On this page
Monitoring Amazon AWS Cloud Platform
Overview
Add AWS accounts to TOS as devices to monitor and manage them. By adding AWS accounts, TOSmonitors the Amazon AWS cloud platform for policy revision changes and provides ongoing visibility into configuration and compliance.
To see which TOS features are supported for your device, review the SecureTrack Features by Vendor.
Add AWS accounts
There are two ways to add AWS accounts as devices:
-
Manually
Add every AWS account individually, as described here in Add a device.
-
Automatically
Configure a Cloud Organization and import its accounts according to a predefined schedule. Automatic account import settings are included as part of the Cloud Organization configuration. For detailed information, see Cloud organization device groups.
Opt-in regions limitation for cloud organizations
SecureTrack cannot discover AWS opt-in regions when you use cross-account access (AssumeRole/ARN), including when monitoring accounts through a Cloud Organization.
To monitor resources in these regions, add the AWS account manually and use direct account credentials.
This limitation will be resolved in a later version.
For more information about AWS opt-in regions, see the AWS documentation.
Account authentication
For TOS to authenticate with and monitor the AWS account, you need the account credentials. When adding a device, you can configure credentials in one of the following ways:
-
Associate with a predefined Cloud Organization
If you have configured Cloud Organizations, you can associate the AWS account with the Cloud Organization to inherit its credentials.
-
Access Key ID and Secret Access Key
Define the Access Key ID and the Secret Access Key for the specific account.
Additional authentication mechanisms
For devices not associated with Cloud Organizations, TOS also supports service-specific authentication mechanisms, such as integration with HashiCorp Vault. These mechanisms require specific credentials.
See Prerequisites for AWS accounts.
Prerequisites for AWS accounts
Permissions
Before you begin, make sure the AWS user or role used by SecureTrack has a custom IAM policy with the minimum required permissions. These permissions allow SecureTrack to retrieve configuration and flow information needed for monitoring, topology mapping, provisioning, and application discovery.
Cross-account access (AssumeRole): To use the AssumeRole option for cross-account monitoring, you must have an Amazon Resource Name (ARN) identifier for the target role. For more information, see Amazon AWS AssumeRole Support.
To create a custom IAM policy, copy the relevant permissions into the Action block of your policy and set "Resource": "*" unless more restrictive access is required. For more help, see the Amazon AWS documentation.
Use the following permission blocks based on the features you want to enable:
These permissions allow SecureTrack to collect details about network components such as instances, security groups, subnets, interfaces, routes, and transit gateways.
VPC and Security Groups
ec2:DescribeRegions
ec2:DescribeVpcs
ec2:DescribeInstances
ec2:DescribeNetworkInterfaces
ec2:DescribeVpnConnections
ec2:DescribeSubnets
ec2:DescribeAddresses
ec2:DescribeRouteTables
ec2:DescribePrefixLists
ec2:DescribeCustomerGateways
ec2:DescribeVpnGateways
ec2:DescribeVpcPeeringConnections
ec2:DescribeSecurityGroups
ec2:DescribeInternetGateways
ec2:DescribeNatGateways
These permissions allow SecureTrack to retrieve network topology data used to build the network map and perform path analysis.
Transit Gateway
ec2:DescribeTransitGateways
ec2:DescribeTransitGatewayAttachments
ec2:DescribeTransitGatewayConnects
ec2:DescribeTransitGatewayPeeringAttachments
ec2:DescribeTransitGatewayRouteTables
ec2:DescribeTransitGatewayVpcAttachments
ec2:SearchTransitGatewayRoutesDirect Connect
directconnect:DescribeDirectConnectGateways
directconnect:DescribeDirectConnectGatewayAssociations
directconnect:DescribeDirectConnectGatewayAttachments
directconnect:DescribeVirtualGateways
directconnect:DescribeVirtualInterfacesThese permissions are required for automatic account import through AWS Organizations:
Account credentials
SecureTrack supports several authentication mechanisms, each of which require specific credentials.
Make sure you have the required credentials for the authentication mechanism before adding the device.
-
Account ID
Required only to associate a Cloud Organization with the device. Get the ID of the account from the AWS Identity and Access Management (IAM) console.
-
AWS Account
The Access Key ID and the Secret Access Key for the account from the AWS Identity and Access Management (IAM) console.
-
Hashicorp Vault server
Preconfigured with the following key-value pairs, which SecureTrack needs to retrieve:
Key
Value
access_key_id<Access Key ID>secret_access_key<Secret Access Key>
VPC automatic import
When you add a device, you can enable Automatic Importfor Virtual Private Clouds (VPCs). When enabled, SecureTrack automatically detects changes to the AWS environment (VPCs which were added, deleted, and updated), and reflects them in the device list and revision history. Changes to the VPCs are also reflected in the Map when a scheduled sync occurs or when you Sync the map.
When enabled, VPCs are imported at 10-minute intervals.
With Automatic Import enabled, devices that were deleted from AWS are automatically deleted from the list of devices in SecureTrack, and their history is no longer available. Therefore, if your continuous integration/continuous deployment (CI/CD) pipeline regenerates VPCs, the history of the deleted VPC will not be available in the new replacement VPC. To retain revision data in SecureTrack for devices that have been deleted from your Amazon account, use manual import.
The maximum number of VPCs for Automatic Import depends on your TOS deployment. For more information, contact Tufin Customer Support.
Add a device
Add an AWS account individually, one at a time.
Optionally associate the account with a predefined Cloud Organization for automatic import or by using the username-password mechanism. Associating a Cloud Organization with the device automatically imports the account details.
-
Do one of the following:
-
To add a device, select Amazon > AWS Account.
-
To add a Cloud Organization, select Amazon > AWS Organization.
-
-
Configure the device settings:
-
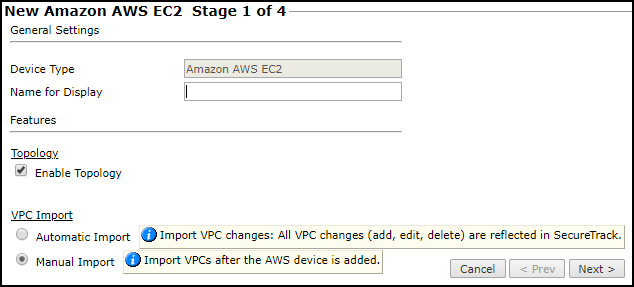
General settings
-
Name for Display
-
Domain: Available only if you have configured your system for managing multi-domains and All Domains is currently selected. Select the domain to which to add the device. The Domain can only be entered when adding a device; to change the Domain, you must migrate the device.
-
ST server: In a distributed deployment, the TOS cluster that monitors the parent device and its VPCs.
-
-
Usage Analysis
-
Collect traffic logs for rule usage analysis: Select to enable SecureTrack to analyze flow log data and identify the last hit date for rules.
When selected, uses AWS CloudWatch (the default). To use S3 flow logs instead, select Enable S3 storage explicitly for the device and configure the storage credentials. -
Enable Rule Optimizer Recommendations: Select to collect and save traffic usage data for Rule Optimizer recommendations.
-
-
Topology
-
Enable Topology: Select to collect routing information for building the network Map.
Topology options for Advanced management mode are configured when you import managed devices.
-
-
VPC Import:
-
Automatic Import: To automatically detect updated, deleted and new VPCs in the AWS account, and reflect the updates in SecureTrack. VPCs are automatically imported at 10-minute intervals.
-
Manual Import: Import VPCs after you add the AWS device.
-
-
- Click Next.
-
Configure the SecureTrack connection to the AWS device, according to the parameters required by the device:
-
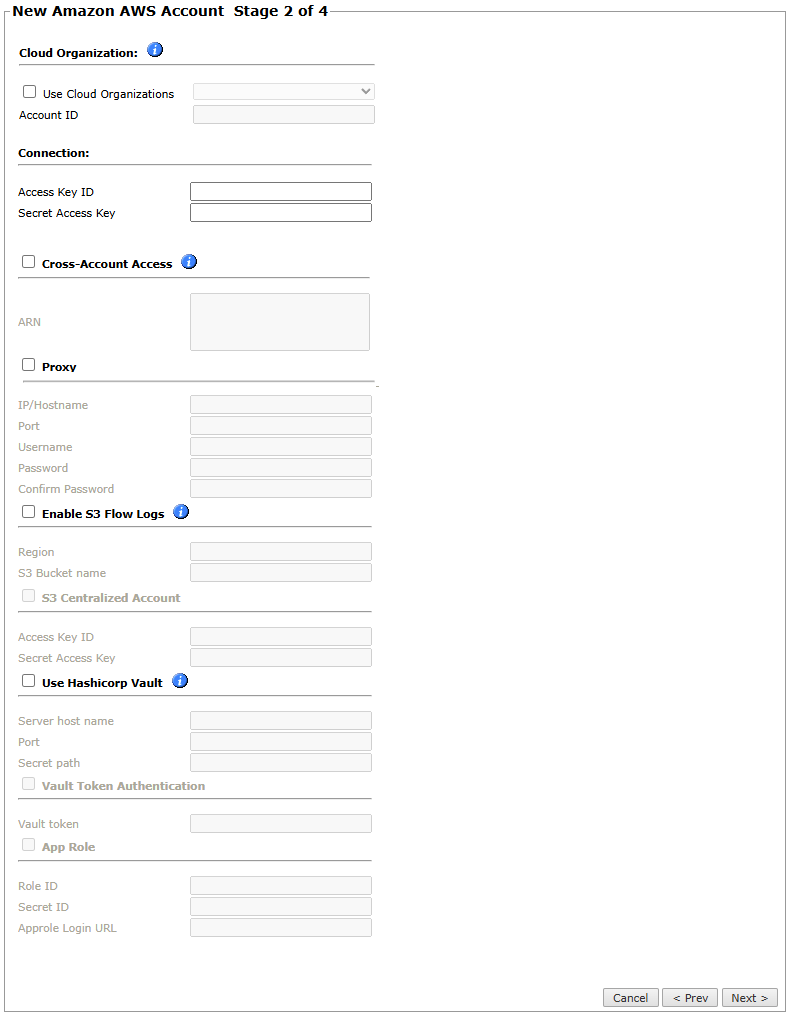
Cloud Organization
-
Use Cloud Organization: Optional. Select to associate this device with a predefined cloud organization. When associated with a cloud organization, other connection mechanisms and credentials are automatically disabled.
The Access Key ID and the Secret Access Key are automatically populated from those configured for the Cloud Organization. -
Account ID: Mandatory when Use Cloud Organization is selected. The ID of the account to associate with the device.
-
-
Connection
Connection credentials are only valid when the AWS account is not associated with a Cloud Organization.
-
The Access Key ID and the Secret Access Key for the account from the AWS Identity and Access Management (IAM) console.
-
-
Cross-Account Access
Enabled only when the AWS account is not is not associated with a Cloud Organization.
-
ARN: The Amazon Resource Name (ARN) identifier to use the
AssumeRolepermissions.This allows you to request temporary security credentials to make AWS requests for the account configuration information that is not available by default, and to access VPCs that are not part of your Account configuration.
For more information, see Amazon AWS AssumeRole Support.
-
-
Proxy:
Enabled only when when the AWS account is not associated with a Cloud Organization.
Select to connect to AWS through a proxy which requires authentication. Enter the proxy details:
-
IP address or Hostname of the proxy
-
Port that you connect to on the proxy
-
Username to use for authentication
-
Password and Confirm Password to use for authentication
From R25-2 PHF3.0.0, if the proxy performs TLS inspection, you must import the proxy’s trusted certificate into TOS before configuring the proxy. See Import a Proxy Certificate for TLS Inspection.
If the device is associated with a Cloud Organization, configure the proxy in Device Groups > Cloud Organizations, and edit the Cloud Organization Settings instead.
If SSL decryption is enabled on the Proxy server and applied to the traffic from SecureTrack to AWS, you must configure a white list on the proxy server. The white list allows the traffic from SecureTrack to bypass SSL decryption and authentication. -
-
Enable S3 Flow Logs:
To use S3 flow logs for usage analysis instead of the default CloudWatch, select this option and enter the S3 details:
-
Region
-
S3 Bucket name
-
-
S3 Centralized Account:
Enabled only when when the AWS account is not associated with a Cloud Organization..
Select this option for cross-account access, and enter the Centralized Account credentials:
-
Access Key ID
-
Secret Access Key
-
-
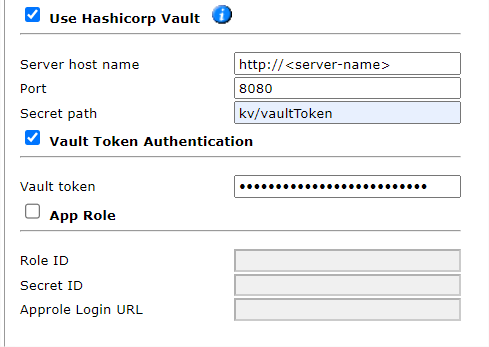
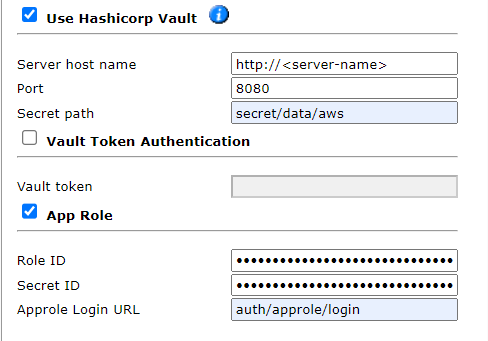
Use Hashicorp Vault:
Enabled only when the AWS account is not associated with a Cloud Organization..
Select this option to store your AWS authentication credentials in Hashicorp Vault.
When storing AWS authentication credentials in Hashicorp vault, use the KV secret engine version 1.-
Server host name: Name of the server used to host the Hashicorp Vault.
-
Port: TCP / UDP port that SecureTrack uses to communicate with the Hashicorp Vault.
-
Secret path: Path to the AWS authentication details within the Hashicorp Vault.
-
Select either Vault Token Authentication or App Role:
- Vault Token Authentication:
Select this option to add the Vault token. This token is required for SecureTrack to authenticate AWS using the Hashicorp Vault.
For example:
- App Role:
Select this option to add the App Role fields:
- Vault Token Authentication:
-
Tufin does not support using the Hashicorp Vault with a proxy or Cross-Account Access (ARN). -
-
Click Next. The Monitoring Settings page appears.
-
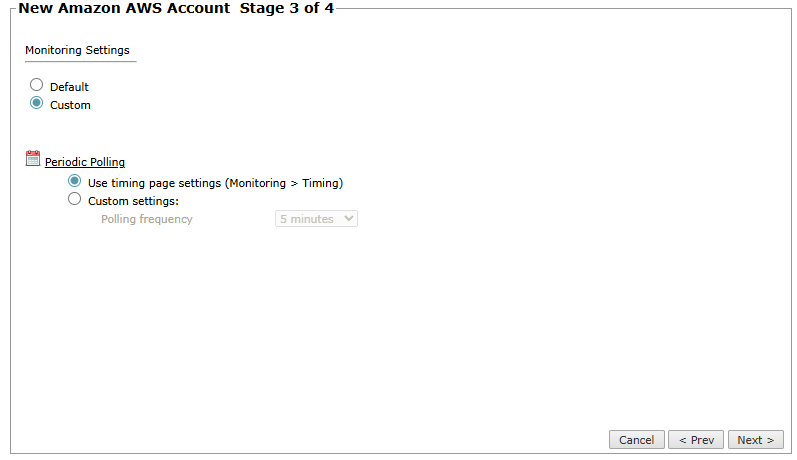
In the Monitoring Settings page, select Default or Custom monitoring settings:
- Default:
-
Custom: Define the polling frequency for SecureTrack to retrieve the configuration from each device:
-
Use timing page settings: See Setting Timing for Monitoring.
-
Custom settings: Select the required polling frequency.
If you select 1 day, you can select the exact time (hour and minute) for the daily polling.
-
-
Click Next.
-
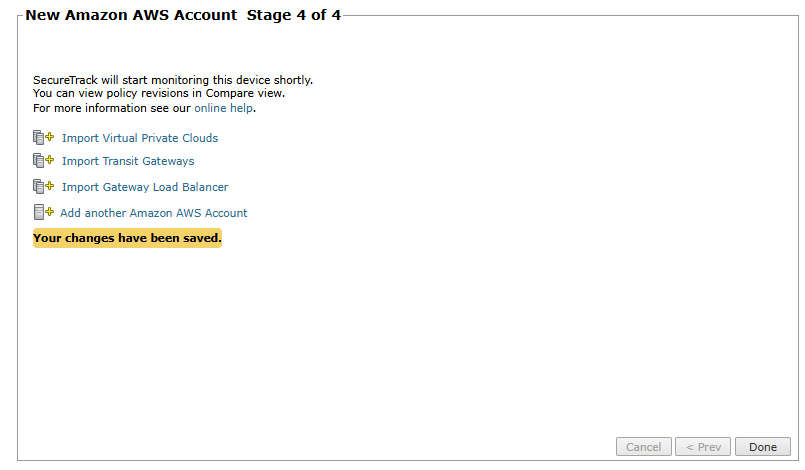
Click Save.
After adding a device, you can update its configuration settings, delete the device, or import additional settings such as VPCs, Transit Gateways, and Load Balancers.
Import AWS Gateway Load Balancers
Configure a monitored device
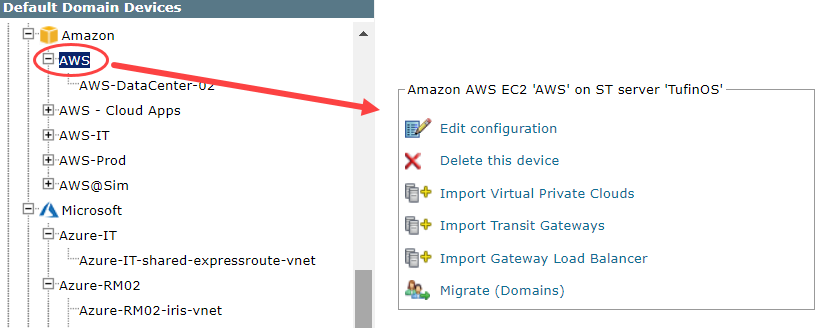
After you add a device, further configuration options are available.
Options vary depending on your environment.
Example:
-
Edit configuration: Use the wizard to modify selected device settings. See Add a Device in this topic.
-
Delete this device: Type yes to confirm that you want to delete the device.
-
Import Virtual Private Clouds: Select the Virtual Private Clouds to be added.
-
Import Transit Gateways: Select the Transit Gateways to import. In multi-domain deployments, select the domain for each Transit Gateway.
-
Import Gateway Load Balancer: Select the gateway load balancers to import. In multi-domain deployments, select the domain for each load balancer.
-
Migrate (ST servers): Available in distributed deployments. Select the server where the device will be monitored and click Migrate.
-
Migrate (Domains): Available in multi-domain deployments. Select the domain where the device will be monitored and click Migrate.
How do I get here?
SecureTrack > Monitoring ![]() > Manage Devices
> Manage Devices
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague