On This Page
How it Works
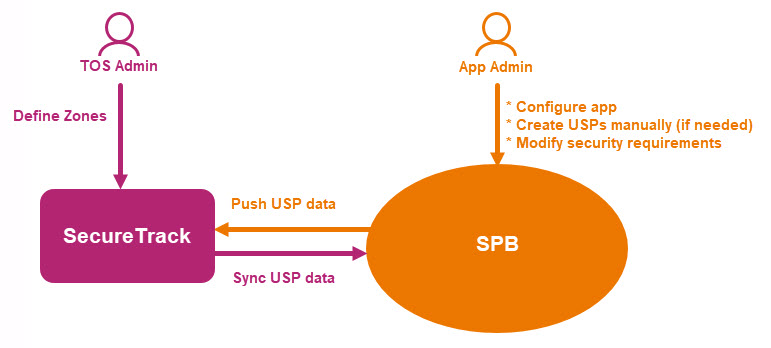
The Security Policy Builder (SPB) analyzes your network rules based on zones and devices, and populates Unified Security Policies (USPs) in the app based on existing access analysis between SecureTrack security zones.
For customers who already have USPs defined in SecureTrack, SPB syncs with SecureTrack to analyze the existing USPs to identify differences between existing access trends and the existing USP to enable making informed updates.
You can create, delete, and modify USP templates in SPB, When you create a new USP, you must select from the existing security zones in SecureTrack (either created and maintained by a SecureTrack administrator or automatically maintained by the IPAM Security Policy App (ISPA)) and the devices and cloud consoles monitored by SecureTrack. SPB matches every enforcement point access rule to a cell in the USP for every pair of source/destination zones, analyzes it, and populates your USP based on trends so that it represents the current state of your network. SPB empowers you to select the access enforcement points that you deem trustworthy and that accurately reflect the access that you want in your network. After you finish modifying USPs in SPB, you push selected USPs to SecureTrack so that both systems contain identical information.
Some access enforcement points might be outdated or incorrect, and there are cases for which they might violate a security policy. We recommend that you review USPs in SPB periodically for relevance and accuracy.
When there are changes in your network landscape, such as newly implemented firewall devices or security groups, you can click a button to analyze the access of the selected enforcement points to compare the results to the existing USPs that you have implemented. You can use the Conflicts feature to see what changed between the analysis results and the current matrix cell (in SPB or in SecureTrack). After resolving conflicts for a USP, you can push the changes to SecureTrack.
