On This Page
Text Formats for Access Requests
Overview
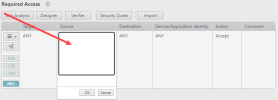
When building a traffic connection for an access request you can use the free text field to add objects to the ticket.
Text Formats for Adding Objects
User
Enter a username.
Source and Destination
Enter one of the following:
-
Host: Enter an IP address without a netmask. For example:
192.168.1.1or2001:db8::ff00:42:8329or::ffff:192.0.2.128 -
Network: Enter an IP address and netmask or CIDR. For example:
192.168.1.0/255.255.255.0;192.168.1.0/24;2001:db8::/48 -
Range: Enter a range of IP addresses. For example:
192.168.1.0-192.168.1.255or2001:db8::-2001:dba:: -
Host or network with NAT: Enter the IP address and netmask with the NAT address and netmask. The NAT information is shown below the entry but is not used in Verifier or Designer calculations. For example:
192.168.1.1 nat 10.1.1.1or192.168.1.0/24 nat 10.1.1.0/24or10.0.0.1 nat 3001::A00:1 -
DNS: Enter a DNS name. After you click outside of the entry field, you can hover over the DNS name to see the resolved IP address.
-
Object: Enter the device and object name, the Internet, or ANY. For example:
ASA/hostorInternetorANYThe Internet object includes all public IP addresses except for addresses that are defined in other SecureTrack zones. If you do not have SecureTrack zones defined then the Internet zone is treated as ANY. The default IP used to calculate paths to and from the internet object is 8.8.8.8. However, this can be changed by editing the Internet Representing IP Address in the Internet zone.
-
User Identity (Source only): Select an LDAP group from the object browser or enter @ and the name of the LDAP group, for example
@dev_team. You can add multiple LDAP groups, as with any source. LDAP groups in all LDAP servers must have unique names.For supported devices, SecureChange includes the LDAP groups in Designer and Verifier results for User Identity.
For other devices, SecureChange provides risk results for LDAP groups that have addresses in the Users Networks zone in the security zone matrix requirements of SecureTrack Unified Security Policy.
User identity is not supported for Multi-Domain interconnected mode.
-
URL Category (Supported for Palo Alto devices, Destination only): Enter the prefix UC: and then the name of the URL category. URL categories are case sensitive. If you are adding multiple URL categories, use line breaks to separate them.
Example
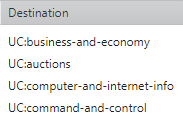
Destination fields containing URL categories cannot contain other network objects (such as IPs, subnets, or internet objects).
Service/Application Identity
Enter one of the following:
-
Service: Enter the name of a predefined service, the protocol and port of a service, or ANY. For example:
httportcp 80orANY -
Application Identity: Enter the name of an application identity (NG application/application aware).
Action
Select Accept, Drop, or Remove.
How Do I Get Here?
SecureChange > ![]() Workflows
Workflows