On This Page
Configuring Check Point Syslogs - Non-Encrypted
First see Configuring Check Point Syslogs.
In R22-2 PGA.0.0 , you can receive Check Point Syslogs over UDP or non-encrypted TCP only. From R22-2 PHF1.0.0 ,TCP must be encrypted - see Configuring Check Point Syslogs Over Encrypted TCP .
Configure SecureTrack to Retrieve Audit/Traffic Logs
- Add to SecureTrack the first management server and its associated Log Server or CLM.
- In the Device Configuration list, select the relevant management server (not the log server).
- Click Edit configuration:
- Click Next and Next.
- In the stage 3 page, select Custom.
-
Set your Check Point device to communicate with SecureTrack by syslog:
Select Custom > Syslog Authentication.
Enter the log ID from the Check Point log exporter.
Select Protocol.
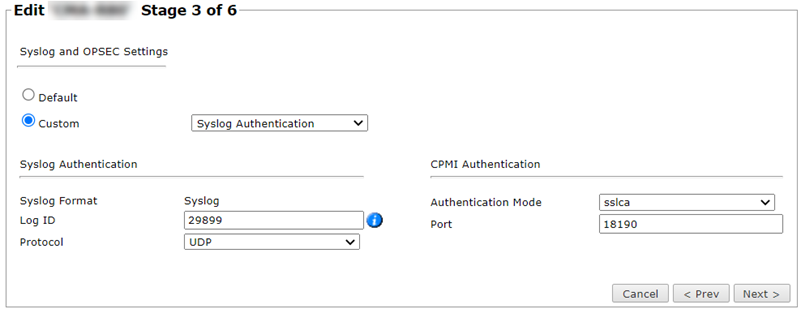
- Click Next, and then Save.
How Do I Get Here?
In SecureTrack, go to Monitoring ![]() > Device Groups
> Device Groups
