On this page
Monitoring Check Point Smart-1 Cloud Devices
Overview
TOS monitors the Check Point Smart-1 Cloud devices dashboard for policy revision changes.
To see which TOS features are supported for your device, review the SecureTrack Features by Vendor.
Prerequisites
To complete the Check Point Smart-1 Cloud configuration procedures, you must have the following connection information from the Check Point Dashboard:
|
ID Information |
Description |
|---|---|
|
API Key |
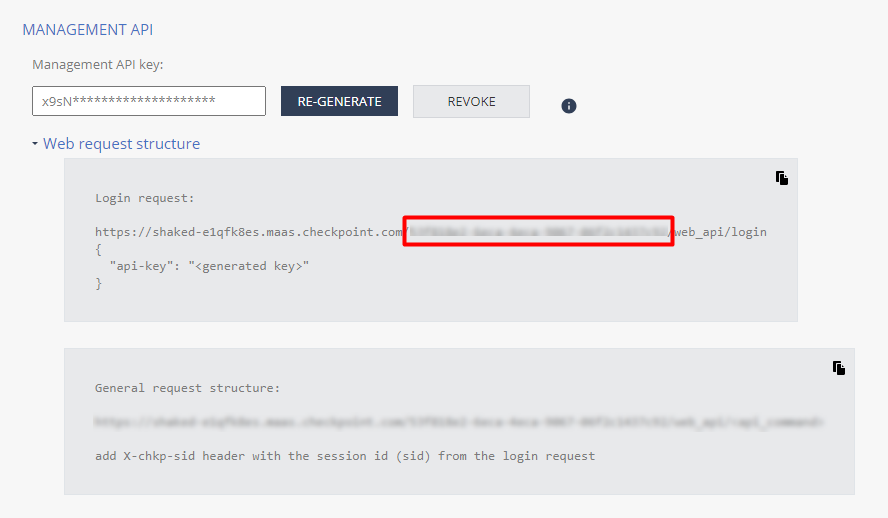
An API Key is the unique ID provided by Check Point so that the device can communicate with TOS. When you log into the Check Point site:
|
|
Context |
Copy this value from the URL in the Web request structure box. |
|
Service Identifier |
Copy this value from Welcome page > Service Management > Service information > Service identifier. |
|
Log ID |
Contact Check Point support for a Log ID. If you manage more than one tenant, you must obtain a unique Log ID for each tenant. |
Add a device
-
Select Check Point > Smart-1 Cloud.
-
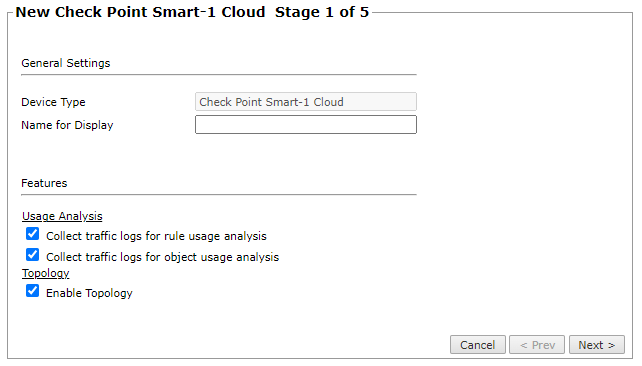
Configure the device settings:
Depending on the Check Point server type, some or all of the following options will appear:
-
Device Type: Check Point Smart-1 Cloud (filled automatically)
-
Name for Display
-
Usage Analysis: Select the relevant options:
-
Collect traffic logs for rule usage analysis: Necessary for Rule Usage reports.
-
Collect traffic logs for object usage analysis: Necessary for reporting on unused objects and services in Rule Usage Reports.
Object usage analysis requires plenty of free disk space (depending on the number of gateways and the amount of traffic logs generated). If disk space is limited, you can configure SecureTrack to limit the number of days that data is kept.
We recommend that you enable SecureTrack administrative alerts, which notify you if there is low disk space on the server. When disk utilization exceeds 90% in the partition that has the database, SecureTrack sends an alert.
-
-
Enable Topology: Collects routing information for building the network Map.
Topology options for Advanced management mode are configured when you import managed devices.
-
-
Click Next.
-
Configure the TOS connection to the Check Point Smart-1 device with the API key that you saved (see Prerequisites):
-
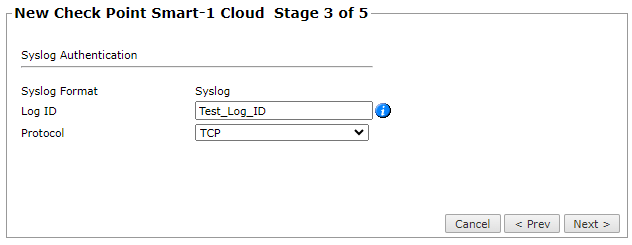
Configure the Syslog authentication:
Note: This step is mandatory. To prevent unexpected behavior, you must include a valid Log ID.-
Log ID: Provide the Log ID that you acquired (see Prerequisites).
-
Protocol: Select TCP or UDP. For more information, see Configuring Check Point Syslogs Over Encrypted TCP.
-
-
Click Next.
-
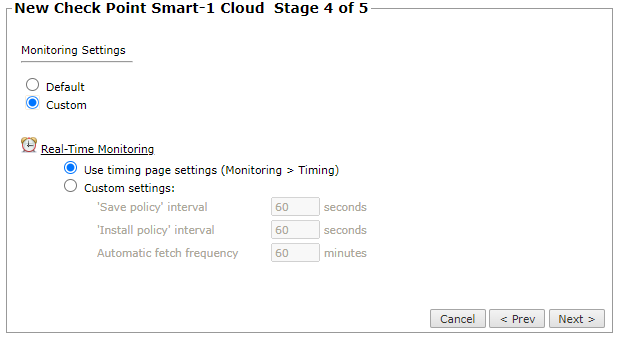
In the monitoring settings, do one of the following:
-
To define specific timing settings for this device, select Custom, then select Custom settings, and configure:
-
'Save policy' interval: When a Save Policy event is followed within this time interval by an Install Policy event for the same policy, SecureTrack tries to combine the two events into a single revision. The default value is 60 seconds.
-
'Install policy' interval: When two or more Install Policy events for the same policy occur within this time interval, SecureTrack combines the events into a single Install Policy revision (Default: 60 seconds).
-
Automatic fetch frequency: See Monitoring Devices in TOS.
-
-
-
Click Next.
-
Click Save.
The Check Point device appears in the Monitored Devices list.
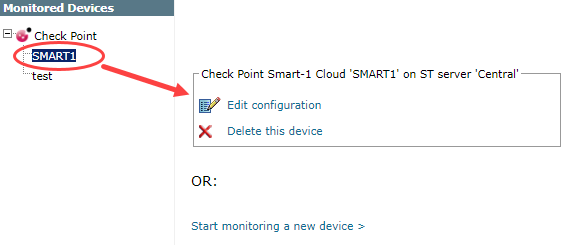
Configure a monitored device
After you add a device, further configuration options are available.
Options vary depending on your environment.
-
Edit configuration: Use the wizard to modify selected device settings. See Add a Device in this topic.
-
Delete this device: Type yes to confirm that you want to delete the device.
How do I get here?
SecureTrack > Monitoring ![]() > Manage Devices
> Manage Devices
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague