On This Page
TufinMate Security Overview
The purpose of this document is to explain exactly how TufinMate interacts with your network information and provides it to end users in a limited and secure manner.
-
Customer data is not used to train or develop the TufinMate application.
-
Data is encrypted at rest and in transit.
-
Access to the TufinMate application can be restricted using multiple mechanisms.
Architecture Overview
TufinMate creates an integration between Microsoft Teams and Tufin Orchestration Suite to relay queries about network topology and access flows; as well as to open SecureChange access requests.
The flow operates as follows:
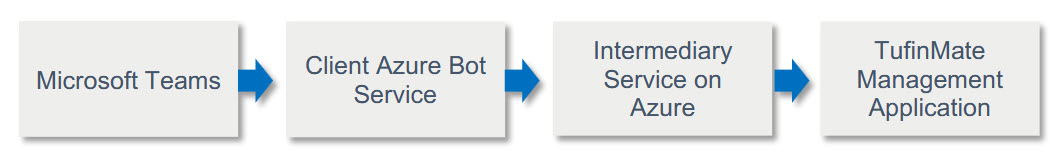
The TufinMate application is comprised of three main components:
-
TufinMate Management Application:Backend operations are handled by the TufinMate Management Application (TMA) installed on your Tufin cluster along with the other Extensions applications. All configuration tasks are handled in the TufinMate Management Application, including user permissions and selection of the SecureChange workflow used for access requests.
The Management App includes multiple settings used to configure the integration between Tufin with Microsoft Teams and generates a Teams plugin unique to your organization using the requested parameters.
On the backend, the management app includes the Natural Language Processing model used to interpret the end user’s question and populate the response.
-
Azure Secure Relay Service: TMA requires an outbound connection and uses a secure message relay service to interface with Microsoft Teams in the cloud. This service (named chatbot.tufin.com) runs on Tufin-hosted Azure infrastructure, but there is no server or database used to store this information. The service passes it through from one side to the other. Each customer’s messages are isolated, and the configured Tenant ID and Bot Service ID ensure that customer data is not transmitted to the wrong environment.
Microsoft Azure adheres to industry standard security, privacy, and compliance controls. To learn more about Azure security and privacy policies visit: Azure Compliance Documentation.
-
Microsoft Teams Application
An app (or plugin) unique to your organization is generated by the TufinMate Management Application. This plugin is installed on Microsoft Teams. End users interact with the TufinMate solution from the chat window in Teams.
You can view an architecture diagram for this structure in Appendix A.
Data Confidentiality: Rest and In-Transit Security Measures
LLM Training Data
TufinMate uses an open-source Large Language Model (BERT) to interpret end users' questions and generate a response. The LLM model Tufin uses was not trained on public data sources like the internet, nor was it trained on customer data. All data used to train the model was generated by Tufin.
TufinMate does not continue to train on new queries submitted by end users. TufinMate does not use generative AI to create responses to end user questions.
Encryption At Rest and In-Transit
-
TufinMate uses encryption in alignment with industry best practices.
-
Messages between Microsoft Teams and Tufin are encrypted in transit.
-
The TufinMate architecture has been verified by a 3rd party to meet certain security standards. Further details available on request.
Data Retention
End user conversations with TufinMate are stored in the Microsoft Teams chat history as well as locally in the TufinMate Management App database. If enabled, TufinMate has a feature to send the end user a PDF report of a specific topology path. These are delivered directly to the OneDrive account of the end user and are secured by OneDrive encryption. Microsoft Teams controls all the privacy controls on these end user conversations. The permissions model within your Microsoft Teams tenant can help ensure that data won't unintentionally leak between users, groups, and tenants. To learn more about Teams messaging controls and policies visit:
Conversation history stored on the TufinMate management app is accessible to the Tufin administrator.
If enabled, TufinMate has a feature to send the end user a PDF report of a specific topology path generated by Tufin API’s. These are delivered directly to the OneDrive account of the end user and are secured by OneDrive encryption.
Regulatory Compliance Requirements
Tufin is committed to protecting your data, and maintaining privacy compliance is our top priority. With customers in nearly every country in the world, Tufin welcomes the positive and continuous development of global privacy regulations. We constantly follow these changes, and we are mindful about what data we process and how we protect it. This applies to the AI tools we offer as part of the Tufin product suite.
To learn more about Tufin’s privacy policies visit: Privacy Center.
Access and Authorization
TufinMate is only accessible from Microsoft Teams. Teams enforces team-wide and organization-wide two-factor authentication, single sign-on through Active Directory.
For more information about Microsoft Team’s security practices, please visit: Security and Compliance in Microsoft Teams.
There are two ways administrators can restrict access to TufinMate:
-
Restrict Access from Teams
Limit which users can access the plugin from Microsoft Teams.
-
Require Secondary Verification
You can configure TufinMate to restrict access to users who have a SecureTrack or SecureChange account. With this option, TufinMate will look for a match between the Microsoft Active Directory user and the First Name, Last Name, and Email Address of a user account in Tufin. TufinMate does not request, receive, store, or retain end user credentials.
A verification service allows TufinMate to connect directly with your Tufin environment rather than importing end user account and transaction data via an aggregator.
End User Permissions
Tufin Administrators can restrict the level of detail different users can ask TufinMate to provide. For example, the ability to generate a topology report with device details and a topology map can be restricted to verified TOS users or prohibited altogether.
To learn more about this functionality, visit: TufinMate User Permissions.
AI Privacy and Security FAQs
TufinMate uses a Natural Language Processing service to interpret questions from end users and return responses on a limited range of topics.
What type of AI does TufinMate use?
TufinMate uses an open-source LLM model (BERT) to interpret natural language questions within a range of supported conversation flows.
-
It does not use machine learning to train on new prompts or questions from end users.
-
It does not use generative AI to return the response.
Is TufinMate built from open-source code or components?
TufinMate uses the open-source program BERT to build the Natural Language Processing algorithm it uses, but the data set used to train the model is uniquely created and owned by Tufin. The TufinMate application code is owned by Tufin and only Tufin personnel can access it. Only Tufin customers can download and install the application. Like the rest of the Tufin product suite, the TufinMate Management App user interface is created using open-source libraries such as Material UI.
Does Tufin use customer data to train the TufinMate NLP model?
No. No customer data was used to create the NLP model used by TufinMate.
Does TufinMate use machine learning to adapt its responses or functions?
No. TufinMate completes a limited number of functions including answering end user questions about network access flows. It does not use machine learning.
Is the application tested for accuracy of output or biases?
Yes, the application has undergone a rigorous QA testing process to verify accuracy of responses.
What dictates whether the AI has access to sensitive data or assets?
TufinMate uses multiple Tufin API’s to populate templated responses to end users. The Tufin administrator is in full control of enabling this API access.
Appendix
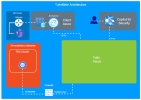
A. TufinMate Architecture
On-premises networks: Tufin implementation under the customer’s responsibility.
Tufin Azure: Intermediary message relay service under Tufin’s responsibility. See Azure Relay Service in Architecture Overview in this document.
Client Azure: This is the bot service your Microsoft administrator creates during the TufinMate setup process. This service is under the customer’s responsibility.
MS Teams Gateway: Microsoft Teams instance under the customer's responsibility.
B. Data Elements Used
TufinMate message transactions include the following information:
(1) Azure Tenant ID
This is required to know which customer system to send the data back to.
(2) Unique Bot ID
This is generated by Teams. Together with the Tenant ID this allows the app to identify the TOS system you want TufinMate to use (i.e. Dev, Prod).
(3) Message
This is the user's question and the formulated response. This may include:
-
IP's and services
-
Network topology reports
-
Network access flows and policy configurations
All the functions described below can be fully disabled or restricted to users with a TOS account. Configure this on the Permissions page in the TufinMate Management App.
-
Yes/No answers on whether access between two end points is permitted.
-
A list of network security devices along a network path.
-
A PDF report of the network topology path between two end points.
-
Users with a SecureChange account can open a SecureChange ticket.
(4) Recipient ID
This is used to return the response to the relevant end user.
(5) Conversation ID
Sustains the ongoing conversation thread.
(6) User Email, First Name, Last Name
Used to verify if the user has a TOS account.
(7) Timestamp and Channel Metadata