On This Page
Vulnerability Mitigation App provides you with a comprehensive view of the vulnerability status of your network. From a holistic view your entire network in the Home menu to a detailed breakdown of critical zones, exploitable rules and exposed assets.
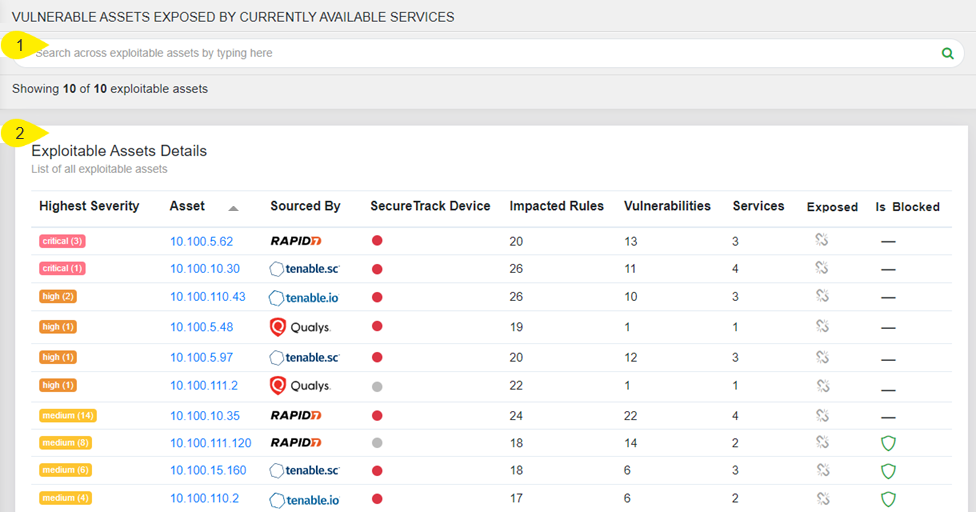
The detailed asset breakdown is displayed in the Assets tab, which provides you with much needed context and visibility regarding the vulnerabilities and affected rules that have been detected.
With this information, you can prioritize which assets should be removed using SecureChange, and which assets should be remediated through patch management.
The Assets menu is divided into two sections:
- Search field for locating specific assets. You can filter the assets in the table by IP address, vulnerability management solution, number of impacted rules, and number of network-based vulnerabilities.
- Exploitable Assets Details table. The assets displayed in this table are sorted by default according to the highest severity of the vulnerabilities correlated by the app. However, you can sort the assets according to any column in the table.
The table includes the following information:
| Column | Description |
|---|---|
| Highest Severity | The severity level of the vulnerabilities |
| Asset |
The asset's IP address. Click the link to view the Asset Profile page for that asset. The Asset Profile page includes the following information on each asset.
|
| Sourced by | The name of the vulnerability management solution, which most recently scanned the asset, or Manual if the asset was added manually. |
| SecureTrack device | This column displays whether the asset is managed by SecureTrack. |
| Impacted Rules | The total number of rules impacted by the asset |
| Vulnerabilities | The total number of network-based vulnerabilities detected |
| Services | The total number of services that can be exploited |
| Exposed |
|
| Is Blocked |
Indicates whether the asset is blocked ( |
