On This Page
Security Controls
Overview
Security controls are objects defined in your cloud vendor accounts that specify the rules of access to and from your assets. SecureCloud locates and displays the security controls in your accounts.
What Can I See Here?
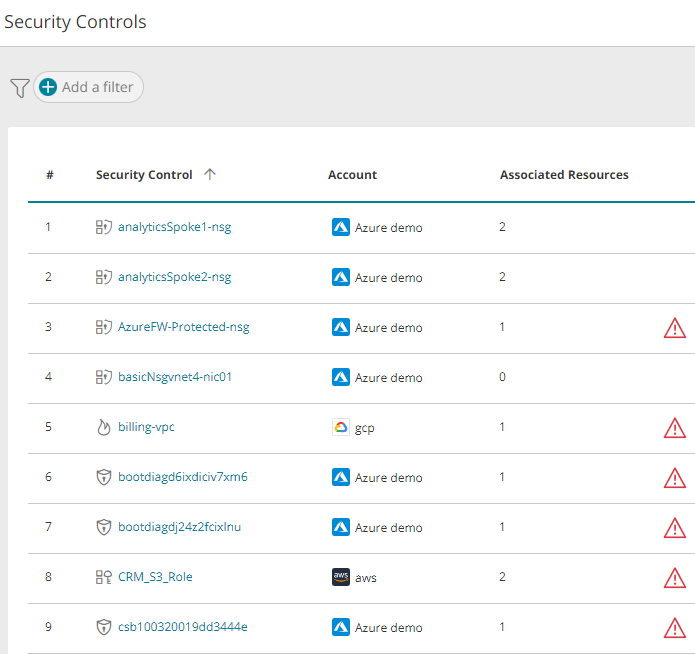
The main screen displays a list of all security controls found. It contains the following details:
-
Type of security control - Icon:
- Name: Name of the security control.
- Account: Cloud vendor icon and the name of the account as defined in SecureCloud.
- Associated Resources: The number of resources associated with the security control.
- Violations icon
 : Appears only if violations exist in at least one of the assets affected by the security control.
: Appears only if violations exist in at least one of the assets affected by the security control.
What Can I Do Here?
- Filter the displayed security controls - click Add a Filter
- View overview for a specific security control - select by clicking on a security control
- View violations for the security control - click on the appropriate warning icon

- View resources associated with a security control - select a security control and then select Associated Resources
- View rules defined in a security control - select a security control and then select Rules
- Suppress rule violations by adding/removing rules or exceptions
Security Control Overview
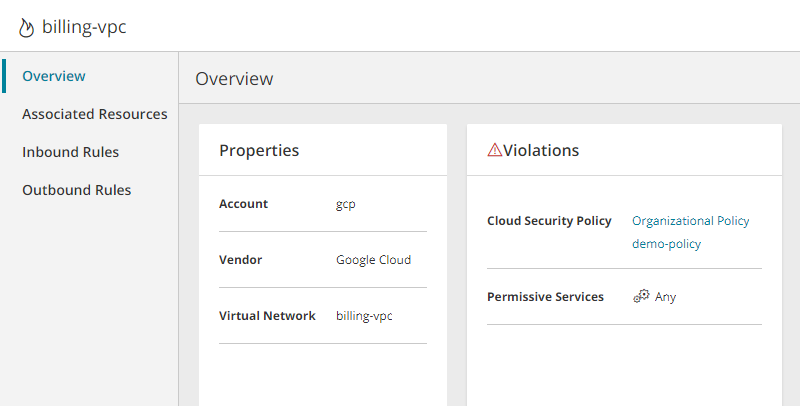
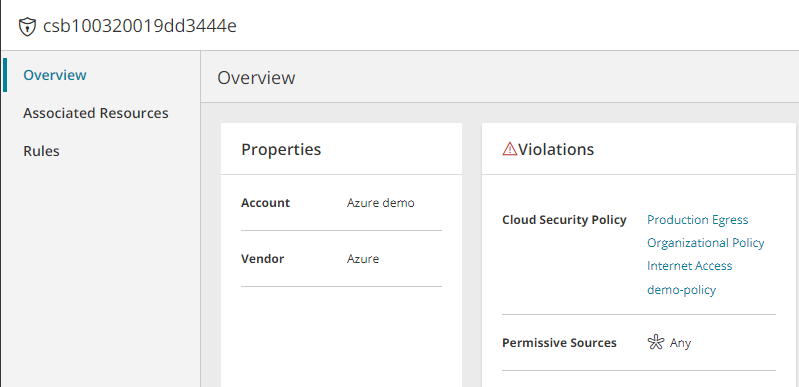
When selecting a security control in the main screen, the overview appears. The information displayed will vary from one type of vendor and security control to another. It may include:
-
Type of security control - Icon
-
 Firewall (AWS firewall, Azure firewall, GCP VPC firewall)
Firewall (AWS firewall, Azure firewall, GCP VPC firewall) -
 Role (AWS role, GCP IAM)
Role (AWS role, GCP IAM) -
 Security group (AWS security group, Azure NSG)
Security group (AWS security group, Azure NSG) -
 Storage security
Storage security -
 Database security
Database security
-
- Name defined in your cloud vendor account
- Account - the name of the cloud vendor account as defined in SecureCloud
- Vendor - the cloud service provider
- Additional properties, according to type of security control and cloud vendor
- Tags
- Details of Violations
The information shown will vary from one type of security control to another and from one cloud vendor to another.
Examples
When hovering over a property, the copy to clipboard icon ![]() appears - click to copy the value.
appears - click to copy the value.
Select Associated Resources in the menu to display all resources affected by the security control.
Select the relevant rule tabs in the menu to display the security control's rules.
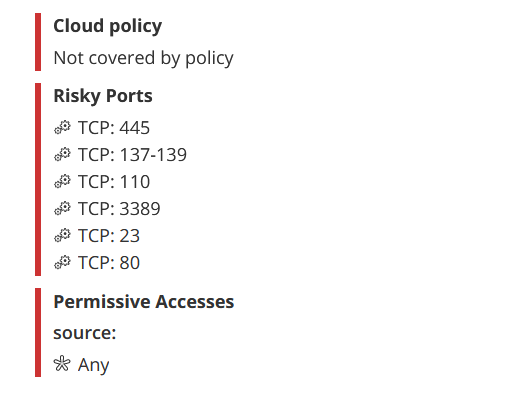
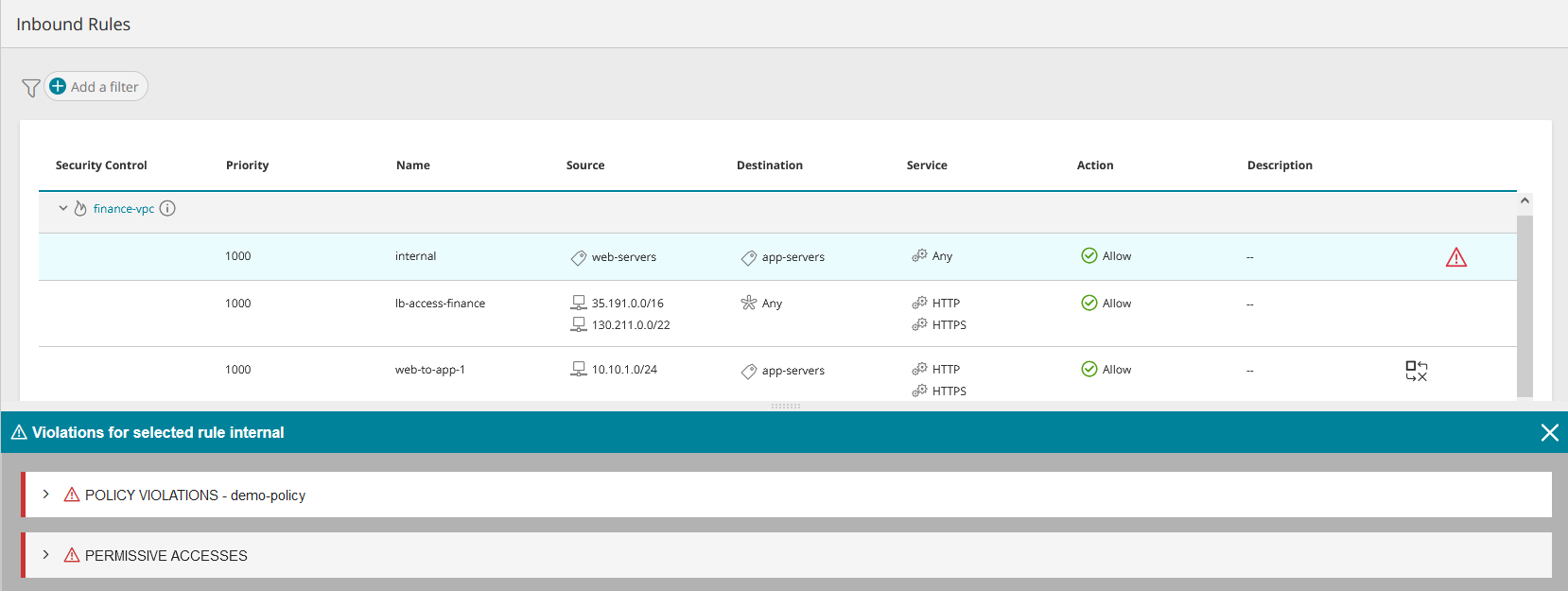
Violations
The violations window appears when clicking on a Warning icon ![]() on the main screen or on a rule and is also a fixed part of the Overview. If there are no violations, an appropriate message is shown.
on the main screen or on a rule and is also a fixed part of the Overview. If there are no violations, an appropriate message is shown.
Violations are not a characteristic of the security control itself. The violations shown for a security control are all those found for its associated assets.
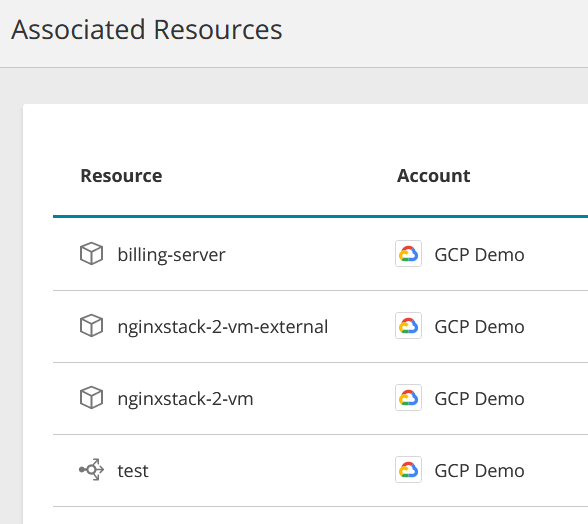
Associated Resources
Display all the resources affected by the security control.
What Can I See Here?
-
Resource type icon
-
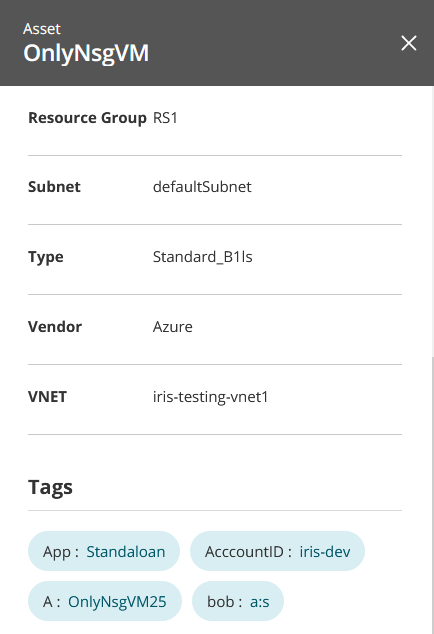
 VM asset
VM asset
-
 Storage asset
Storage asset
-
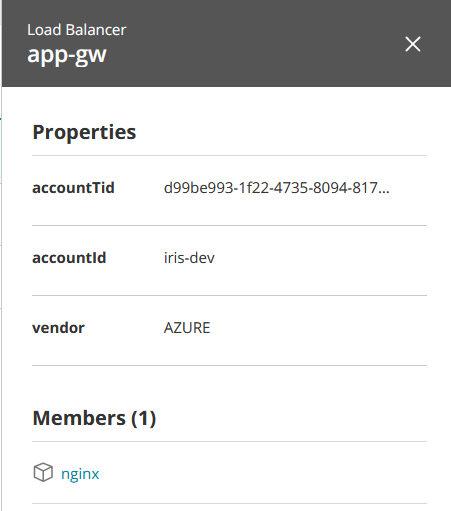
 Load balancer
Load balancer -
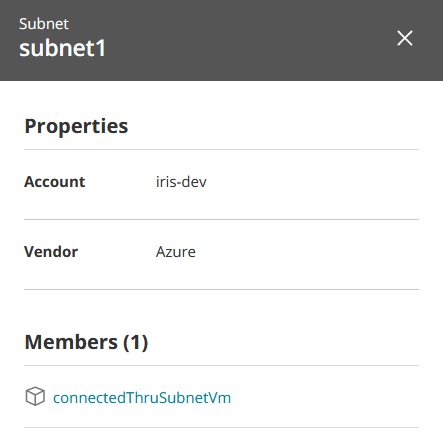
 Subnet
Subnet -
 Cluster
Cluster
-
-
Resource name
- Account - cloud vendor icon and the name of the account as defined in SecureCloud
Select a resource to see more details. Examples:
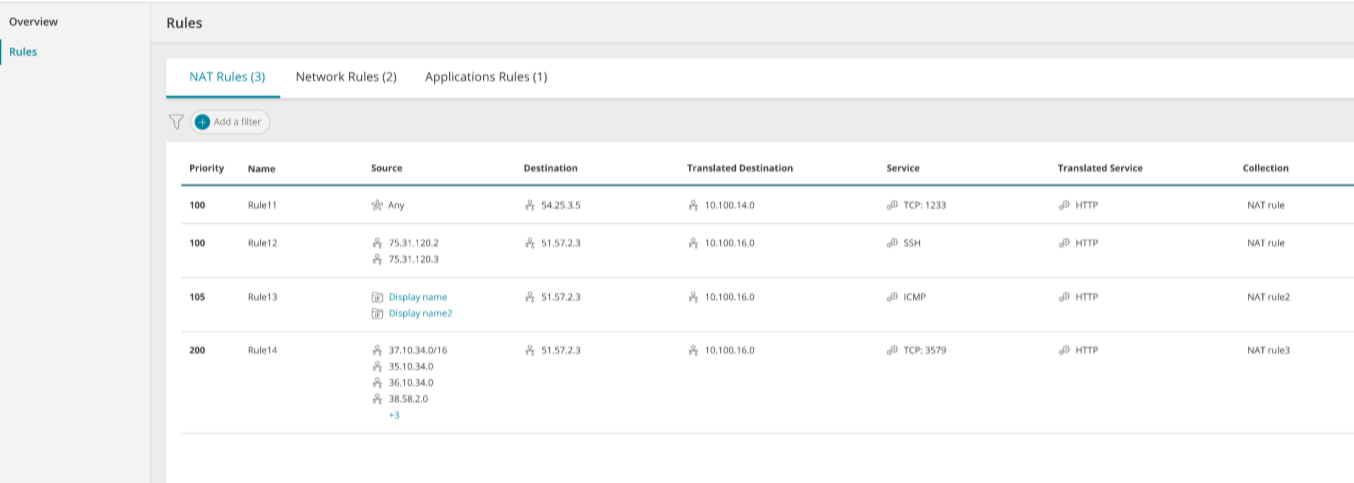
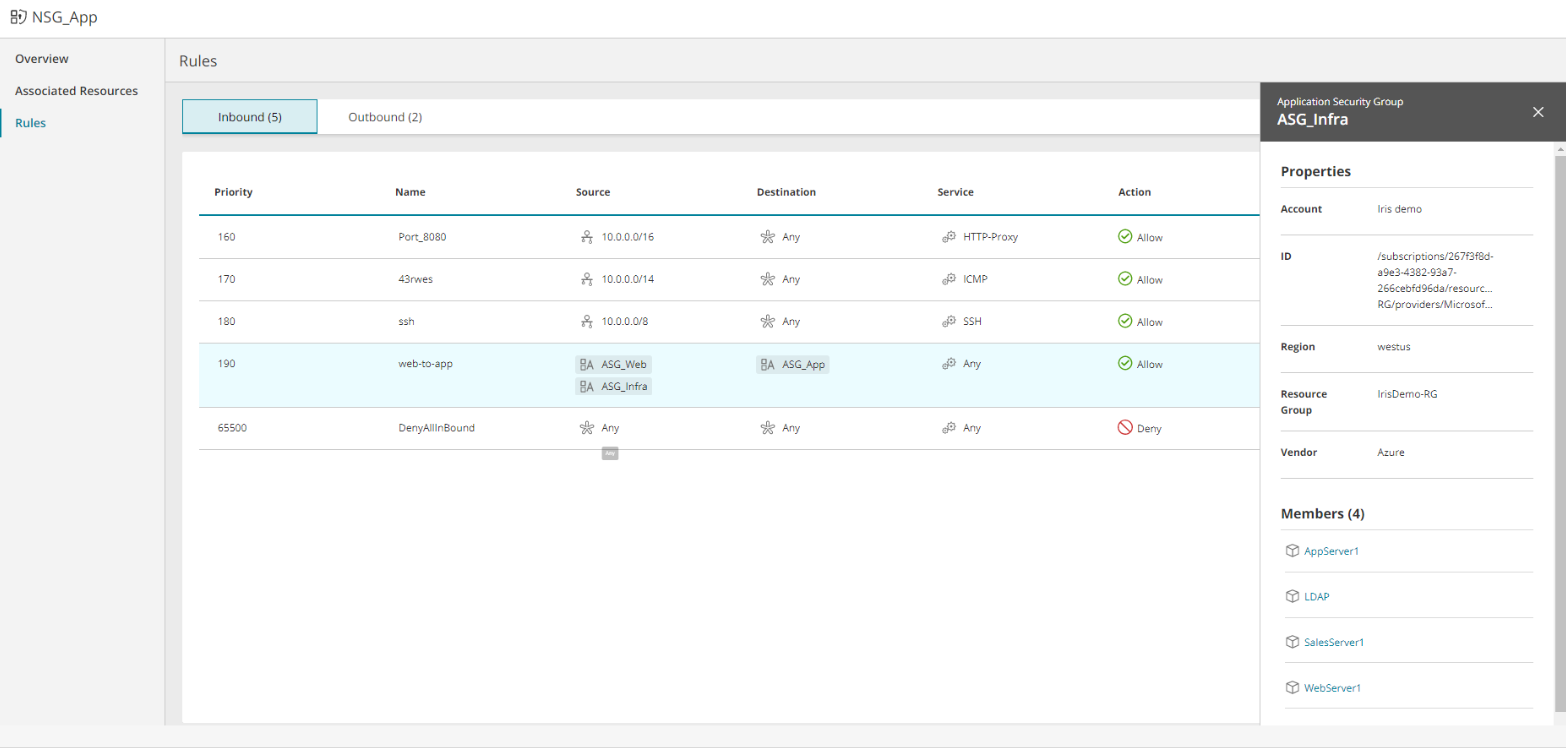
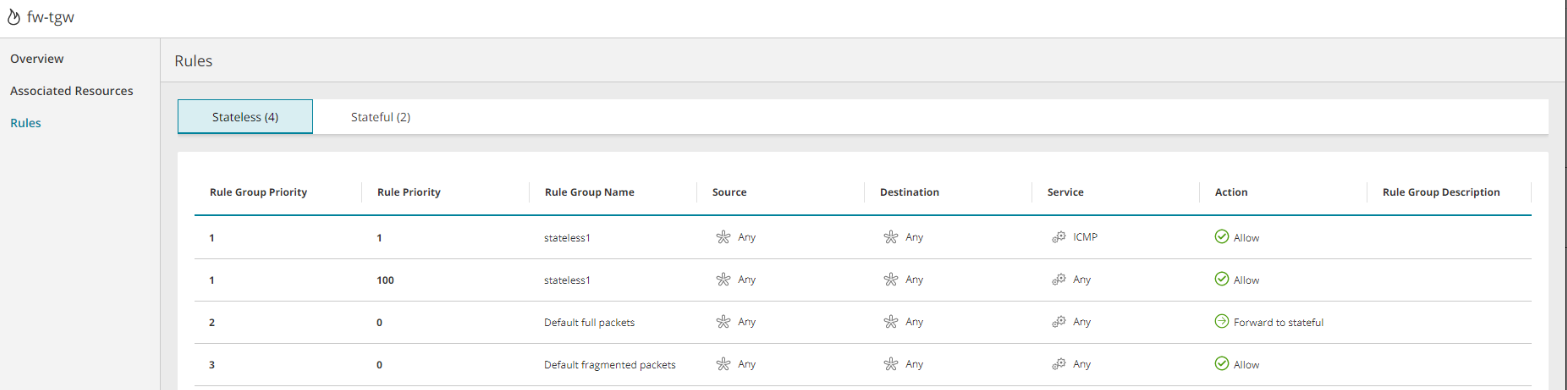
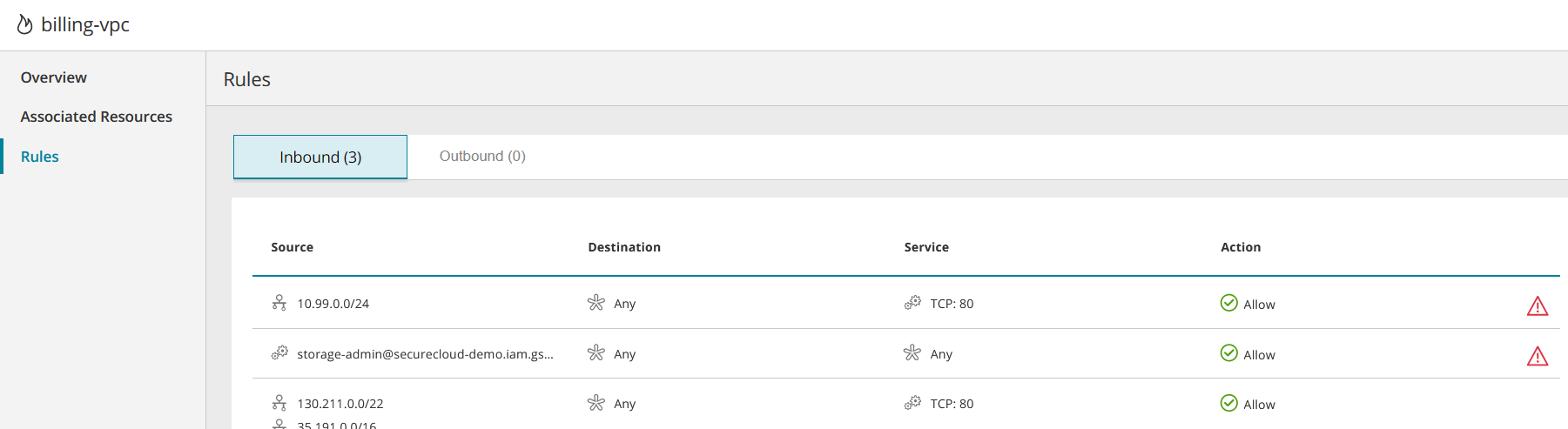
Security Control Rules
Display all rules defined by the security control.
They may be split into separate tabs such as inbound/outbound, NAT/network/application and/or stateless/stateful, depending on vendor and security control type and the information displayed for the rule will vary from one type of vendor and security control to another. It may include:
| Field | Comments |
|---|---|
|
Name |
The name of the rule |
|
Priority |
Sequence of handling the rule |
| Source | The source of the access. It can vary according to the cloud vendor and security control type e.g. IP, subnet, 'Any', a security group, the security control itself. You can click on some types of source to display more information, such as ID and members. |
| Destination | The destination of the access. It can vary according to the cloud vendor and security control type, e.g. IP, subnet, 'Any', a security group, the security control itself. You can click on some types of destination to display more information, such as ID and members. |
|
Service |
The communications service of the rule. It can contain multiple values and may include port number e.g. 'Any', TCP, TCP:80 |
|
Action |
Allow / Deny |
|
Description |
|
| Violations | Indicates that there are one or more violations of the rule. Click |
|
|
Enabled only when the violations icon
|
Examples of Security Control Rules:
Suppress Rule Violations
When the violations icon ![]() appears for a rule, you can click
appears for a rule, you can click ![]() to view the rule suppression options:
to view the rule suppression options:
Handle Violations at the Vendor Rule Level
Handle Violations at the SecureCloud Policy Level
-
Add a SecureCloud policy rule (for policy violations only)
-
Click
 on the rule. The violations appear. A separate line appears for each type of violation:
on the rule. The violations appear. A separate line appears for each type of violation:-
For cloud security policy violations, a separate line appears for each affected policy in violation
-
For risky ports and Permissive access a single line appears for each type if violations exist.
-
-
Select the appropriate on
-
Select Add to cloud policy. The Add Rule window appears with pre-populated values.
-
Modify values as needed - see Cloud Policy.
-
Add the rule.
-
-
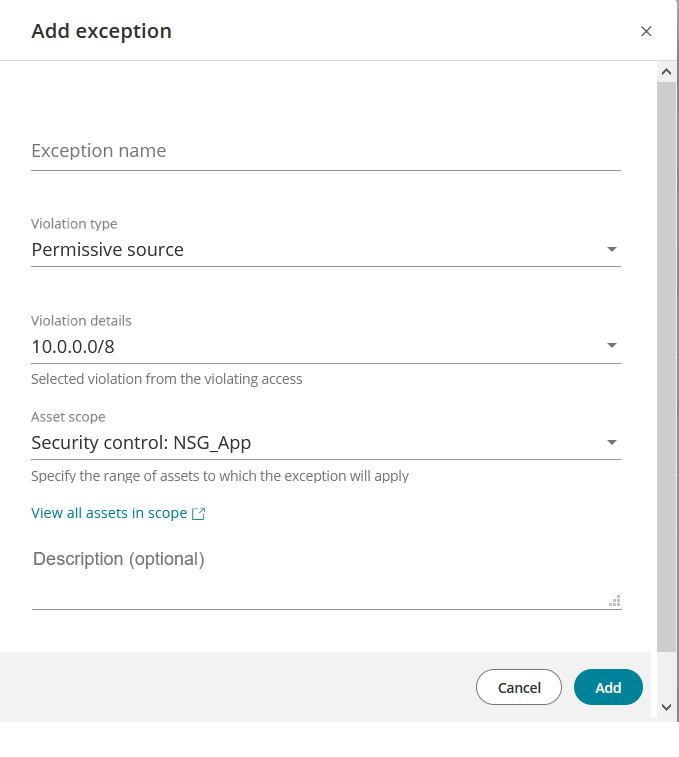
Add an exception (for risky ports and Permissive access violations only)
-
Click
 on the rule.
on the rule. -
Select Add exception. The Add Exception window appears.
-
Complete the exception details.
Exception Name: A name of your choice.
Violation Type: Risky port, Permissive source, Permissive service. If more than one type of violation exists for the selected access then select the type of exception you are defining. If only one type of violation exists for the access, it cannot be changed.
Violation Details: The ports, sources or services identified as violations. If more than one violation exists for the selected violation type and access, then select all those appropriate for the exception you are defining. If only one violation exists for this violation type and access, it cannot be changed.
Asset Scope: The assets to be included in the exception. Select one:
- Security control - all assets to which access is permitted by the security control allowing this access
- Asset tags - all assets having the exact same tags as this asset
- Cloud account - all assets in the cloud account in which this asset is located
- All cloud accounts - all cloud accounts monitored by SecureCloud
You can click on View all assets in scope to view all assets that will be affected by this exception
Description: Optional text of your choice.
- click Add to save.
Once added, exceptions can be viewed in Exceptions, where they can be deleted if desired.
-
-
Delete the rule from the cloud vendor definitions:
-
Click
 on the rule.
on the rule. -
Select Delete rule from cloud.
-
The rule will be removed from your cloud vendor definitions.
-
How Do I Get Here?
- Main Menu > Cloud Resources > Security Controls