On this page
Monitoring Zscaler Internet Access (ZIA)
Overview
TOS monitors Zscaler Internet Access (ZIA) platform for policy revision changes.
To see which TOS features are supported for your device, review the SecureTrack Features by Vendor.
Add a device
-
Select Zscaler > ZIA Cloud Firewall.
-
Configure the device settings:
-
Device Type: Zscaler ZIA Cloud Firewall (filled automatically)
-
Name for Display
-
ST server: Select Central or RC (Remote Collector)
-
Usage Analysis: Select the relevant options:
-
Collect traffic logs for rule usage analysis
-
Collect traffic logs for object usage analysis
-
Enable Rule Optimizer Recommendations: Select to collect and save traffic usage data for Rule Optimizer recommendations.
Enabling Usage Analysis for unused rules and objects requires configuration in Zscaler. See Configuring Zscaler to Send Log Data to TOS. -
-
Enable Topology: Collects routing information for building the network Map.
-
-
Click Next.
-
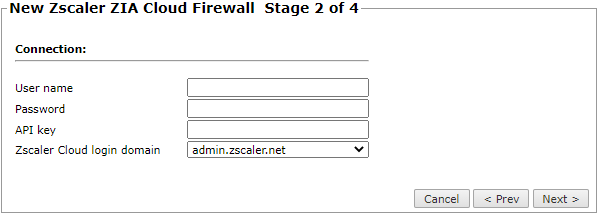
Enter the following connection information:
-
User name
-
Password
-
API key: To obtain an API key, see https://help.zscaler.com/zia/getting-started-zia-api.
-
Zscaler Cloud login domain: We recommend monitoring Zscaler from a production domain. Monitoring from a beta domain may lead to unstable behavior.
-
If you connect to the device with a proxy server, select Proxy and enter the HTTPS Proxy Hostname or IP, Port, Username, and Password.
-
-
Click Next.
-
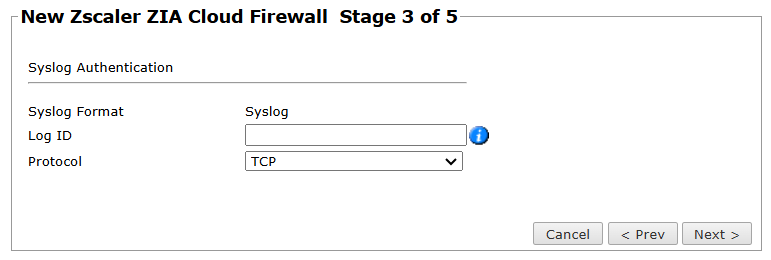
Enter the Syslog Authentication information:
-
Log ID: Unique ID (for example, TOS) that matches the value in the feed output format of the NSS Feed. This match insures that TOS will recognize the syslog and analyze it correctly with the relevant Zscaler device - see Configuring Zscaler Syslogs.
-
Protocol: Select TCP or UDP to determine the port that will be used to transfer syslog information.
TCP: Use this value if Zscaler sends syslogs directly.
UDP: Use this value if the syslogs are forwarded to TOS using an external source like an SIEM server.
-
-
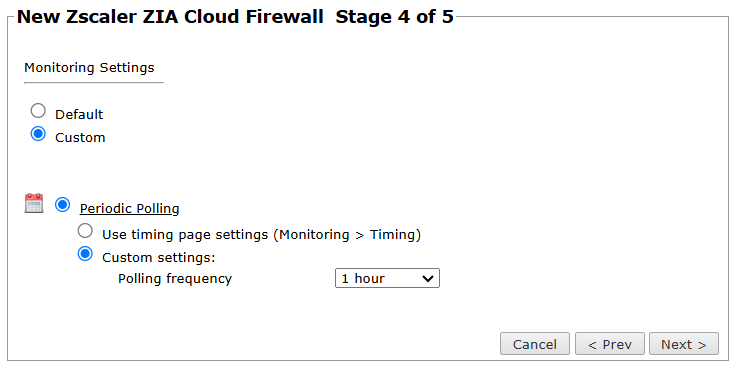
In Monitoring Settings, do one of the following:
Select Custom and configure the monitoring mode and settings.
- Periodic Polling, select Custom settings and set the Polling frequency - this is how often TOS fetches the policy from the device. We recommend setting the polling frequency to 1 hour, due to rate limitations of the Zscaler API.
-
Click Next.
-
Click Save.
The Zscaler ZIA Cloud Firewall device now appears in the Monitored Devices tree.
Configure a monitored device
After you add a device, further configuration options are available.
Options vary depending on your environment.
-
Edit configuration: Use the wizard to modify selected device settings. See Add a Device in this topic.
-
Delete this device: Type yes to confirm that you want to delete the device.
-
Migrate (ST servers): Available in distributed deployments. Select the server where the device will be monitored and click Migrate.
-
Migrate (Domains): Available in multi-domain deployments. Select the domain where the device will be monitored and click Migrate.
How do I get here?
SecureTrack > Monitoring ![]() > Manage Devices
> Manage Devices
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague