On This Page
Policies and Rules
Overview
A policy is a component of your Cloud Security Policy and is made up of rules defining the access or communication channels that should and/or should not be allowed to and from your assets. A policy can contain any number of rules and a rule can contain any number of access definitions.
What Can I See Here?
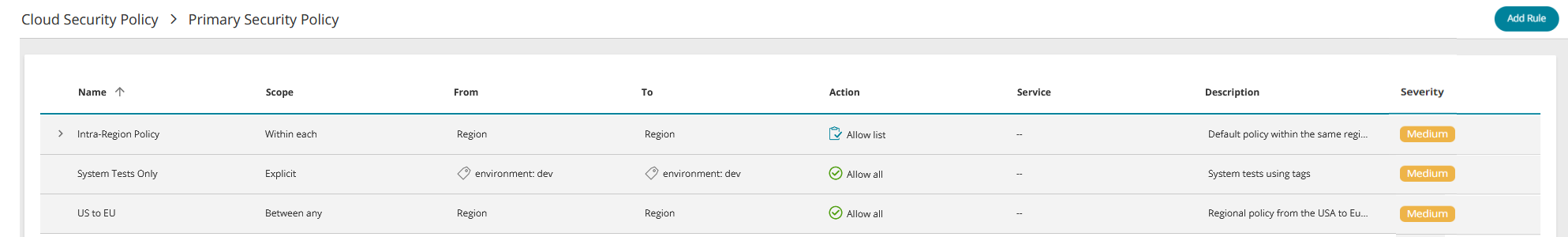
When you create a policy, it initially has no rules. All the rules that have been added to the policy appear with their name and details.
Rule Details (for a detailed explanation of the fields, see Cloud Security Policy Structure):
-
Name: Rule name
-
Scope: Relationship between the 'From' and 'To' entities
-
From: Logical collection of assets defining the network traffic source
-
To: Logical collection of assets defining the network traffic destination
-
Action: Action that should be taken - allow or block
-
Service: Protocol(s) of the traffic
-
Description: Rule description
-
Severity: Impact of a rule violation.
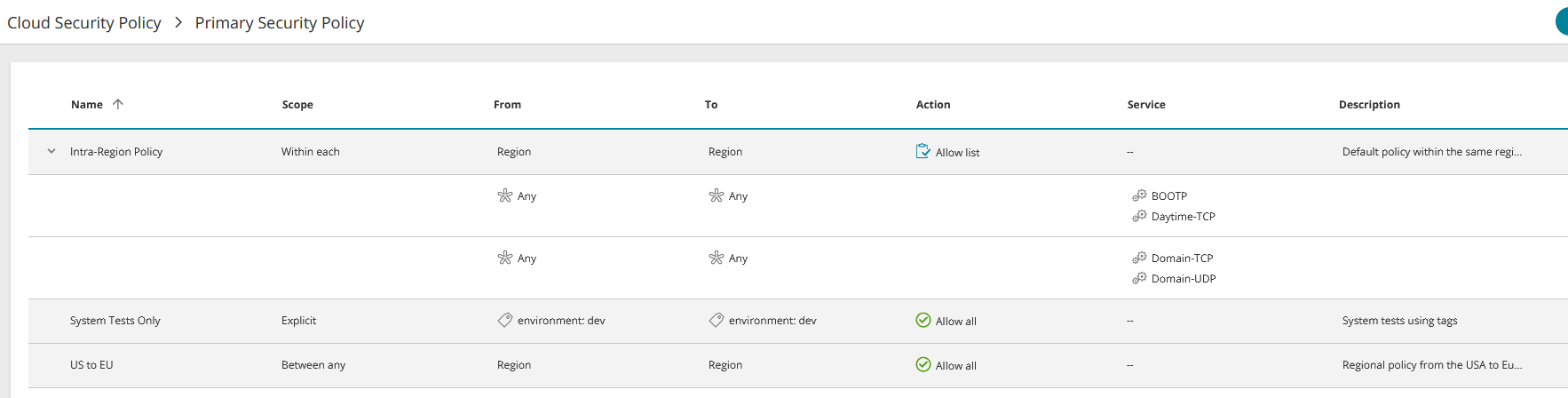
For rules with an action of Allow list or Block list, click on > to expand the display to include the rule's access definitions.
What Can I Do Here?
- Add a policy rule
- Edit a policy rule
- Delete a policy rule
- Add a Policy Rule Access
- Edit a Policy Rule Access
- Delete a Policy Rule Access
Add a Policy Rule
-
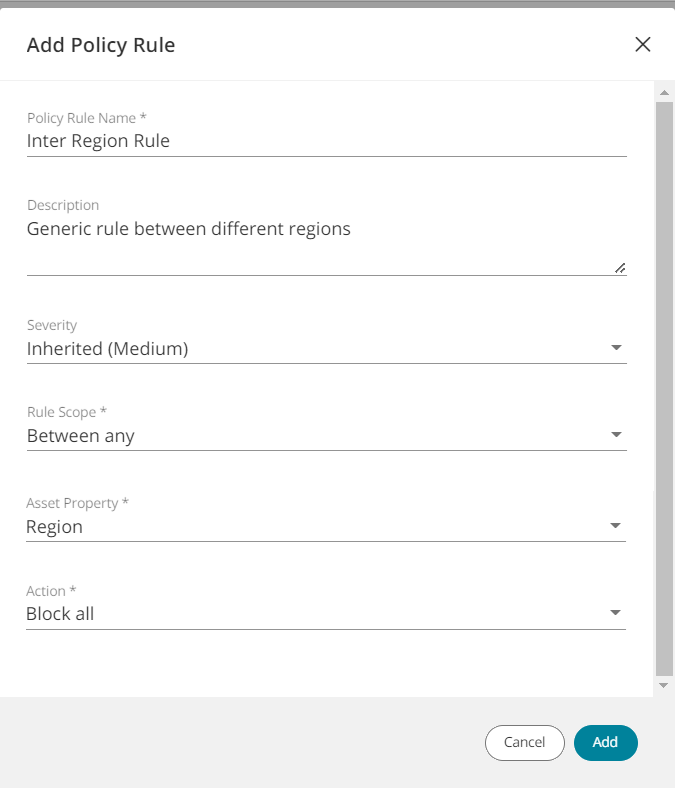
Click Add Rule. The Add Policy Rule window appears.
-
Enter the rule details. For a detailed explanation of the fields, see Cloud Security Policy Structure):
-
Policy rule name: Enter the desired text.
-
Description: Enter the desired text.
-
Severity: Assign a severity for the rule. By default, the rule severity is inherited from the cloud policy.
-
Rule scope: Select one:
-
Explicit
-
Within each
-
Between any
-
-
Asset property (only if rule scope is 'Within each' or 'Between any'): Select one:
-
Account
-
Virtual Network
-
Subnet
-
Region
-
Tags
-
-
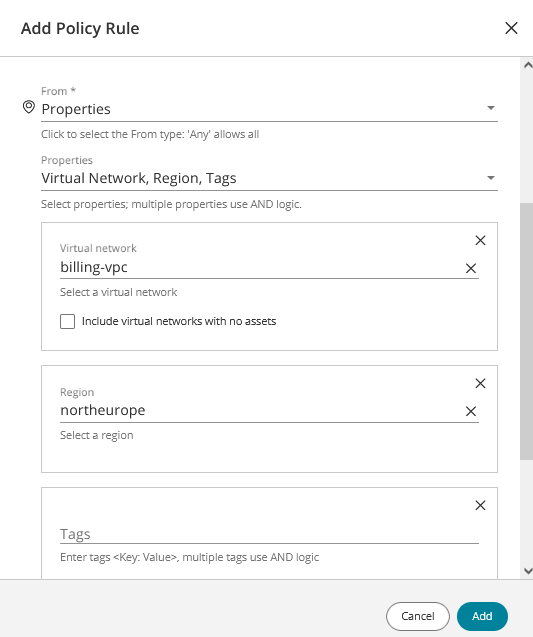
From/To (only if rule scope is Explicit): For each of the From and To fields, select one:
-
Any: Any location.
-
Internet (available only for From): Any internet location outside of your monitored vendor accounts.
-
IPs: If selected, you will be prompted to enter one or more IP addresses or CIDR blocks to represent the location.
-
Properties: If selected, you will be prompted to select one or more asset properties that together define the location.
-
Account: If selected, you are prompted to select a single account.
-
Virtual Network: If selected, you are prompted to select a single virtual network from the list. To include networks that currently contain no assets, check the checkbox.
-
Subnet: If selected, you are prompted to select a single subnet from the list. To include subnets that currently contain no assets, select the checkbox.
-
Region: If selected, you are prompted to select a single region from the list.
-
Tags: If selected, you are prompted to enter one or more tag key values or select from the list.
-
-
-
Action: Select one:
-
Allow all: All traffic defined above should be allowed. No additional conditions are required.
-
Block all: All traffic defined above should not be allowed. No additional conditions are required.
-
Customized allow list: You will specify one or more access definitions that should be allowed.
-
Customized block list: You will specify one or more access definitions that should be blocked.
-
-
Access (only if action customized allow/block list selected).
If you selected action Customized allow / block list, you must define at least one access definition.
An access definition consists of 'From', 'To' and 'Service'.
-
From/To: For each of the From and To fields, select one:
-
Any: Any location.
-
Internet (available only for From): Any internet location outside of your monitored vendor accounts.
-
IPs: You will be prompted to enter one or more IP addresses or CIDR blocks to represent the location.
-
Properties: You will be prompted to select one or more asset properties that together define the location.
-
Account: If selected, you are prompted to select a single account.
-
Virtual Network: If selected, you are prompted to select a single virtual network from the list. To include networks that currently contain no assets, check the checkbox.
-
Subnet: If selected, you are prompted to select a single subnet from the list. To include subnets that currently contain no assets, select the checkbox.
-
Region: If selected, you are prompted to select a single region from the list.
-
Tags: If selected, you are prompted to enter one or more tag key values or select from the list.
-
-
-
Service: You will be prompted to enter one or more services. Select from the list or enter a service in one of the formats:
-
IP:<INT>
-
TCP:<FROM>-<TO>
-
UDP:<FROM>-<TO>
-
Additional access definitions can be added if required. To add an access definition, select Add Access.
-
-
- Save the rule.
Edit a Policy Rule
- Hover over the rule and select
 > Edit policy rule. The edit rule window appears.
> Edit policy rule. The edit rule window appears. - Click Edit Rule from the pop-up menu.
- The Edit Rule Window appears. See Add a Policy Rule for more information.
- Make changes as necessary and click Save.
Delete a Policy Rule
- Hover over the rule and select
 > Remove policy rule.
> Remove policy rule. - Click Delete policy rule from the pop-up menu. A warning appears.
- Confirm the action. The rule will be deleted.
Add a Policy Rule Access
Enabled only for rules with action customized allow or block list.
-
Hover over the rule and select
 > Add policy rule access. The Add Policy Rule Access window appears.
> Add policy rule access. The Add Policy Rule Access window appears. -
Complete the access definition.
An access definition consists of 'From', 'To' and 'Service'.
-
From/To: For each of the From and To fields, select one:
-
Any: Any location.
-
Internet (available only for From): Any internet location outside of your monitored vendor accounts.
-
IPs: You will be prompted to enter one or more IP addresses or CIDR blocks to represent the location.
-
Properties: You will be prompted to select one or more asset properties that together define the location.
-
Account: If selected, you are prompted to select a single account.
-
Virtual Network: If selected, you are prompted to select a single virtual network from the list. To include networks that currently contain no assets, check the checkbox.
-
Subnet: If selected, you are prompted to select a single subnet from the list. To include subnets that currently contain no assets, select the checkbox.
-
Region: If selected, you are prompted to select a single region from the list.
-
Tags: If selected, you are prompted to enter one or more tag key values or select from the list.
-
-
-
Service: You will be prompted to enter one or more services. Select from the list or enter a service in one of the formats:
-
IP:<INT>
-
TCP:<FROM>-<TO>
-
UDP:<FROM>-<TO>
-
-
-
The Edit Rule Window will be displayed. See Add a Policy Rule for more information.
-
Make changes as necessary and click Save.
Edit a Policy Rule Access
Enabled only for rules with action customized allow or block list.
-
Click on the expand icon (>) of the desired rule. The access definitions appear below the rule.
-
Hover over the desired access and select
 > Edit policy rule access. The Edit Policy Rule Access window appears.
> Edit policy rule access. The Edit Policy Rule Access window appears. -
Make changes as necessary and click Save.
Delete a Policy Rule Access
Enabled only for rules with action customized allow or block list that have more than one access defined.
-
Click on > of the desired rule. The access definitions appear below the rule.
-
Hover over the desired access and select
 > Delete policy rule access.
> Delete policy rule access. -
Confirm deletion.
How Do I Get Here?
Main Menu > Cloud Security Policy
Then select the desired policy from the list.
Or, click on the name of the policy from anywhere else in SecureCloud.