On This Page
Viewing General, Violation and Shadowing Information
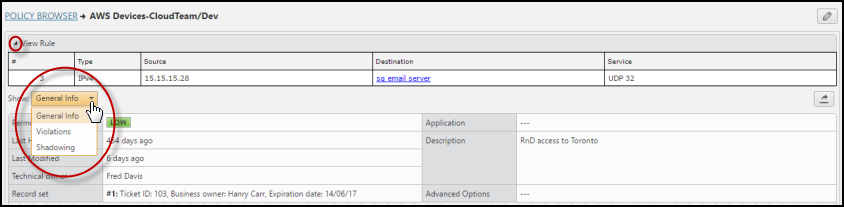
When you click on the rule details (![]() ) for a rule in Policy Browser you can see a more detailed view of any rule. The rule is shown at the top of the page.
) for a rule in Policy Browser you can see a more detailed view of any rule. The rule is shown at the top of the page.
Below the rule is a menu that shows the following three groups of information you can view:
- General - In this section you can see:
- Permissiveness level (high/medium/low) – An indication of how widely a rule is defined, for example:
- A rule with one source host, one destination host and one service is low permissiveness
- A rule with Source "ANY", Destination "ANY" and Protocol "ANY" is high permissiveness
Rules with high permissiveness can be a security risk because they allow too much access through the firewall. N/A indicates that the platform is not supported for permissiveness calculations.
- Last hit for rule - How many days ago the device received traffic that matched the rule
Policies need to have unique names. If there are multiple policies that share the same name, rule hits will not be mapped correctly to these policies.
- Last hit for users (Palo Alto only) - How many days ago the device received traffic that matched a user that is specified in the rule
- Last hit for application identities (Palo Alto only) - How many days ago the device received traffic that matched an application identity that is specified in the rule
- Last Modified - The last time a revision showed that the source, destination or service changed in the rule, including changes group members
After you upgrade to R16-4 or higher, SecureTrack analyzes the revisions to identify the last time any part of the rule was changed, for example source, destination, service, log, or comment. Rules are labeled with the last modified date of yesterday, 3 months ago, 6 months ago, 12 months ago, or longer, whichever is the most recent change. This process can take up to a few days to complete.
- Technical owner - Typically, the firewall administrator who is responsible for the technical accuracy of the rule
- Record sets - The business details of the rule including the business owner (person responsible for the business needs for the rule), email address of the business owner, ticket IDs associated with the rule, the expiration date when the business need for the rule is no longer valid
- Application - The application in SecureApp that is associated with the rule
If the rule is IPv4 only, it is associated with an application when the topology of the SecureApp connection matches the rule. If the rule uses IPv6 addresses, it is associated with an application when the target selected for the SecureChange ticket created from the connection matches the rule.
- Rule description - The description of the rule entered into Policy Browser
- Permissiveness level (high/medium/low) – An indication of how widely a rule is defined, for example:
- Violations - In this section you can see the violations caused by the rule as they are shown in the Violations browser:
- Severity - The level of severity of the violation as defined by the severity of the security requirement
- Creation Date - The date and time the violation first occurred
- Violations - The traffic allowed by the rule that violates the security requirement
- Security Requirement - The requirement that governs the traffic allowed by the rule
- Shadowing - In this section you can see any rules that shadow the selected rule
What can I do on this page?
- Hide the rule - Click
 to hide the rule details, which gives more space for the additional information thta may be available.
to hide the rule details, which gives more space for the additional information thta may be available. - Export - Click
 to export the details of each group to a supported format, such as PDF or CSV.
to export the details of each group to a supported format, such as PDF or CSV. - Edit the Metadata - Click
 to edit the metadata for this rule.
to edit the metadata for this rule.
How Do I Get Here?
To view the additional information about a specific policy:
- In SecureTrack, click Home > Policy Browser.
- Click
 on the desired rule.
on the desired rule.
