across the network without encryption. SNMP services can contribute to data leakage and information exposure. |
161 TCP, 161 UDP, 162 TCP, 162 UDP, 1993 TCP, 1993 UDP, 5161 TCP |
|
All |
Corporate DMZ |
Known P2P services |
P2P services are common virus propagation points and lead to data leakage. |
Kazaa (1214 TCP, 1214 UDP), edonkey (4661-4672 TCP, 4661-4672 UDP), winmx and napster (6257 TCP, 6257 UDP, 6699 TCP, 6699 UDP), bittorrent (6881-6889 TCP, 6881-6889 UDP), gnutella (6346 TCP, 6346 UDP), eMule (5555 TCP, 4242 TCP, 3306 TCP, 2323 TCP, 6667 TCP, 7778 TCP) |
|
All |
Corporate DMZ |
OSPF services |
OSPF is a dynamic routing protocol used by internal organization routers. It should generally not be allowed to propagate from the External network to the Internal and DMZ networks. OSPF services can contribute to data leakage and information exposure. |
IP protocol 89 |
|
All |
Corporate DMZ |
RIP services |
RIP is a dynamic routing protocol. It should generally not be allowed to propagate from the External network to the Internal and DMZ networks. RIP services can contribute to data leakage and information exposure. |
520 UDP |
|
All |
Corporate DMZ |
IRC services |
IRC services pass authentication credentials and data across the network without encryption. IRC services are also common virus propagation points and lead to data leakage. |
TCP ports 194,531,6660-6664,6665-6669,6679,6697; UDP ports 194, 531 |
To add this matrix to TOS, save this sample Advanced Best Practices - High USP matrix as a CSV file, and then import it into SecureTrack > Audit > Compliance > Unified Security Policy to create the following USP matrix:
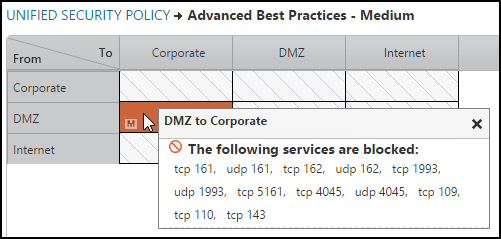
Medium Risk Level Example
The services and protocols identified as a medium risk are:
|
From Zone |
To Zone |
Title |
Details |
Services Checked |
|---|---|---|---|---|
|
All |
Corporate DMZ |
X11 services |
X-11 services can pass authentication credentials and data across the network without encryption. X-11 services can also be used to launch denial of service attacks and exploits against servers. |
6000-6255 TCP |
|
All |
Corporate DMZ |
SNMP services |
SNMP is a network management protocol that can configure and control network equipment, and should be restricted to trusted sources. SNMP services can pass authentication credentials and data across the network without encryption. SNMP services can contribute to data leakage and information exposure. |
161 TCP, 161 UDP, 162 TCP, 162 UDP, 1993 TCP, 1993 UDP, 5161 TCP |
|
All |
Corporate DMZ |
LOCKD services |
The lockd daemon manages RPC connections between the client and the server for the Network Lock Manager (NLM) protocol. LOCKD services can pass authentication credentials and data across the network without encryption. |
4045 TCP, 4045 UDP |
|
All |
Corporate DMZ |
POP services |
POP services pass authentication credentials and data across the network without encryption. POP services carry data and contribute to data leakage. |
109 TCP, 110 TCP |
|
All |
Corporate DMZ |
IMAP services |
IMAP services pass authentication credentials and data across the network without encryption. IMAP services carry data and contribute to data leakage. |
143 TCP |
To add this matrix to TOS, save this sample Advanced Best Practices - Medium CSV USP matrix as a CSV file, and then import it into SecureTrack > Audit > Compliance > Unified Security Policy to create the following USP matrix:
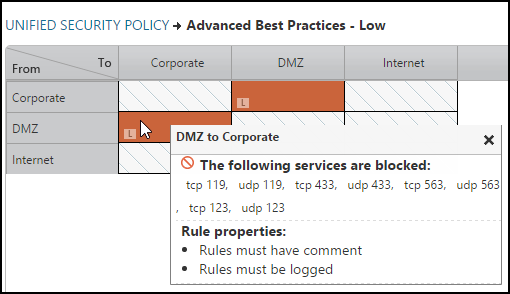
Low Risk Level Example
The services and protocols identified as low risk are:
|
From Zone |
To Zone |
Title |
Details |
Services Checked |
|---|---|---|---|---|
|
Corporate DMZ |
All |
NNTP services |
NNTP services pass authentication credentials and data across the network without encryption. NNTP services are also common virus propagation points and lead to data leakage. |
119 TCP, 119 UDP, 433 TCP, 433 UDP, 563 TCP, 563 UDP |
|
Corporate DMZ |
All |
NTP services |
NTP services can contribute to information exposure and denial of service attacks. |
23 TCP, 123 UDP |
To add this matrix to TOS, save this sample Advanced Best Practices - Low CSV USP matrix as a CSV file, and then import it into SecureTrack > Audit > Compliance > Unified Security Policy to create the following USP matrix: