On This Page
Vulnerability Mitigation App provides you with a comprehensive view of the vulnerability status of your network, from a holistic view your entire network in the Home menu to a detailed breakdown of critical zones, exploitable rules and exposed assets.
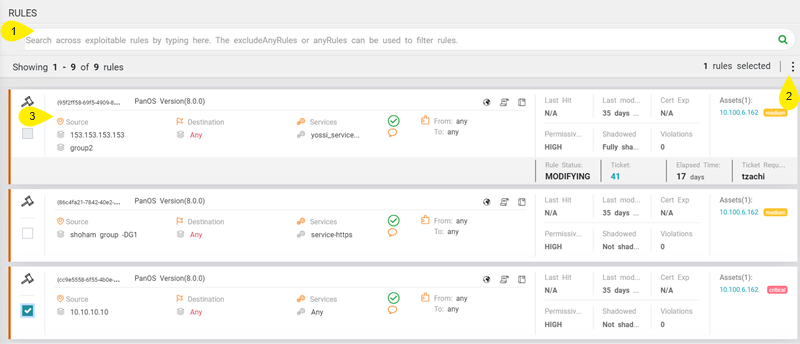
The detailed rule breakdown is displayed in the Rules (![]() ) menu, which provides you with much needed information on the vulnerability details of the individual rules.
) menu, which provides you with much needed information on the vulnerability details of the individual rules.
With this information, you can prioritize assets and rules for mitigation. Assets can be mitigated by opening from Vulnerability Mitigation App a Server Decommission request ticket in SecureChange. Rules can be mitigated by opening a Rule Decommission request from the SecureTrack Policy Browser.
The app correlates rules by the vulnerabilities’ services. Only rules that match the source or destination AND one of the services are considered vulnerable and correlated to the app.
The Rules menu offers the following features:
- Search field for filtering the rules table according to the details of specific rules. You can perform searches using free text, or one of the following predefined strings:
- anyRules: Display rules with ANY object assigned to a firewall that is not the asset's firewall
- excludeAnyRules: Exclude rules containing ANY object that is assigned to a firewall that is not the asset's firewall.
- An actions (
 ) menu with the following options:
) menu with the following options:- Change rule by Rule Modification: Select a rule to change and select this option. VMA opens a Rule Modification workflow in SecureChange. The status of the rule changes to Modifying. After the rule is changed, VMA checks the rule to see if it is still vulnerable. If not, VMA removes it from the list.
- Download as CSV: Download the rules table as a CSV file.
- Rules table listing all the rules containing services that can be used to exploit the vulnerable asset. The table includes the following information:
- Rule UID
- Rule name
- Source
- Destination
- Affected services
- Rule action
- Comments
- Zones
- Domain
- Logs
- Rule metadata including Last hit, Last modified, Expiration date, Permissiveness level, Shadowed, and Violations count
- Assets exposed by rules, sorted by severity
