On This Page
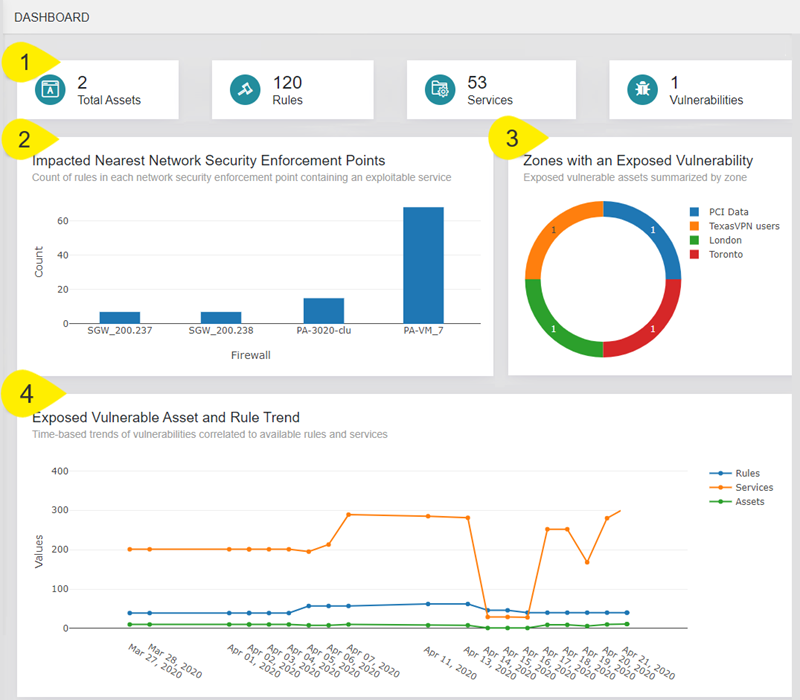
You can analyze the vulnerability status of your network in the dashboard. The dashboard provides you with the context and visibility, allowing you to view the total numbers of vulnerable assets, exploitable rules, affected services, and network-based vulnerabilities detected. You can view security trends over time, as well as the number of network-based vulnerabilities detected per zone. This information provides you with a comprehensive holistic view of your network, allowing you to better understand if your vulnerability mitigation processes are improving. if you are more exposed now than before, and which assets and tasks need to be prioritized.
The dashboard is located in the Home menu.
The dashboard is divided into four sections (as seen in the image above):
-
Vulnerability numbers: The numbers in this section represent the current state of the assets in the critical zones defined in the Settings menu.
-
Total Assets: Total amount of vulnerable assets exposed through the exploitable access.
-
Rules: Total amount of rules that provide access to the vulnerable assets.
-
Services: Total amount of services that can be exploited using the vulnerable assets.
-
Vulnerabilities: Total amount of vulnerabilities detected .
-
-
Impacted Nearest Network Security Enforcement Points: The chart displays the number of rules in each network security point that can be exploited. Each bar represents the number of rules that can be exploited per network security point.
-
Zones with an Exposed Vulnerability: The chart displays the number of vulnerable assets per critical network zone, allowing you to view which network zone have the most vulnerable assets and prioritize your mitigation efforts accordingly.
-
Exposed Vulnerable Asset and Rule Trend: This chart displays the trends in exposed assets, exploitable rules, and affected assets over a period of time. The chart allows you to analyze whether your vulnerability mitigation processes are improving the overall vulnerability status of your network, or whether further actions need to be considered.
The app correlates rules by the vulnerabilities’ services. Only rules and zones that match the source or destination, AND one of the services, are considered vulnerable and correlated to the app.
