On This Page
Monitoring Cisco Switch Devices
Overview
TOS monitors switch devices for revision changes. For TOS to show full accountability details (who made the policy changes and when the changes were made), you must also configure the device to send syslogs.
To see which TOS features are supported for your device, review the SecureTrack Features by Vendor.
Prerequisites
Before you start, make sure that the device user account that you use for TOS monitoring has permission to run these commands:
-
Retrieve revision:
terminal no exec prompt timestamp
(use one of these commands) show running-config OR show configuration OR show startup-config
show clock
show version
show access-lists - Retrieve dynamic topology:
show ip route
show ip interface
show mpls interface detail
show ip bgp | inc IDIf BGP is used, run:
show ip bgp neighbors | inc BGP
show ip bgp vpnv4 all labels
show standby - Provisioning:
changeto system
show context
Recommendations
-
TOS and the monitored devices must be synchronized with the correct date and time, either manually or automatically. We recommend that you also configure the devices to resolve DNS queries.
Add a Device
-
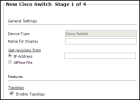
Select Cisco > Switch:
-
Configure the device settings:
- Name for Display
-
Domain: Available only if you have configured your system for managing multi-domains and All Domains is currently selected. Select the domain to which to add the device. The Domain can only be entered when adding a device; to change the Domain, you must migrate the device.
-
Get revisions from: One of the following:
- IP Address: Revisions are retrieved automatically
- Offline File: (If available) Revisions are manually uploaded to TOS for Offline Analysis
-
ST server: In a distributed deployment, select which TOS cluster monitors this device (not shown in image)
-
Enable Topology: Collects routing information for building the network Map.
Topology options for Advanced management mode are configured when you import managed devices.
Click Next.
-
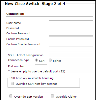
Configure the TOS connection to the Cisco device, according to the parameters required by the device:
-
Enter the authentication details needed to connect to the Cisco device.
-
Username and password: Enter the device username and password
- Enable password: Enter the password to give TOS elevated privileges on the device
-
- Connection configuration: Select whether to use SSH (preferred) or Telnet. The device can be configured to use either SSH version 1 or 2.
- To use default settings (recommended in most cases), leave the Port number and both Override options clear.
-
If TOS is configured to automatically replace the SSH host key when a new SSH host key is detected for a device, you can Override SSH host key settings to prevent the host key from being replaced for this device.
You can then set TOS to Replace SSH host key automatically for this specific device.
Warning: Automatic replacement of the SSH host key can expose your server to security risks and is not recommended.
- Override SSH Version: Select this option to force the device to use SSH-1 or SSH-2
- Override Cipher: Select this option to force the device to use DES or 3DES encryption
Click Next.
-
-
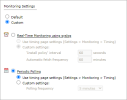
In Monitoring Settings, do one of the following:
- To use real-time monitoring and timing settings from the Timing page, select Default.
Otherwise, select Custom and configure the monitoring mode and settings.
Real-Time Monitoring: Applies only if syslogs Sending Additional Information Using Syslog) are configured. Select Custom settings and configure:
- 'Install policy' interval: When two or more Install Policy events for the same policy occur within this time interval, TOS combines the events into a single Install Policy revision (Default: 60 seconds)
- Automatic fetch frequency: Frequency (in minutes) for automatic fetch
-
Periodic Polling, select Custom settings and configure the Polling frequency: How often TOS fetches the configuration from each device.
If you select 1 day, you can then select the exact time (hour and minute) for the daily polling.
Click Next.
- Save the configuration.
The Cisco device now appears in the Monitored Devices tree.
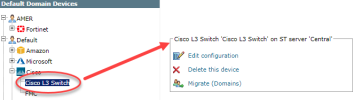
Configure a Monitored Device
After you add a device, further configuration options are available.
Options vary depending on your environment.
Example
-
Edit configuration: Use the wizard to modify selected device settings. See Add a Device in this topic.
-
Delete this device: Type yes to confirm that you want to delete the device.
-
Migrate (ST servers): Available in distributed deployments. Select the server where the device will be monitored and click Migrate.
-
Migrate (Domains): Available in multi-domain deployments. Select the domain where the device will be monitored and click Migrate.
How Do I Get Here?
SecureTrack > Monitoring ![]() > Manage Devices
> Manage Devices
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague