On This Page
Access Regression Report
Overview
The Access Regression report is a change report that lists effective policy changes. The Access Regression report is similar to the Comparison report (Compare > Generate Report), in that it compares specified revisions of the same policy; however, whereas the Comparison report compares configuration changes, the Access Regression report calculates the effective policy for each revision, and displays effective changes to traffic handling. For example, if an object's definition is changed, the Comparison report will show only that one change; the Access Regression report will show all the resulting effective changes caused by the object's appearance in any part of the policy.
The report lists all newly blocked traffic (possible business continuity regression), followed by all newly allowed traffic (possible security regression). For each change, the report specifies the rule that previously handled the traffic, and the rule that currently handles the traffic.
The Access Regression report is only for Check Point policies. It can be used for 'what if' analysis by saving a policy change without installing it, and then running the report.
In the Access Regression report results, traffic patterns that are newly blocked by changes to the same rule, and were previously handled by the same rule, are consolidated into one row; the same is done for newly-allowed traffic. As a result, such a row may contain multiple Sources, Destinations, and Services, but the effective change is only relevant to some of the traffic combinations of these Sources, Destinations, and Services.
Configure and Generate an Access Regression Report
-
Log into SecureTrack as an Administrator.
-
In the address bar of your browser, add
/toolsto the SecureTrack base URL.For example:
https://192.168.1.1/tools -
Click Access Regression Test.
The tool appears:
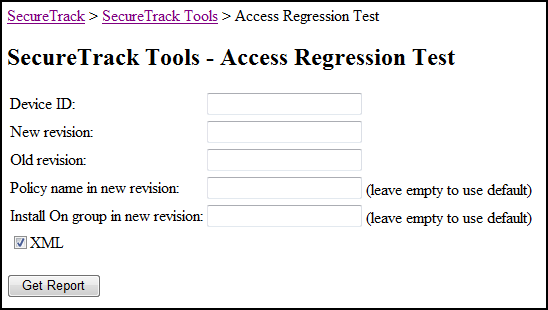
-
Enter the Device ID of a monitored device.
To get the ID of a device, in SecureTrack:
-
Navigate to Monitoring > Manage Devices.
- Click any device in the device tree.
-
Type the letter "t".
The ID appears for all devices.
-
-
Enter the numbers of the revisions to analyze.
The revision numbers are shown in the revision table in Compare.
-
You can enter the policy package name.
The policy package name are shown in the revision table in Compare.
-
To analyze only Check Point rules configured for specific targets, type SecureTrack's ID number for an Install On Group. For assistance in obtaining this number from SecureTrack's database, please contact Tufin support.
- For a regular HTML report, keep XML clear.
- Click Get Report.
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague