On this page
Configuring a Cisco ASA to Send Syslogs
|
|
This topic is intended for TOS Administrators. |
Overview
To configure Cisco ASA or virtual context syslogs to be sent, configure either from the CLI or from ADSM.
For a general overview about syslogs, see Sending Additional Information via Syslog.
Syslog proxy is supported for specific devices. For more information on syslog proxy support for supported devices, see Configuring Devices to Send Logs.
Only rules that are marked for logging in the device are included in the syslogs.
Configuration using CLI commands
|
Configuration |
CLI Command |
|---|---|
|
Configure the device to send syslog messages |
logging enable |
|
Set that the timestamp is included in the syslog message |
logging timestamp |
|
Set the level of events for which syslog messages are sent |
logging facility 23 |
|
Set the device-id that is included in the syslog message The Hostname for the device must be explicitly set via syslog for Real Time Monitoring to retrieve data. |
logging device-id hostname |
|
Set the device-id that is included in the syslog message with a virtual context |
logging device-id context-name |
|
Set to send events to SecureTrack for full accountability |
logging list securetrack message 111008 |
|
Set to send events for SecureTrack APG and SecureApp discovery |
logging list securetrack message 106100 |
|
Set to send events for SecureTrack APG and SecureApp discovery |
logging list securetrack message 106023 |
|
Set the level of severity of the messages that you want to receive |
|
|
Set the trap message list name for the syslog messages |
logging trap securetrack |
|
Set the SecureTrack server to send the syslog messages to:
|
logging host <interface_name> <ip_address> |
Configure using ASDM
-
Log into the ASDM and enter the syslog configuration for the ASA device:
-
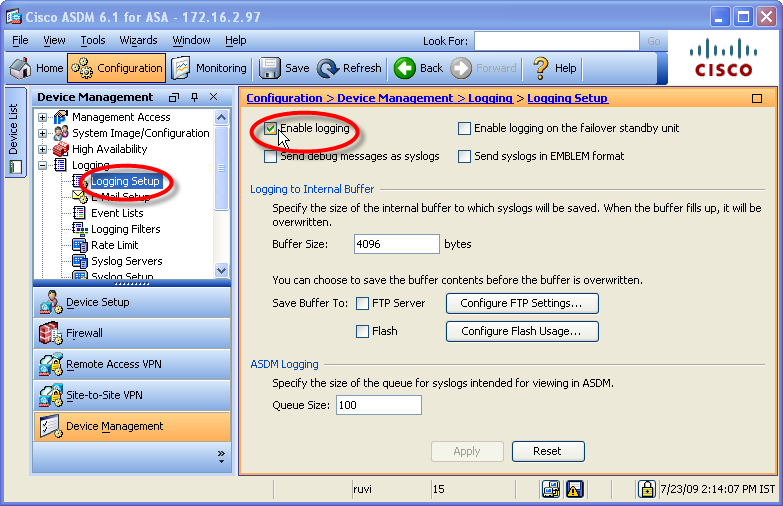
Enable logging on the ASA device:
-
Add the event IDs that you want to the ASA device to send:
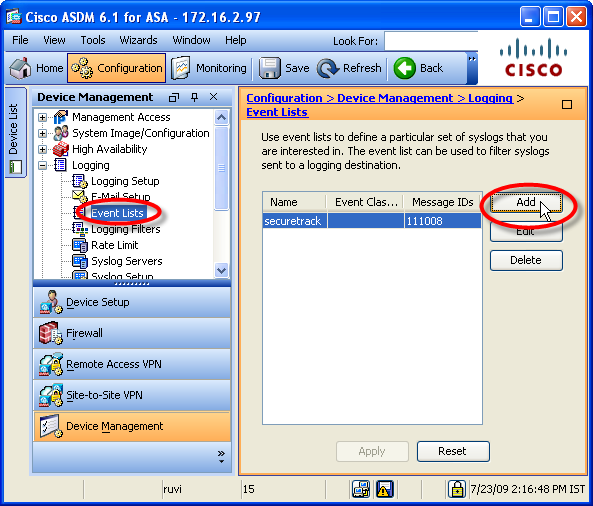
- Select Event Lists, and click Add.
-
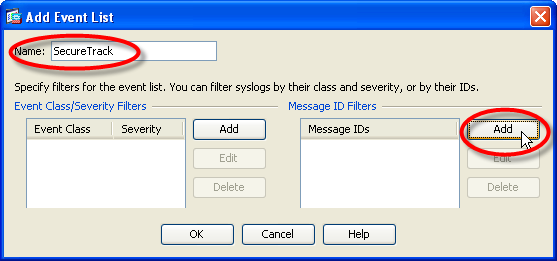
In the Add Event List window, type a Name, and under Message ID Filters, click Add.
-
Enter a syslog ID and click OK.
Syslog ID
Purpose
Notes
111008
Full accountability
SecureTrack APG and SecureApp connection discovery
- Syslog ID 106100 only sends syslogs for logged rules.
- For APG, you can use either of the syslog IDs or both IDs
- Click OK to close the Add Event List window.
-
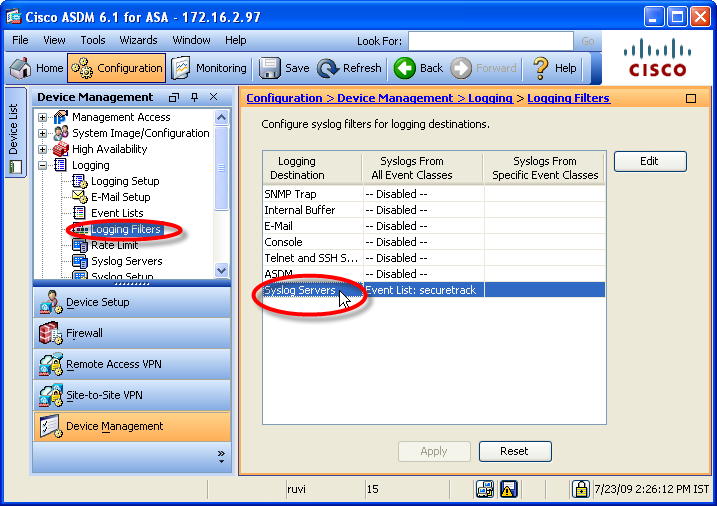
Configure the logging filters to use the specified event IDs:
-
Configure SecureTrack as a syslog server:
-
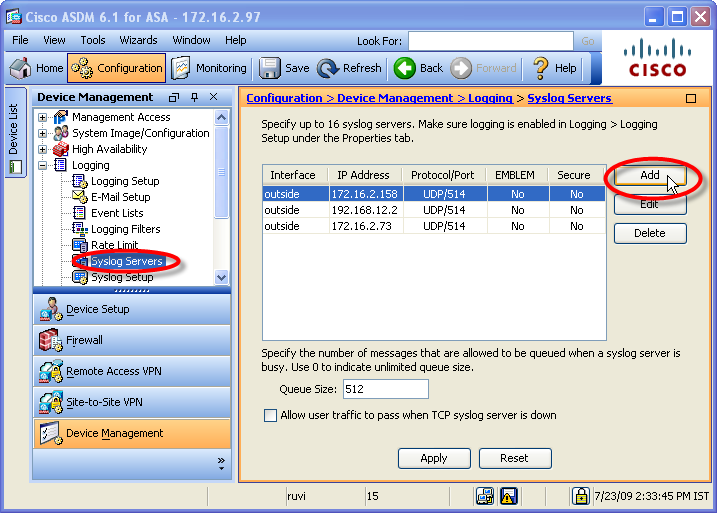
Select Syslog Servers, and click Add.
- In the Add Syslog Server window, select the interface used to access SecureTrack, and enter the appropriate TOS destination described in Sending Additional Information via Syslog..
- Select UDP, Port:
514, and clear Log messages in Cisco EMBLEM format. 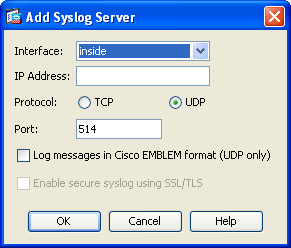
- Click OK.
-
-
Configure the format for the syslogs:
-
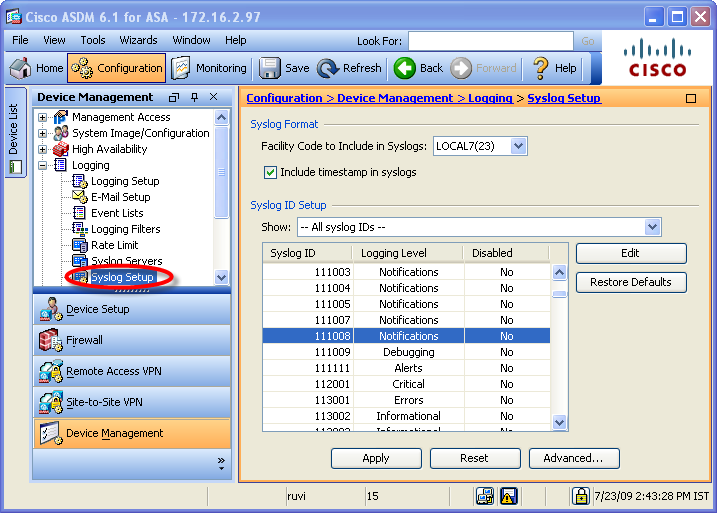
Select Syslog Setup.
-
Select Include timestamp in syslogs.
-
By Facility Code to Include in Syslogs, select LOCAL7(23).
To use a different facility, you must configure SecureTrack as described in this tech note: Configuring SecureTrack for Non-Default Syslogs
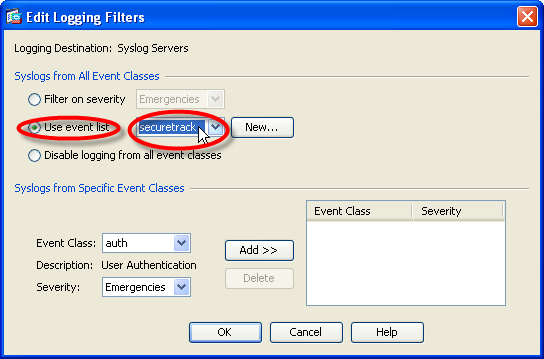
- Scroll down and double-click entry 111008. Set its Logging Level to Notifications, and click OK.
- Click Apply.
-
Still in the Syslog Setup page, click Advanced and select Enable syslog device ID.
If the device is not in context mode, you must enable the syslog device ID from the device's CLI with this command:
logging device-id string <Enter the ID> -
Configure a unique logging ID by selecting one of the following. No other device, including virtual contexts even on other devices, may have the same ID:
-
Hostname
The Hostname for the device must be explicitly set via syslog for Real Time Monitoring to retrieve data.
-
Context name (in a Virtual Context)
-
IP address (select an interface)
-
String (type the desired ID)
-
-
Click OK, and Apply.
For virtual contexts, configure a logging ID for each context.
-
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague