On This Page
STRE reports are created in the Create Report tab from a list of predefined templates. These reports can be ad-hoc single-use reports, frequently used reports, or recurring reports that automatically run on a schedule that you define when creating the report.
How to create a report
-
Click on the report template that you want to use.
The Setup page for the report is displayed.
-
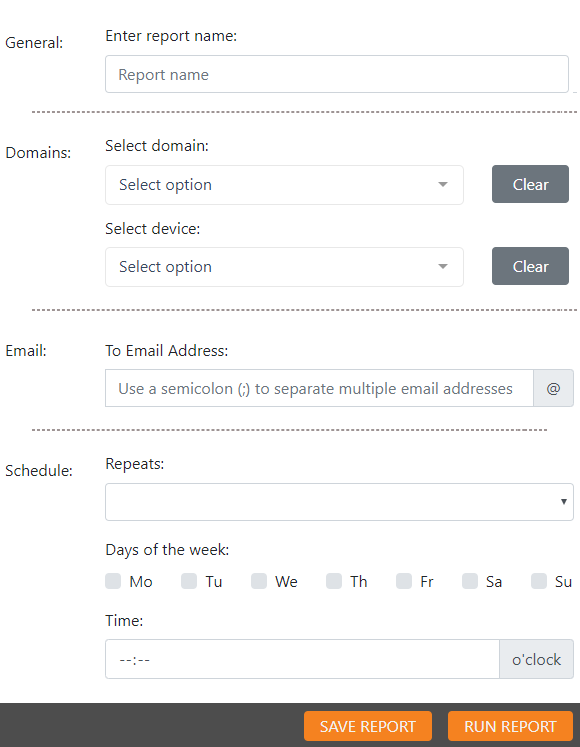
Configure the report settings, which are used to define the report domain devices, recipients, and schedule (for recurring reports), as well as additional information required for the report. Some settings are the same for all report templates, while others are specific to an individual template. You can reuse these settings when editing an existing report (Saved Reports tab).
The following settings apply to all report templates:
Setting Category
Fields
General
Report name
Domains
- Select domain
- Select device(s) - For some reports, you can select multiple devices or device groups.
Email
To Email Address: The recipients for notification emails
Use a semicolon (;) to separate multiple email addresses
Schedule
- Repeats
- Days of the week
- Time
The following settings apply to specific report templates:
Report Template
Setting Category
Settings
Business Ownership Changes
- Revisions: Displayed when you select a device
- Dates: Displays when you select more than one device.
Select Revision options (single device selected)
- Start Revision
- End Revision
Select Dates (multiple devices selected)
- Start Date
- End Date
Device Audit
Audit
Select CIS audit paragraphs for inclusion (e.g. CIS 1.3.1 password complexity), all selected by default.
The options are grouped into sub-categories: Settings, password rules, authorization, services, user ID, high availability, dynamic updates, Wildfire and security profiles/
Device credentials must be set up before running this report.
Policy Analysis
Policy Data
Use the search icon to open the object browser.
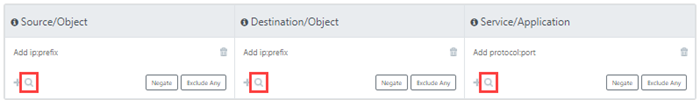
In the object browser, you select Source, Destination, and Service values from devices or zones in any available domain.
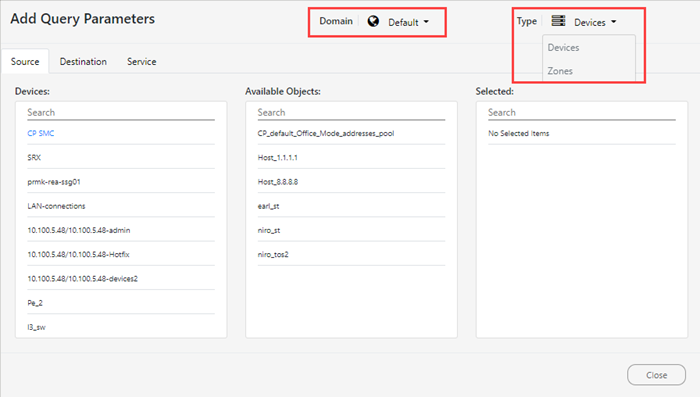
- Source and Destination: Select one or more Devices to view the list of Available Objects to select. To remove a selected object, click it in the Selected list.
- Service: Select one or more predefined applications from the list of Available Applications or enter a protocol and port separated by a colon (for example, tcp:80 or udp:21). To remove a service, click it in the Selected list.
Data options:
- Negate - Click to exclude rules that match the information entered in the query
- Exclude Any - Click to exclude services/objects with "Any"
Filter options:
- Select Shadowing: Select a shadowing option for filtering rules.
- Select Action: Select a rule action for filtering rules: Accept, Drop or Any (both Accept and Drop)
- Simulate NAT: Select to use NAT simulation when calculating the path
- Last Installed Revision: Select to use the last installed policy in the simulation. If there is no installed policy, the last saved policy is used
- Display Blocked Status: Select to display blocked traffic icons next to devices blocking the traffic
- Show Broken Paths: Select to display all nodes even if the node cannot reach the destination, or if the source and destination are the same.
Shadowed rules are rules that match the query, but will never actually handle any of the traffic included in the query as the traffic is handled by a rule or rules higher up in the rulebase.
Since not all rules have a shadowing status in SecureTrack, some rules that match the traffic defined in rules that are higher up in the rulebase may be returned in the report output. Errors will be added to the STRE log file.
Rule and Object Changes
Revisions category displays when you select a device
Select Revision options
- Start Revision
- End Revision
Rule Analytics
Rules
Search - Auto-complete search field for rule values
Security Best Practices
Best Practices
- Best Practices Type
- Names - Best practice use cases
- Values
- Severities
Security Violations
Domains
- Select Matrices
- Custom Filters - options to exclude rules
Shadowed Rules
Domains
Custom Filters - options to exclude rules
Unified Security Compliance
Domains
Select Matrix
-
Click Save Report or Run Report.
