On this page
Cloning a Network Object Policy Field
|
|
This topic is intended for SecureChange requesters, responsible for creating change requests in SecureChange. |
Overview
A workflow which includes Clone Network Object Policy (formerly known as Clone Server Policy) lets you duplicate the access permissions of an existing server in your security policy for new servers. After cloning a server policy, all rules and object groups which include the IP address of the existing server will also include the IP addresses of the new servers.
What can I do here?
Enter a clone network object policy server request
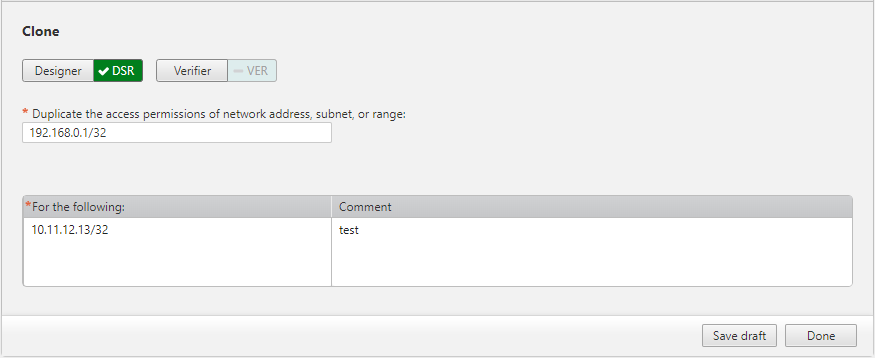
The Clone Network Object Policy Server field can be in the first or any other step in the workflow. This allows a requester or handler to select which existing server’s access permissions should be added to new servers in your security policy.
After entering values, click outside the field, to initiate a save and a validity check on the value entered.
-
In For the security rules that include server field, enter a valid server name, subnet, range, or IPv4 address. This is the existing server policy whose access permissions will be added to the selected additional servers.
Addresses with non-continuous network masks are not supported.
-
In Add the following server(s) field enter all the servers which are to be associated with the access permissions and rules of the existing server. Up to 50 servers can be entered.
-
Enter a comment that relates to this cloning instance.
Design clone network object policy changes
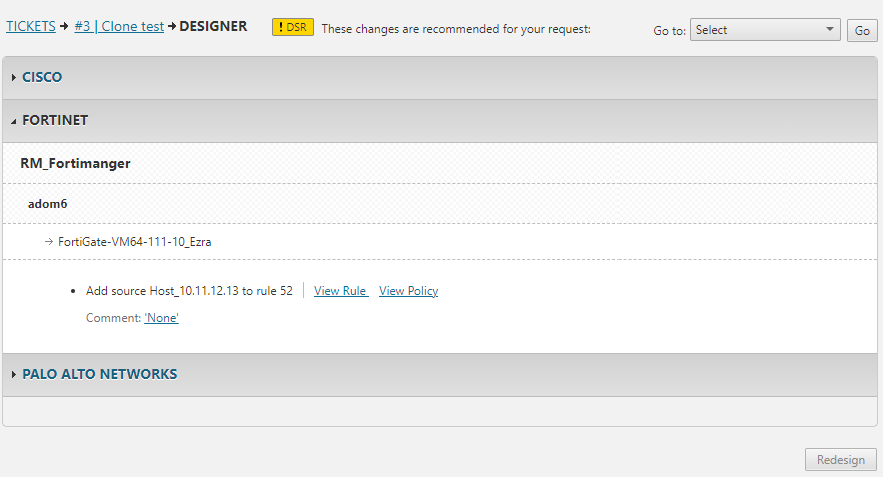
The handler uses Designer to view the relevant policies, rules and groups for each device and suggests how to add the access permissions of the existing server for the new servers.
-
Click Designer.
-
Review the Designer instructions. The instructions can include:
-
Add object to rule
-
Add object to a group
-
Create new object
-
-
Review the Clone Network Object Policy suggested changes for each device.
-
Manually follow the instructions provided by the Designer. For devices where Provisioning is supported, click Update Policy to provision the changes to the device.
Verify clone network object policy changes
The handler can verify that the Designer suggestions were provisioned or manually applied to the relevant rules for the specified server policies.
-
Click Verifier.
-
Verify that the access permissions have been applied for the additional servers. Verifier results displays two sections:
-
Rules successfully implemented: Lists all the rules to which the selected servers are added.
-
Rules not implemented: Lists all the to which selected servers were not added. For example, due to partial implementation or inability to calculate.
-
How do I get here?
SecureChange > ![]() Tickets > Click a Clone task.
Tickets > Click a Clone task.
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague