On This Page
Risky Ports by Asset
Overview
The risky ports assets page lists all assets that have one or more high-risk ports exposed to the internet.
What Are Risky Ports?
In SecureCloud, risky ports are commonly-used ports exposed to the internet. They are therefore considered high risk and could leave your assets open to attack. The list of risky ports can be managed in Configuration and the scope of reporting them further refined in Exceptions.
A default list is included when you install SecureCloud, which you can modify to your requirements:
- Port 23 - Telnet: Data is plain text and so open to injection
- Port 110 - POP3: Plain text
- Port 137-9 NetBIOS meant for file and printer sharing - can be used to obtain system information such as domain, workgroup and system names
- Port 445 SMB over IP - can be used to obtain system information
- Port 3389 - RDP - could be breached by brute-force methods for trying username and password combinations
What Can I See Here?
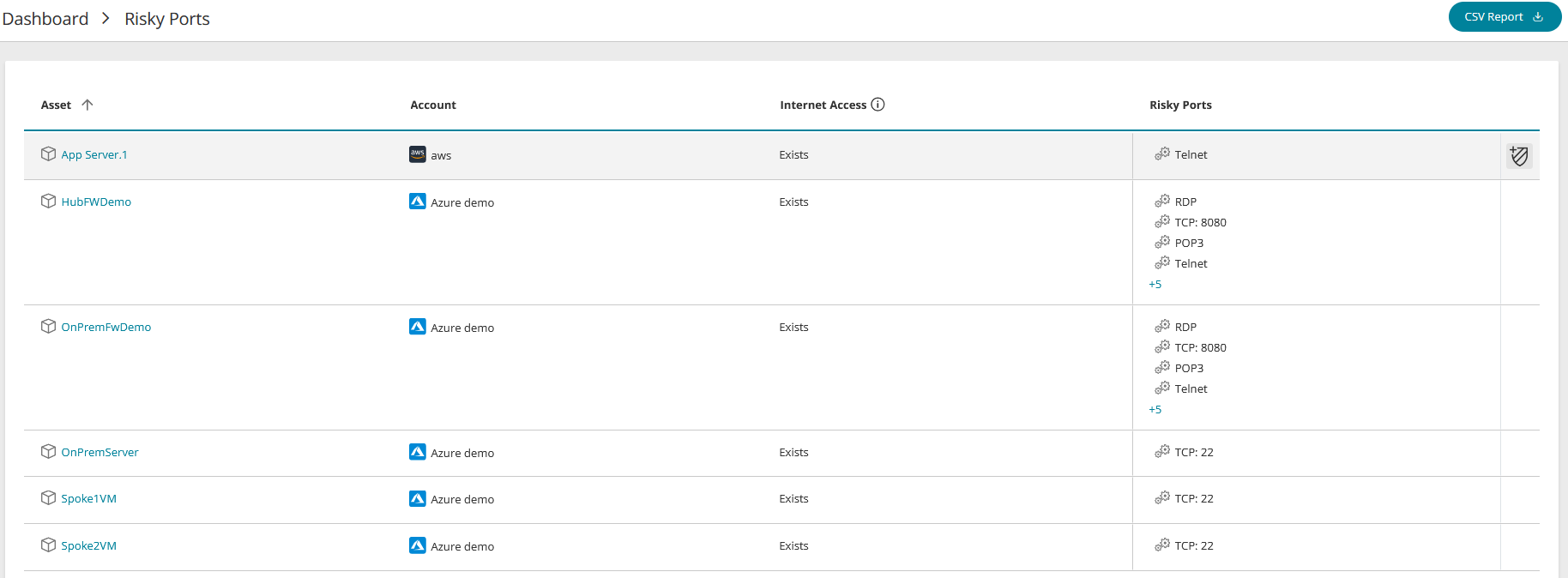
The main screen section is a list of the assets showing the following information:
-
Asset: The asset's name
-
Account: The name of the cloud account with the vendor's icon - Amazon AWS, Microsoft Azure, Google Cloud
-
Internet access:
Exists: The asset has access to the internet
None: The asset doesn't have access to the internet
-
Risky Ports. A list of all risky ports identified in the asset
What Can I Do Here?
- Add an exception
-
Download to CSV file - click on CSV Report
Add an Exception
In SecureCloud, an exception is a user-defined condition that causes SecureCloud to ignore certain policy violations. The existence of an exception can change the statistical data displayed on the Dashboard and also suppress warnings from appearing elsewhere in the product, such as screen elements appearing in red and warning icons on assets. In other cases, properties that would have constituted a violation are displayed in a strike-through font to indicate they are currently not considered violations of policy. The change in behavior caused by the exception is canceled if the exception is deleted. A single exception can define only a simple set of criteria. However, you can create as many exceptions as you like.
A risky port exception defines a more specific case of a definition made in risk configuration to be excluded from being considered a violation.
To add an exception:
-
Hover over the desired asset and click on
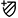 Add exception. The Add Exception window appears.
Add exception. The Add Exception window appears. -
Complete the exception details.
Exception Name: A name of your choice.
Violation Type: Risky port. This cannot be changed.
Violation Details: All ports identified as violations are shown and selected by default. If there is more than one port, you can unselect any ports you don't want to include in the exception. If only one port is shown, it cannot be unselected. Press Escape to continue.
Asset Scope: The assets to be included in the exception. Select one:
- Asset tags - all assets having the exact same tags as this asset
- Cloud account - all assets in the cloud account in which this asset is located
- All cloud accounts - all cloud accounts monitored by SecureCloud
You can click on View all assets in scope to view all assets that will be affected by this exception
Description: Optional text of your choice.
- click Add to save.
Once added, exceptions can be viewed in Exceptions, where they can be deleted if desired.
How Do I Get Here?
Main Menu > Dashboard > Risky Ports widget