On this page
Configuring Check Point for Non-Encrypted Syslogs
|
|
This topic is intended for TOS Administrators. |
Overview
The syslog mechanism is used to pass policy change and traffic information from your devices to SecureTrack. For Check Point devices, you can configure syslogs, non-encrypted over UDP, as described here, or encrypted over TCP.
Non-encrypted syslog configuration for Check Point includes configuring:
To configure encrypted syslogs, see Check Point Syslogs over encrypted TCP. For general information about sending syslogs to TOS, see Sending Additional Information using Syslog.
Syslog processing methods
TOS supports two methods of processing syslog information for Check Point devices:
-
Original method (default)
-
The Automatic Policy Generator (APG) and in the Rule and Object Usage reports display rule usage.
-
The SecureTrack Reporting Essentials (STRE) reports do not display objects.
- The Rule Viewer displays last-hit information only for rules (not for objects in rules).
-
-
New method
Tufin Support might advise switching to the new method if you have a large volume of syslog traffic and have experienced performance issues.
On switching to the new method, all existing last-hit information is cleared and reinitialized.-
The Rule Viewer displays last-hit information for both rules and objects in rules.
-
The STRE reports includes objects.
-
The following are not available:
-
Automatic Policy Generator
-
Rule and Object Usage report
-
-
Configure Syslog processing method
-
Switch to the new method:
-
Switch to the default method:
Configure SecureTrack to retrieve audit/traffic logs
Configure the log exporter on all monitored MDSM CMA, SMC and CLM log server devices.
-
Add to SecureTrack the first management server and its associated Log Server or CLM.
-
In the Device Configuration list, select the relevant management server (not the log server).
-
Click Edit configuration:
-
Click Next and Next.
-
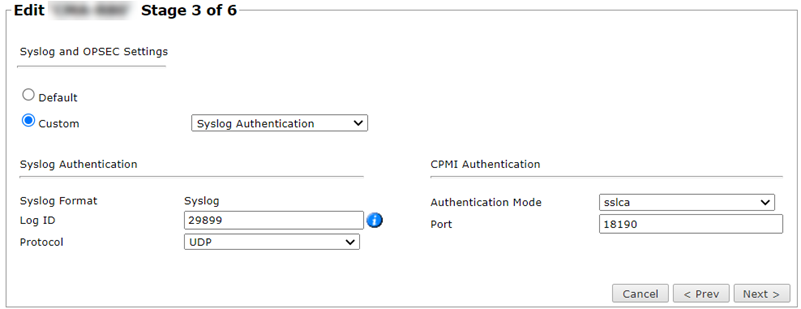
In the stage 3 page, select Custom.
-
Set your Check Point device to communicate with SecureTrack by syslog:
Select Custom > Syslog Authentication.
Enter the log ID from the Check Point log exporter.
Select Protocol UDP.
-
Click Next, and then Save.
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague