On this page
Configuring Third Party Risk Analysis
|
|
This topic is intended for SecureChange workflow owners, who are responsible for creating and maintaining workflows. |
Overview
To use a third party tool to determine the risk in a Access Request, you need to link to a script which takes input data from SecureChange and returns an XML file with details of the risk level. The script acts as a mediator between SecureChange and the external risk assessment tool.
The process works as follows:
- User opens an Access Request ticket and enters the source and destination details. Source and destination can be an IP address, subnet, SecureTrack object, or group.
- Once the external risk analysis tool is called, an automated script is triggered with the Access Request details (taken from the Input Data XML file). The script reformats the data in a format that can be processed as a risk assessment query in the external tool.
- The external third party risk assessment tool analyzes the input data, calculates the risk, and generates risk assessment result to be collected by the script, which reformats the Return Data in XML format, and sends it back to SecureChange. The response must include a risk status for every access request in the ticket.
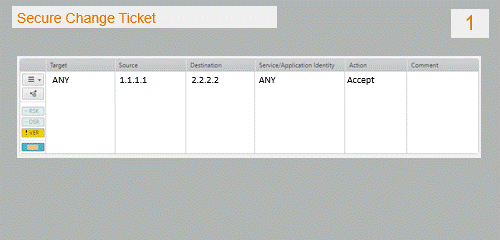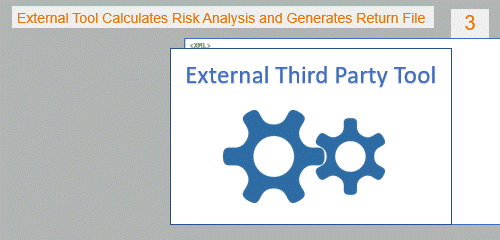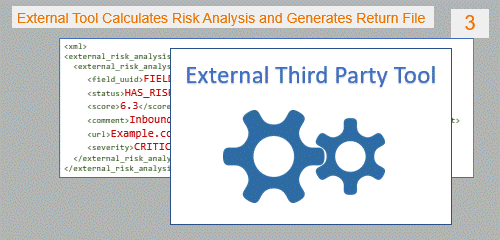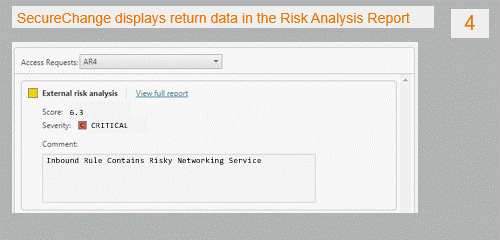
- SecureChange displays the return data in the Access Request Risk Analysis report.
Tufin provides two extensions
-
Vulnerability-based Change Automation App helps your team identify and mitigate network exposure to vulnerabilities. By integrating with one or more vulnerability scanners, the extension generates a list of firewall rules that could allow malicious actors to access your sensitive network assets using identified vulnerabilities. The extension also ranks these vulnerabilities and exposed assets by criticality to help you prioritize mitigation efforts. For more information, see Vulnerability-based Change Automation App.
-
Vulnerability Mitigation App tests proposed firewall rules against your vulnerability dataset by integrating SecureChange with third-party Vulnerability Management tools. For more information, see Vulnerability Mitigation App.
Input data
When the External Risk Analysis tool is called from within the ticket, it triggers a script which takes data from an XML file and reformats the data in a format that can be processed as a risk assessment query in the external tool. The script must be stored in the following directory.
/opt/tufin/data/securechange/scripts
The script takes data from an XML file in the following format, the source and destination could be an IP address, subnet, SecureTrack object, or group.
<?xml version="1.0" encoding="UTF-8"?>
<field_info>
<context xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="ticket_draft" />
<field xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="multi_access_request">
<name>ar</name>
<access_request>
<uuid>FIELD_UUID0</uuid>
<order>AR1</order>
<use_topology>true</use_topology>
<targets>
<target type="ANY" />
</targets>
<users>
<user>Any</user>
</users>
<sources>
<source type="IP">
<ip_address>1.1.1.1</ip_address>
<netmask>255.255.255.255</netmask>
<cidr>32</cidr>
</source>
</sources>
<destinations>
<destination type="IP">
<ip_address>2.2.2.2</ip_address>
<netmask>255.255.255.255</netmask>
<cidr>32</cidr>
</destination>
</destinations>
<services>
<service type="ANY" />
</services>
<action>Accept</action>
<labels />
</access_request>
<access_request>
<uuid>FIELD_UUID02</uuid>
<order>AR2</order>
<use_topology>true</use_topology>
<targets>
<target type="ANY" />
</targets>
<users>
<user>Any</user>
</users>
<sources>
<source type="IP">
<ip_address>3.3.3.3</ip_address>
<netmask>255.255.255.255</netmask>
<cidr>32</cidr>
</source>
</sources>
<destinations>
<destination type="IP">
<ip_address>2.2.2.2</ip_address>
<netmask>255.255.255.255</netmask>
<cidr>32</cidr>
</destination>
</destinations>
<services>
<service type="ANY" />
</services>
<action>Accept</action>
<labels />
</access_request>
<designer_verifier_advanced_option>NONE</designer_verifier_advanced_option>
</field>
</field_info>Return data
The script returns the analysis as an XML file which contains the following data:
- field_uuid – unique identifier for each access request in the ticket, received from the request.
- status – risk status with one of the following values: NO_RISK, HAS_RISK, CANNOT_COMPUTE
- score – a floating point number denoting the risk score as provided by the external tool.
- comment – text comment, which could be used to provide explanations or reason for the risk
- detailed_report_url– optional link to a risk assessment report stored on an external repository managed by a third party system.
- severity – risk severity with one of the following values: CRITICAL, HIGH, MEDIUM, LOW
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<external_risk_analysis_result>
<external_risk_analysis_result_for_fields>
<external_risk_analysis_result_for_field>
<field_uuid>FIELD_UUID0</field_uuid>
<status>HAS_RISK</status>
<score>6.3</score>
<comment>Inbound Rule Contains Risky Networking Service</comment>
<detailed_report_url>Example.com/riskAnalysis/FIELD_UUID0</detailed_report_url>
<severity>CRITICAL</severity>
</external_risk_analysis_result_for_field>
<external_risk_analysis_result_for_field>
<field_uuid>FIELD_UUID1</field_uuid>
<status>NO_RISK</status>
<score>1</score>
<comment>No Risk in Access Request</comment>
<detailed_report_url>Example.com/riskAnalysis/FIELD_UUID1</detailed_report_url>
<severity>LOW</severity>
</external_risk_analysis_result_for_field>
</external_risk_analysis_result_for_fields>
</external_risk_analysis_result>Technical notes
- On a saved ticket, the input information the script gets will contain the ticket ID, step ID, and task ID. When the ticket is still in draft mode (on first step, before it is submitted), the input information that the script gets includes only the traffic information from the Access Request.
- On a saved draft, the request must contain only the Access Request.
- The response must contain results for each Access Request. If the response does not contain the same number of Access Requests as the ticket, it will result in an error.
Configuring a custom script for third party analysis
-
In the Workflow Properties window, select Enable external risk analysis and enter the full path to the script. The script must be in the format described above and be placed in the following directory:
/opt/tufin/data/securechange/scripts
-
Click Test to confirm that SecureChange can access the script with the correct permissions and that the script returns a properly formed XML response. Test calls the script with
testas the first and only argument. The script must finish successfully (returned code=0). -
Enter a title for the report that will be used as the default title for the risk enhancement report for each access request.
- Click OK to save your changes.
How do I get here?
SecureChange > ![]() Workflows
Workflows
Was this helpful?
Thank you!
We’d love your feedback
We really appreciate your feedback
Send this page to a colleague