On This Page
Using User Identity in TOS
Overview
User Identity allows you to use LDAP groups in the Source field of an access request, giving you next-generation firewall (NGFW) capabilities in your Access Request workflow. For example, if you want to define an access request between the Human Resources department (hr_dept) and a site with sensitive personnel information, you can assign an LDAP group that includes the Human Resources department personnel to the Source field.
In SecureChange, all Access Request workflow automation tools support User Identity, including Auto Suggest Target, Risk Analysis, Designer, and Verifier. In SecureApp, you can use LDAP groups in the Source field when defining a connection.
User Identity is implemented for all devices supported by TOS. For devices that natively support using LDAP groups in firewall rules (Panorama Advanced, FortiManager, and Check Point), the workflow automation tools will use the LDAP groups listed in the Access Request. For all other devices, the workflow automation tools will use the predefined Users Networks zone. The Users Networks zone contains all subnets from where users connect to your network. (See Managing the Users Networks Zone.)
Tufin REST API supports using User Identity in Access Request tickets.
Prerequisites
-
Configure SecureTrack to connect to the LDAP directory that you want to use for User Identity. See Configure User Identity.
-
For devices that do not natively support using LDAP groups in firewall rules, configure the Users Networks zone with all IP addresses or subnets from which users connect to your network. (See Managing the Users Networks Zone.)
Create an Access Request
The requester can add LDAP groups in the Source field of an Access Request. These groups appear as @<name of the LDAP group>, for example @auto.adminGroup. Hover on the LDAP group to see the Distinguished Name (DN) that uniquely identifies the entry.
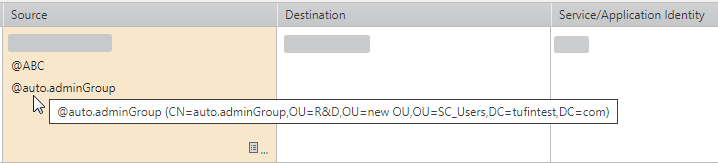
You can either select the LDAP group from the Object Browser or type the group name in the Source field using free text. API users can add LDAP-related fields in POST and PUT requests.
If the Source field contains both an IP address and an LDAP group:
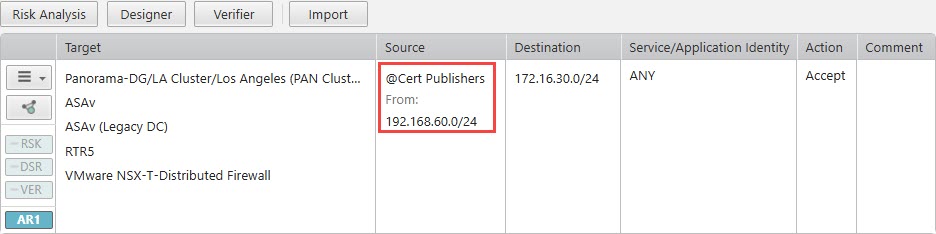
-
Devices that support User Identity (Panorama, Fortinet):
-
Path analysis calculations will only include the IP address.
-
Designer will suggest creating or editing rules that include both the IP address and the LDAP group.
-
Verifier will find matching rules that include both the IP address and the LDAP group.
-
Risk analysis will include both the IP address and the LDAP group.
-
-
Devices that do not support User Identity: Automation tools (Designer, Verifier, Risk Analysis) and the Topology Map will only use the IP address because User Identity is not supported.
Add LDAP Group Using Object Browser
-
In a SecureChange access request ticket, click the Object Browser icon in the Source field.
The Advanced Options window appears.
-
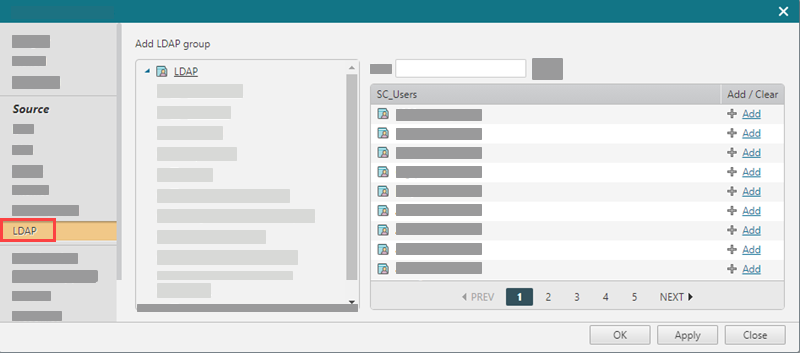
In the Source list, select LDAP.
-
Click Add for each LDAP group that you want to add as a source in the access request.
-
Click OK.
Add LDAP Group Using Free Text
-
In the Source field of an access request, type
@<name of the LDAP group>(for example@hr_dept). - Click OK.
Add LDAP Group Using API
In POST and PUT requests for API Ticket objects, you use the ldap_entity_name, ldap_entity_id, or ldap_entity_dn fields in the SourceDTO object. SecureChange verifies these values, and if they are valid, the LDAP group appears in the access request.
You can also retrieve these values in a GET request. See the SourceDTO object in the API Ticket documentation.
Handle an Access Request
The handler sees the LDAP groups specified by the requester in all steps of the workflow that contain the Access Request field.
(for example, @hr_dept)
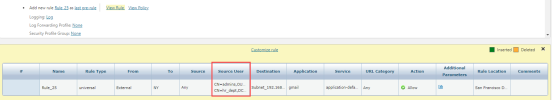
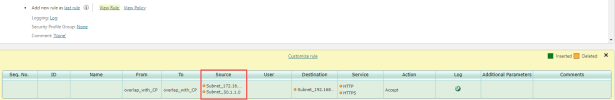
For devices that support native LDAP in firewall rules (Panorama Advanced, FortiManager, and Check Point), TOS automation tools resolve the LDAP group to the DN name from the LDAP directory. For example, in Designer:
For all other devices, TOS automation tools resolve the LDAP groups to all of the subnets listed for the Users Networks zone. For example, in Designer: