On this page
Cisco ACI Fabric Visibility in TOS
Overview
Tufin integrates your Cisco ACI device by modeling the ACI fabric in TOS. Each tenant is represented as a separate device
TOS derives robust security access rules to interpret and emulate the allowed ACI traffic flows. This set of rules is less susceptible to changes caused by small shifts in ACI configuration. The resulting Tufin security policy enables, redirects, and blocks the same traffic that the ACI does.
Each access rule includes metadata to indicate how it is derived from the ACI fabric, so you can track ACI configuration changes and search for relevant keywords. Rules that are built from ACI contracts indicate which contract and subject they are based on. Additional rules are derived from the configuration in the ACI, for example, vrf enforcement rules, which include implicit conditions that are external to contracts.
While the ACI zoning rules are not directly imported into TOS, the access rules also simulate ACI zoning rule behavior, including emulating the priority ordering of the zoning rules.
When you associate a contract with VRFs as consumers or as providers and set the contract scope to Application-Profile, the behavior of Cisco ACI for this scope is non-deterministic. TOS does not generate security rules for this situation, because the configuration may create different sets of zoning rules with different priorities at different times.
ACI Hierarchy Visibility
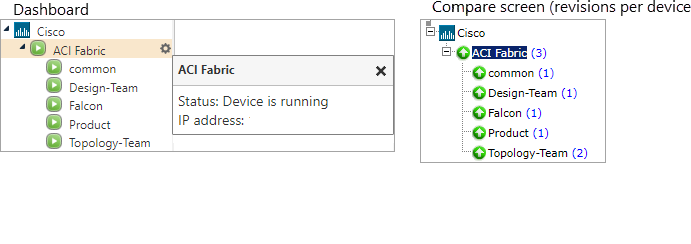
The following image displays the ACI hierarchy in the TOS Dashboard and in the Compare screen (with number of revisions per device).
Access Rules and ACI Revisions
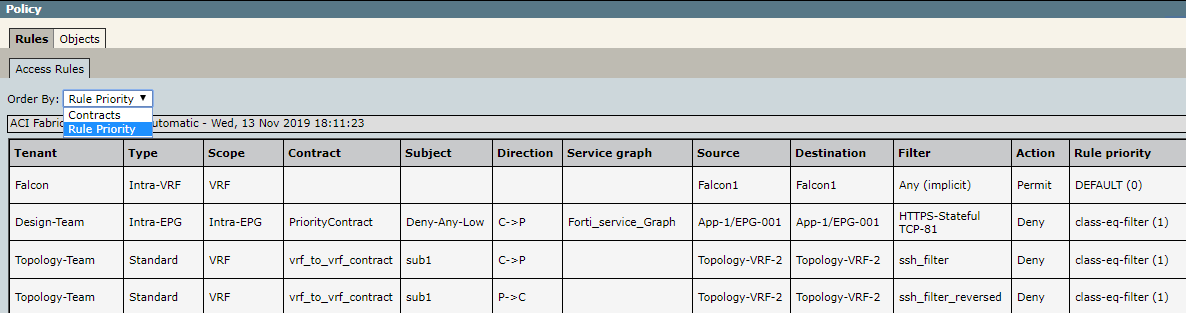
At the parent device level, for each policy revision, the Access Rules table (Compare Revisions > View Policy > Rules > Access Rules) displays a list of the access rules that model the fabric, grouped or ordered by tenant, type, and scope.
The Access Rules in a TOS policy present the source, destination, filters for protocol services, action, and the priority of the ACI zoning rule they emulate. Access rules that are generated from an ACI contract may also include the contract, subject, direction and related service graph information.
When the contracts in the Common tenant include the EPGs of other tenants, the Access Rules may include cross tenant rules generated from Standard and Taboo contracts that also model the traffic between those EPGs.
|
Column |
Description |
|---|---|
| Tenant | Which tenant the access rule is associated with |
| Type |
Defines the rule mechanism type:
|
| Scope |
Defines which providers can communicate with which consumers:
|
| Contract | Contract from which the access rule is derived |
| Subject | Sub contracts within the contract |
| Direction |
Rule traffic direction
|
|
Service graph |
External firewall used as a filter for traffic redirection and access decisions |
|
Source |
Entity from which traffic originates |
|
Destination |
Entity to which traffic arrives |
|
Filter |
Set of services |
|
Action |
How to handle the traffic defined by the rule:
|
|
Rule priority |
Priority of the emulated ACI zoning rule |
Viewing Tenant Access Rules
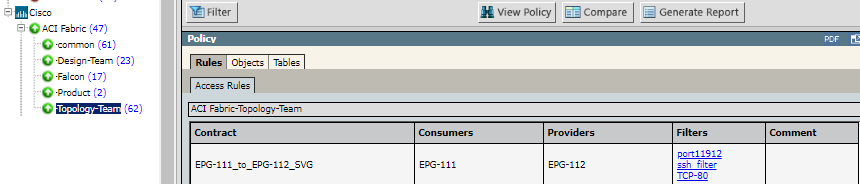
When you select the ACI tenant device and a revision, View Policy > Rules > Access Rules summarizes the contract, consumers, providers, and filters for each rule.
Viewing the Tenant
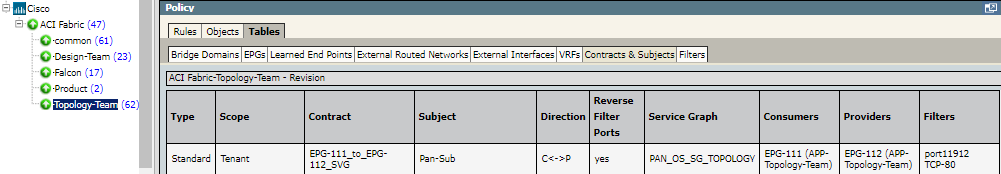
When you select the ACI tenant device and a revision, View Policy > Tables presents tabs to explore the TOS model of the tenant information.
Tufin provides added value by collecting information for each ACI tenant in a single location within the Tables tab, grouped by sub tabs:
|
Sub tab |
Description |
|---|---|
| Bridge Domains |
Presents the bridge domain details for the subnets and VRFs related to each bridge domain in the tenant. The table includes the following information: Name of the bridge domain, related VRFs and subnets, subnet type, and relevant segment |
| EPGs |
Presents the application profile for each EPG in the tenant. The table includes the following information: EPG name and Class ID, related VRFs and bridge domains, Intra EPG Isolation status (enforced or unenforced), the Contract Master, Preferred Group Member action (include or exclude), and the related EPG Subnets |
|
Learned End Points |
Presents the end point details and related EPG information. The table includes the following information for the tenant: Application Profile, EPG name and Class ID, VRF, Bridge Domain, Contract Master, Preferred Group Member action (include or exclude), Intra EPG Isolation status (enforced or unenforced), and the EPG Subnets and End Points |
|
External Routed Networks |
Presents the information for the External Routed Networks. The table displays which VRFs, protocols and External Routed Domain are related to each external routed domain in the tenant |
|
External Interfaces |
Presents the information for External Interfaces. The table includes the External Network Name, the VRF information for the External Interfaces, as well as the Node, Interfaces. IP address, and the Designated Router and Backup Designated Router |
|
VRFs |
Presents the information for VRFs in the tenant, by VRF name. The table includes the relevant Segment and Class ID, Policy control status (enforced or unenforced), EPG collection for VRG (vzAny) , Preferred group status (enabled or disabled) and Preferred group members |
|
Contracts & Subjects |
For each tenant, presents the details for each subject and each direction in the contracts. The table includes the Contract Type and scope, and the Contract and Subject names, the Direction of the contract, whether Reverse Filter Ports are used (yes or no), the related Service Graph name, names of the Consumers and Providers, and Filters |
|
Filters |
Presents the filter details for the tenant. The table includes the Filter and Entry names, Ether type, IP protocol, whether Fragments only, whether the filter is Stateful, and the Source and Destination ports |
At the tenant level:
-
View Policy > Tables displays the same information presented in Objects > Network Objects
-
View Policy > Tables > Filters includes the same information presented in Objects > Services
Viewing the ACI in the Map
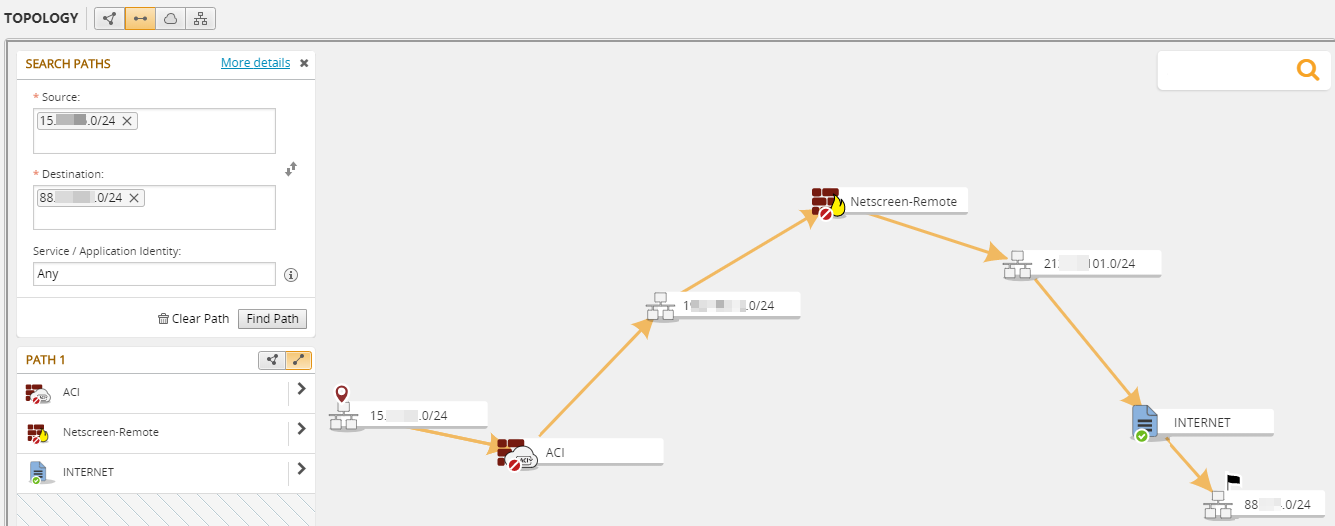
For Cisco ACI devices, Tufin supports path calculations in the Map with security simulations and with service graph calculations. You get to search for paths that cross the ACI fabric on the way from source to destination in Path Analysis. We show you the access rules from the Tufin model that enable, redirects, or denies the traffic that crosses the ACI.
You can search the Map for paths that simulate East/West and North/South connectivity both with and without redirection to Service Graph elements.
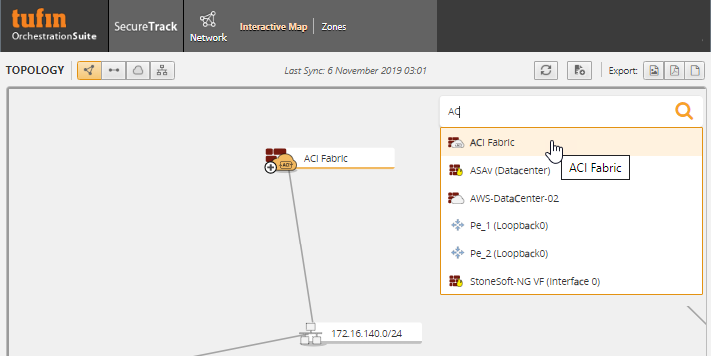
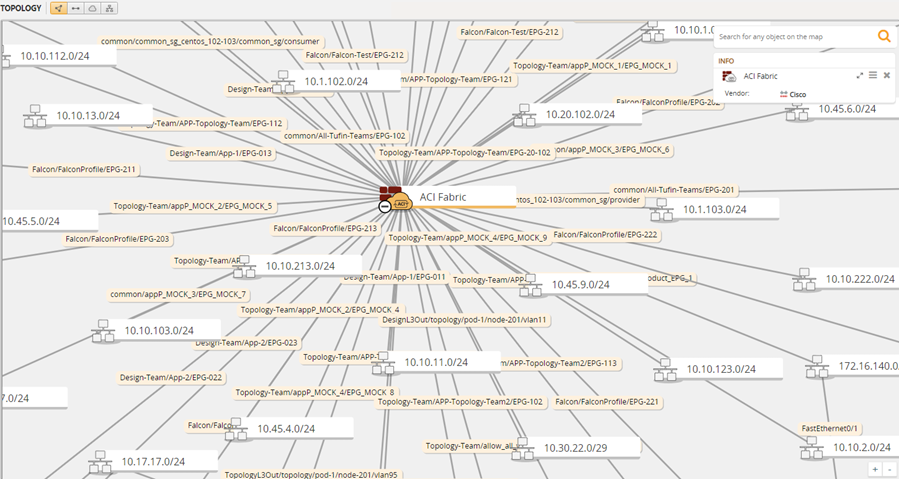
When you search for the ACI device in the Map, the ACI is presented as a single firewall in the Map and displays the aggregated information from the different tenants.
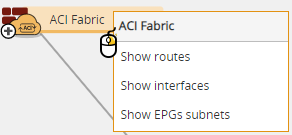
Right click  and select an option to display lists of routes, interfaces, and the EPG subnets for the ACI:
and select an option to display lists of routes, interfaces, and the EPG subnets for the ACI:
-
Show routes displays the network, interface name and gateway per route.
-
Show interfaces displays the consumer or provider interface name, the IP, the bridge domain and interface type (either an external or service graph interface).
A service graph interface name specifies the tenant, the contract name, the service graph template name, and whether the interface is serving as provider or consumer.
For example, common/common_sg_rhel_192-103/common_sg/consumer
-
Show EPGs subnets displays the subnet name, IP, and bridge domain. Subnets are connected to the ACI by logical interfaces.
The Map displays a single interface per subnet, even if several EPGs are associated with this subnet. An EPG is associated with all subnets that are configured on the EPG's bridge domain.
Click  to expand the subnets:
to expand the subnets:
-
If a single EPG leads to a subnet, the EPG name appears in the Map
-
If more than a single EPG leads to the same subnet, the names of the EPGs do not appear
Using the ACI in Path Analysis
You can search for paths which simulate the traffic flow for east/west and north/south connectivity and the traffic that redirects to Service Graph.
Search Paths can calculate the paths for traffic that the ACI redirects to firewalls when the ACI is configured as follows:
- The firewalls are configured in the ACI as unmanaged service graph elements.
- Service graph templates were created for the firewalls.
- Bridge domains were created for the various firewall interfaces.
- PBR entries containing the interface IP and MAC address were created for firewall interfaces that are connected to the ACI (optional).
-
Device selection policies were created, containing:
-
Contract name
-
Service graph template name
-
Consumer and Provider interfaces include:
-
IP addresses
-
Bridge domain
-
PBR entry (optional)
-
-
External EPGs in the Source or Destination Field
You can add an external EPG to the Source/Destination fields (North/South).
The external EPG appears as fully qualified.
Autocomplete works with external EPG IPs and External EPG names.
IP to EPG (East/West) in the Source or Destination Field
You can add an IP or an EPG to the Source/Destination fields.
EPGs are displayed as fully qualified.
Autocomplete suggests the most exact results for an EPG that contain the requested IP address:
- Learned end-point autocomplete is applied only on full IP match
- Autocomplete task starts only after the third octet of the IP
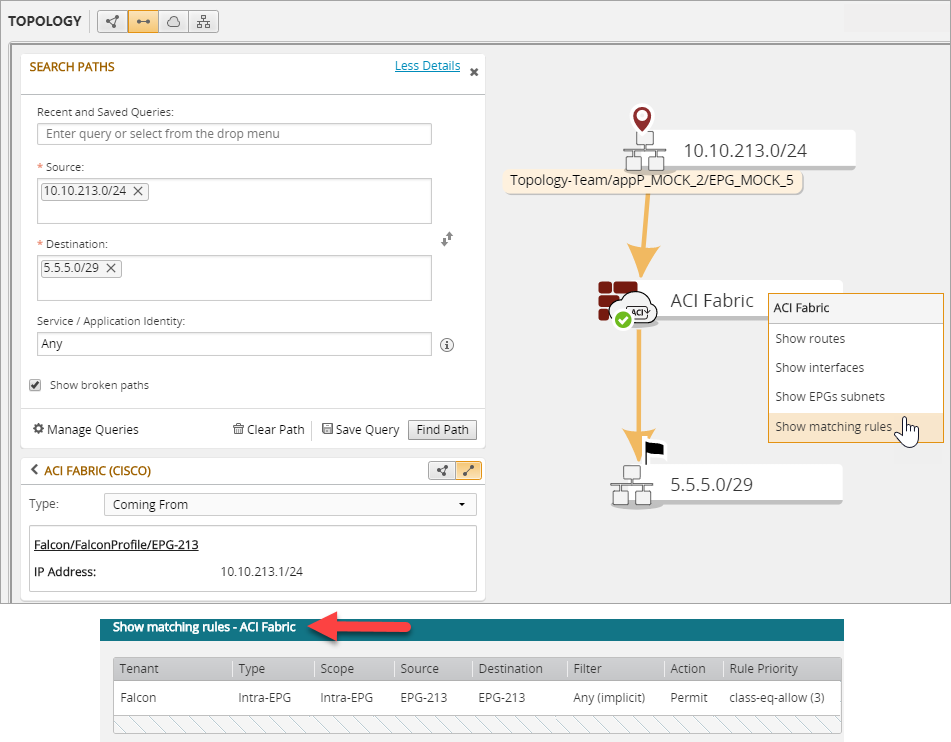
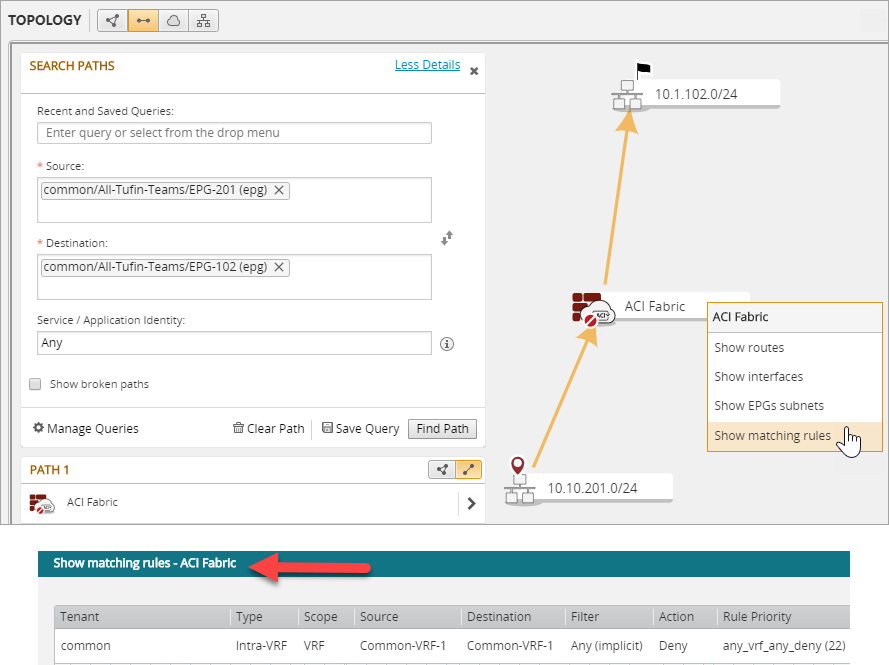
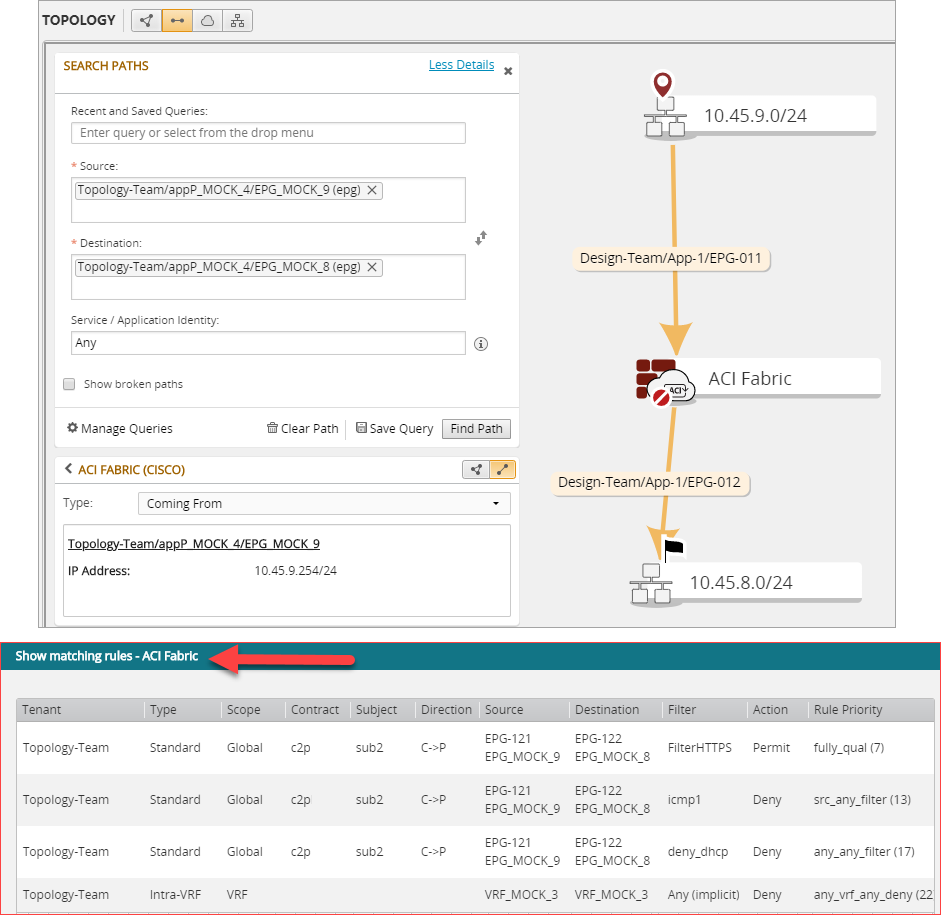
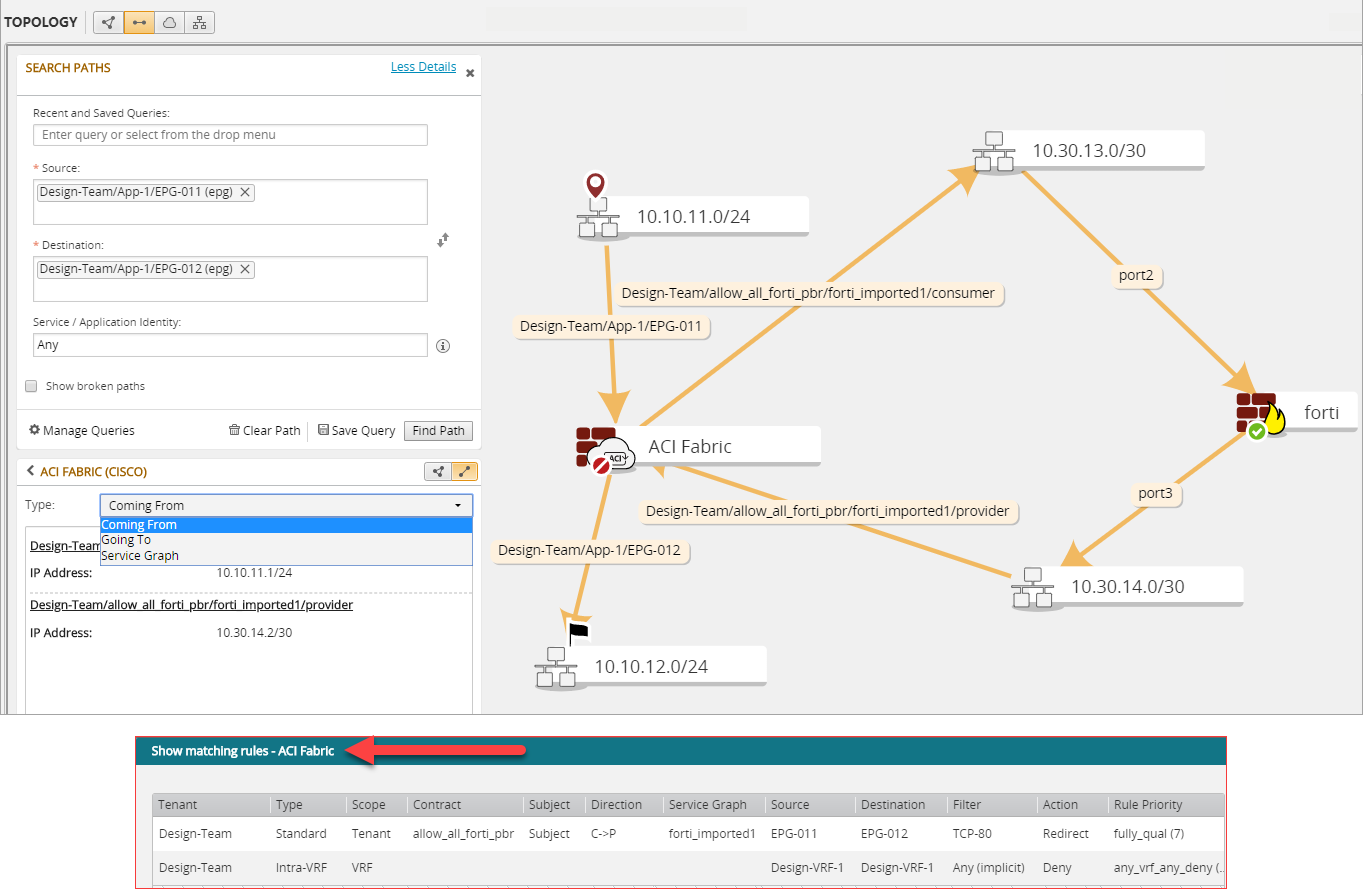
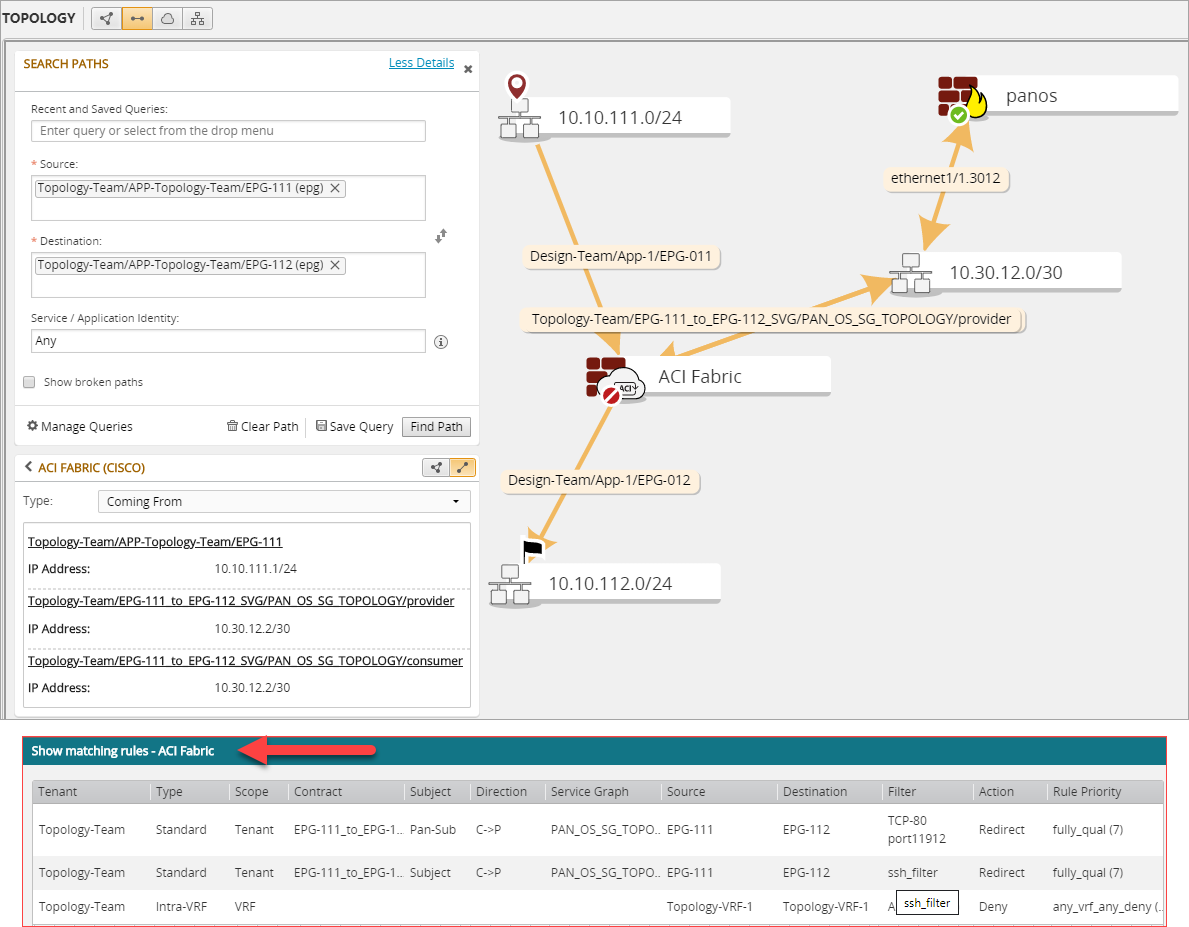
Show Matching Rules
Path calculation between EPGs, matched by an intra-EPG traffic rule that permits traffic.
Path calculation between EPGs matched by an intra-VRF rule that denies traffic.
Path calculation between EPGs matched by rules from a standard contract.
Path calculation between EPGs with Service Graph - two arms
Path between EPGs with Service Graph - single arm
How Do I Get Here?
SecureTrack > Reports ![]() > Compare Revisions
> Compare Revisions
SecureTrack > Map
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague