On This Page
Azure Permissions
To allow SecureCloud to monitor Azure subscriptions, you must grant the appropriate permissions. For more information on Azure authorizations, see the official Microsoft Azure documentation - What is role-based access control (RBAC) in Azure.
-
In Azure Active Directory, create a new application registration where:
Name=<Your AppReg name>
-
Add permissions to the application registration in one of the following ways:
Add Standard Roles
This method gives read permissions to all resources and does not allow SecureCloud to make changes to your Azure definitions. The permissions are the same as the custom read-only role.
-
For the required subscription, under Access control (IAM), add a role assignment to the application registration created in the previous step where:
Role=Reader
Assign access to=Azure AD user, group or service principal
-
To enable integration with SecureChange, add an additional role assignment to the application registration:
Role=Network Contributor
Assign access to=Azure AD user, group or service principal
-
To enable SecureCloud to perform the CIS benchmark audit:
- Add Azure Active Directory Graph API permission to the application registration
- Select "Application permissions"
- Add Directory.read.all permission to the Azure Active Directory Graph API
- Grant the application registration admin consent for Default Directory
- Add a client secret.
Create a Custom Read-Only Role
This method gives the same permissions as using standard roles - read permissions to all resources and does not allow SecureCloud to make changes to your Azure definitions.
-
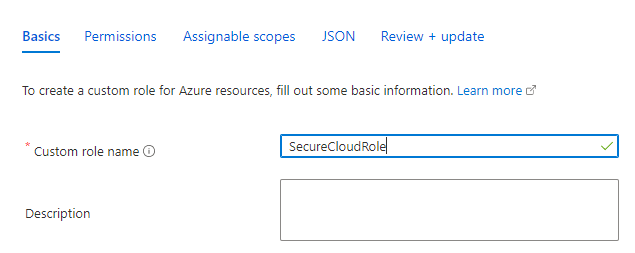
Create a custom role.
-
Select JSON.
-
Under Permissions enter:
"permissions": [
{
"actions": [
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Network/networkSecurityGroups/read",
"Microsoft.Network/applicationSecurityGroups/read",
"Microsoft.Network/routeTables/read",
"Microsoft.Network/virtualNetworks/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.Network/localnetworkgateways/read",
"Microsoft.Network/virtualNetworkGateways/read",
"Microsoft.Network/networkInterfaces/read",
"Microsoft.Compute/virtualMachines/read",
"Microsoft.Network/applicationGateways/read",
"Microsoft.Network/loadBalancers/read",
"Microsoft.Network/publicIPAddresses/read",
"Microsoft.Network/azurefirewalls/read",
"Microsoft.Network/ipGroups/read",
"Microsoft.Authorization/policyAssignments/read",
"Microsoft.DBforPostgreSQL/servers/read",
"Microsoft.DBforMySQL/servers/read",
"Microsoft.DBforMariaDB/servers/read",
"Microsoft.Sql/servers/read",
"Microsoft.Sql/managedInstances/read",
"Microsoft.DocumentDB/databaseAccounts/read",
"Microsoft.Network/networkSecurityGroups/write",
"Microsoft.Storage/storageAccounts/write",
"Microsoft.Network/virtualWans/read",
"Microsoft.Network/virtualHubs/read",
"Microsoft.Network/virtualHubs/hubVirtualNetworkConnections/read",
"Microsoft.Network/vpnGateways/vpnConnections/read",
"Microsoft.Network/vpnsites/read",
"Microsoft.Network/expressRouteGateways/expressRouteConnections/read",
"Microsoft.Network/virtualHubs/hubRouteTables/read",
"Microsoft.Network/virtualHubs/effectiveRoutes/action",
“Microsoft.Compute/virtualMachineScaleSets/read”,
“Microsoft.NetworkCloud/kubernetesClusters/read”,
“Microsoft.Security/assessments/subAssessments/read”
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]In addition, for NSG Optimiser and flow logs integration:
-
In the
actions[ ]section, add the following permissions : -
In the
dataActions [ ]section, add the following permission:
-
-
Save the role.
Create a Custom Update Role
This role gives read permissions to all resources, and write permissions to NSG and Storage Accounts (buckets).