On This Page
Editing Rule Metadata
You can edit the details, or metadata, of rules in Policy Browser.
To edit the details of one or more rules:
-
Select the device and enter the search criteria to see matching rules.
-
Click on the rule or rules you want to edit.
You can also select a rule and click
 to see the rule details.
to see the rule details. -
Click
 to edit the rule metadata, and enter the following:
to edit the rule metadata, and enter the following: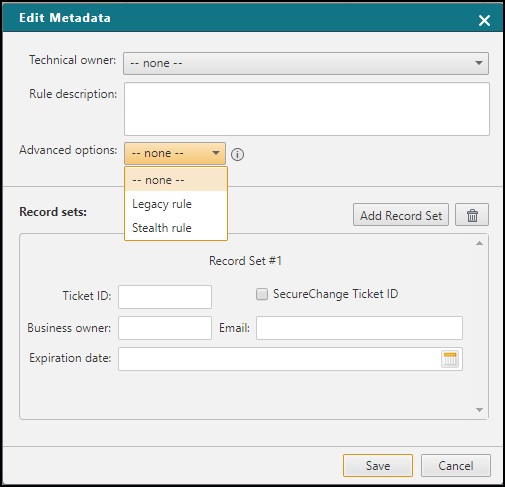
-
Technical Owner and Rule Description:
If you are a SecureTrack administrator, you can select a SecureTrack user from the list. If more than one rule is being edited, this will be disabled.
-
Advanced options:
-
Legacy rule - When a rule is marked as legacy, SecureChange Designer will treat a rule marked as legacy as a shadowed rule when making recommendations, and SecureChange Verifier will ignore a rule marked as legacy when verifying access.
Marking rules as legacy can be used to let you methodically replace overly permissive rules over a period of time. Only rules that have an Allow action will be considered by Designer as legacy.
When the traffic in an access request is fully or partially implemented by traffic that is handled by legacy rules, Designer locates the recommended rules above the related legacy rule with the highest position in the policy.
-
Stealth rule – When a rule as is marked as stealth, SecureChange Designer recommendations will place any new rules recommended for an access request below the stealth section of the policy. Only rules that have a Deny action will be considered by Designer as stealth.
The stealth section is comprised of all rules above and including the last rule marked as stealth in the device policy and is therefore always the top section in the device policy. Stealth rules can be used to protect a firewall device from attack by denying unwanted access to specific firewalls.
-
Ticket ID, SecureChange Ticket ID, Business Owner, Email, Expiration Date: Enter the Ticket ID to associate with the rule. Select SecureChange Ticket ID if the Ticket ID is from SecureChange, and the ID will display in the Policy Browser as a hyperlink to the specified ticket.
-
 : Click Add Record Set to additional Ticket IDs to this rule.
: Click Add Record Set to additional Ticket IDs to this rule.
For devices that support hierarchical structures and management of grouped entities, Policy Browser does not display propagated Legacy or Stealth Rules for the devices that are lower in the hierarchy.
To determine whether a device that is lower in the hierarchy includes a Legacy or Stealth Rule propagated from higher up, SecureTrack users should search for the level at which the Legacy or Stealth Rule was defined. The level of each rule is displayed in the Policy Browser, in the Rule Location column.
Designer takes the propagated Legacy or Stealth Rules into account for the managed devices that are lower in the hierarchy when suggesting changes and when provisioning. With Legacy rules, Designer will not create new rules on lower level entities that intersect with the legacy rule.
-
-
Click Save.
