On This Page
Security Best Practices Report
Overview
The Security Best Practices report provides the organization with the ability to ensure that security controls are based on common security best practices and to detect best practice failures. It lists all the rules that violate each best practice.
This report enables you to:
-
Identify the locations of risks across your network and which devices are most impacted
-
Prioritize rule optimization and remediation
-
Ensure awareness of the state of your network for audit purposes
Security Best Practices report supports the PCI DSS v4.0 standards.
What Can I See Here?
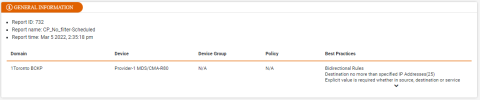
General Information
This section shows information such as report ID, name, time, and the domain details including the best practices selected during report creation.
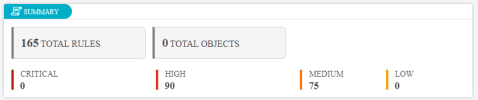
Summary
This section shows the total number of rules and objects with the breakdown by severity.
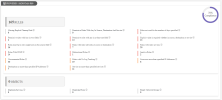
Rule and Object Best Practices per Device
These sections show the best practices that you selected when creating the report and the number of rules or objects that violate the best practices. The color of the bar next to the best practice indicates the severity of the violation:
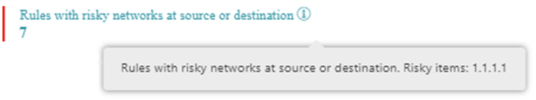
Hover over a tooltip to see an explanation for the best practice:
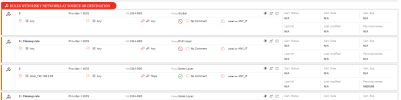
Click a best practice to see the violations details in a new section:
This compliance measurement shows the overall percentage of compliance for all best practices.
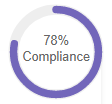
It is calculated as follows:
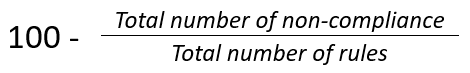
Create a Security Best Practices Report
Prerequisites
-
In the Settings > General page, the administrator must configure the outgoing SMTP server and the remote repository.
Procedure
-
From the Create (
 ) menu, click Security Best Practices.
) menu, click Security Best Practices.The Setup page for the report appears.
-
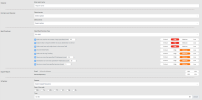
Complete the report fields:
-
General: Report name.
-
Domains and Devices: Select a domain and one or more devices or device groups.
-
Best Practices: Select the Best Practices Type. For best practices that require a value, you must supply the value AND select the check box. If not selected, STRE ignores the best practice.
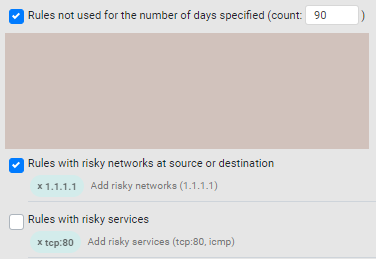
<tcp/udp>:<port>formaticmp
STRE only supports the following options for the risky services field:-
Export Report:
-
Email: Specify the recipients for notification emails. Press Tab or Enter to separate multiple email addresses.
The email message contains a link to the report in STRE. Reports can be generated as PDF or CSV files, and you can select either option or both (if enabled) to include in the email as an attachment. If the report file is larger than 4 MB, the attachment is compressed as a
.zipfile. -
Remote Repository: STRE can export reports using SFTP. Specify the report format - PDF or CSV.
If the report finished successfully, you can verify that the new files appear in the Reports Folder path, in the remote repository, configured by your administrator (see Send Reports Using SFTP).
-
- Schedule: Configure the following:
- Repeats: Select the frequency by which the report should run. Options include Daily, Weekly, and Monthly.
- Days of the week: Select one or more days on which the report should run.
- Time: Indicate the time at which the report should run.
When scheduling a report to run on a monthly basis, you must choose a single Day of the week value. For whichever weekday you choose (Mon, Tues, Wed, etc.) the report will run on the first of that day every month. Keep in mind, this may not correlate with the first calendar day of that month.
-
-
Click one of the following:
 : Saves the report. The Saved menu lists all saved and scheduled reports.
: Saves the report. The Saved menu lists all saved and scheduled reports. : Runs the report. After a report runs, you can view the results in the Repo menu.
: Runs the report. After a report runs, you can view the results in the Repo menu.
Severity Settings
The report builder provides a default severity setting for each of the available Best Practices checks. Severity settings are primarily intended to help prioritize the security checks included in the report results. All severity settings are suggestions and can be modified to suit the preferences, risk tolerance, and needs of your organization.
Whether you are using a group of checks listed under a specific regulatory template (i.e. PCI DSS, ISO 27001, etc.) or using the complete collection of checks for general risk management, the severity ratings can be used to convey four levels of urgency.
-
Critical — Failure to comply represents a material violation of widely accepted security best practices that significantly increases the likelihood of unauthorized access, regulatory exposure, or operational disruption. These findings typically reflect high-impact misconfigurations or behaviors that create clear and actionable exposure and should be remediated immediately.
-
High — Indicates a significant deviation from established security best practices that elevates organizational risk. While not necessarily indicative of an imminent compromise, these issues meaningfully weaken the security posture and should be addressed promptly to prevent escalation or downstream exposure.
-
Medium — Reflects conditions that degrade rule governance, visibility, or alignment with security principles. These findings do not usually pose an immediate threat but may increase risk over time, hinder auditability, or complicate investigation and response efforts if left uncorrected.
-
Low — Represents minor configuration inconsistencies, procedural gaps, or optimization opportunities. Addressing these findings improves policy hygiene, reduces "noise" in audits, and supports long-term maintainability, but they generally have minimal direct security impact.
Available Report Formats
When viewing the report output, use the Export menu to save the report data.
You can save the data for this report as a CSV file or PDF file. The CSV export option is useful when you want to create your own reports based on the specific data from the report configuration. The PDF output is limited to 100 rules.