On This Page
Violations Browser
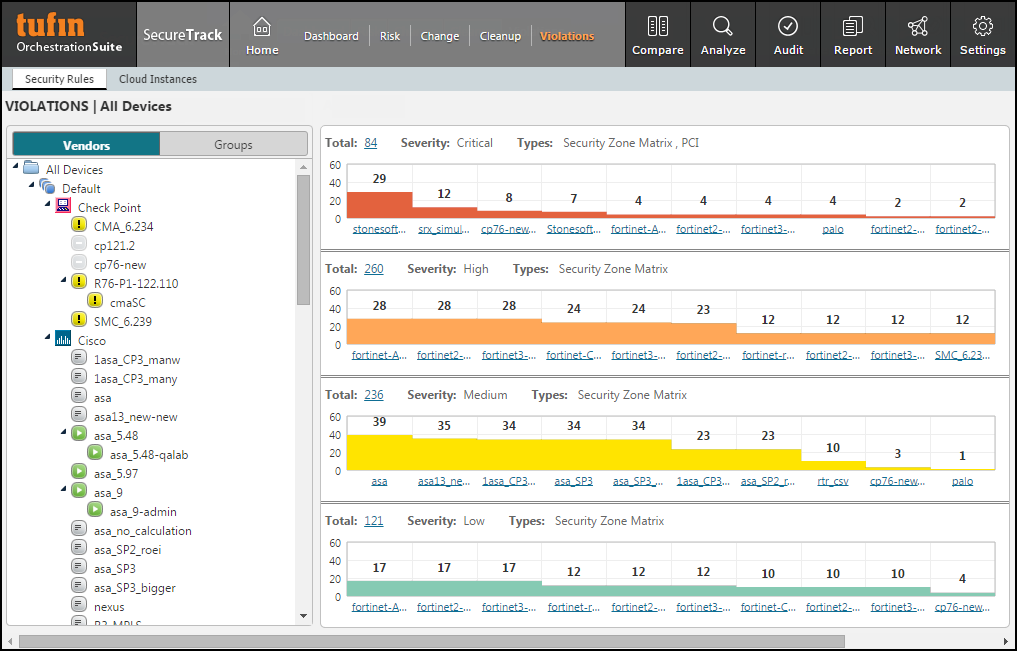
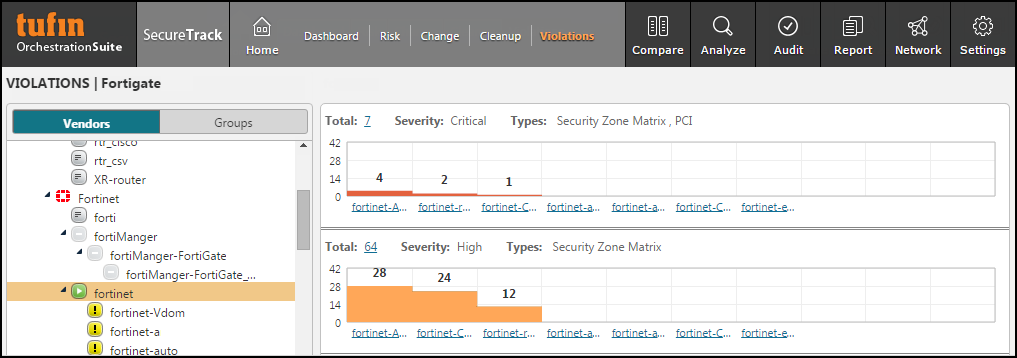
The Violations browser lets you see at-a-glance the security compliance violations in your network by device.You can drill-down to see the exact rules that cause the violations, as well as suggested ways to remediate the violations.For management platform devices, the violations are shown at the level in the hierarchy in which the violation can be resolved.
Violations are calculated when the USP or PCI policy is changed, when devices in the USP or PCI policy are changed, or when the Interactive Map is synchronized, either automatically or manually.
SecureTrack uses these compliance requirements to determine the violations:
- Security Rules
- Security zone matrix requirements configured in Audit > Compliance > Unified Security Policy
- PCI DSS policies configured in Settings > Configuration > Regulations(Only critical violations)
- Cloud Instances
- Cloud tag policy requirements configured in Audit > Compliance > Unified Security Policy (Only critical violations)
You can select a single device to show the revisions for that device, or you can select a group of devices from the tree to show the recent revisions for all of the devices in the group.
IPv6 is not supported for this TOS feature.
Note: Security Groups are currently not displayed in the Violations Browser.
What can I do on this page?
- Violations Browser Summary - Click on violations total to view a summary of all violations.
- Violating Rules - Click on the device name or violations bar of a device to view the violating rules of that specific device.
How Do I Get Here?
To view the Violations Browser:
- In SecureTrack, click Home > Violations.
