On This Page
Security Compliance Report
Overview
The Security Compliance report lists all the security requests required to comply with SecureTrack Unified Security Polices (USPs). Security Compliance specifies whether the request complies with the rules defined in the devices.
This report enables you to:
-
Identify rules that are in violation with your USPs
-
Prioritize remediation efforts
What Can I See Here?
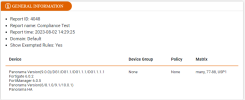
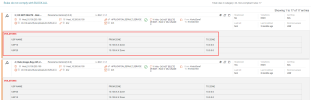
General Information
The General Information section includes details such as the report ID, name, time, domain, and the device information.
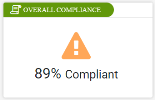
Overall Compliance
This section shows the average percentage of compliance for all devices in the report.
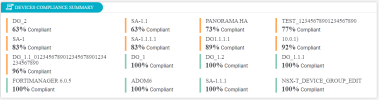
Devices Compliance Summary
This section lists the selected devices (and in the case of device groups - their members) and their level of compliance with the USPs.
The upper section displays each device and its overall compliance percentage, calculated as follows:
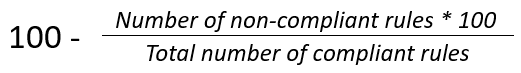
For each device, the color band indicates the compliance adherence:
-
Green: 100% compliant
-
Orange: 60-99%
-
Red: < 60%
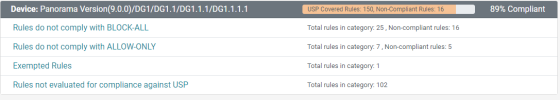
Devices Compliance Details
The lower section shows details for each device's compliance.
STRE calculates compliance based on the following metrics. Only the metrics that apply will appear in this section. For each metric, the report shows the total number of rules that are governed by the policy and the number of rules that violate block or allow specifications.
-
Rules do not comply with BLOCK-ALL: The USP definition between these zones states that all traffic should be blocked, but one or more rules exist that allow traffic. These rules are counted as violations.
-
Rules do not comply with ALLOW-ONLY: The USP definition between these zones states that traffic is allowed for specified services or applications. A violation occurs when a rule exists with a service/application that is not allowed.
-
Rules do not comply with BLOCK-ONLY: The USP definition between these zones states that traffic is blocked for specified services or applications. A violation occurs when a rule exists with a service/application that is not blocked.
-
Exempted Rules: If selected during report creation, this metric shows the number of exempted rules. Exempted rules are those that STRE does not consider when calculating violations. You define these rules in SecureTrack.
-
Rules not evaluated for compliance against USP: These rules are not relevant for the USP because either the source or the destination do not match any source or destination in any USP.
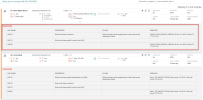
Rule Cards
For the metrics that are not 100% compliant, you can drill down to reveal the rule information that includes details about each violation. You can use this information to decommission rules or change definitions in your USPs.
Examples:
-
For BLOCK-ONLY, you see violations by USP and associated zones.
-
For ALLOW-ONLY, you see violations by USP with a description for each violated property.
Create a Security Compliance Report
Prerequisites
-
In the Settings > General page, the administrator must configure the outgoing SMTP server and the remote repository.
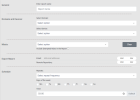
Procedure
-
From the Create (
 ) menu, click Security Compliance.
) menu, click Security Compliance.The Setup page for the report appears.
-
Complete the report fields:
-
General: Report name.
-
Domains and Devices: Select a domain and one or more devices or device groups.
-
Matrix: After selecting a domain, select one or more USPs.
-
Include Exempted Rules: Exempted rules are those that you want to suppress from violation calculations and reporting. Select this check box if you want to include these exempted rules in the Security Compliance report.
To learn more about USP Exceptions, see USP Exceptions.
Note: STRE shows only fully exempted rules. For example, if a rule is exempted in USP A but not exempted in USP B, you will not see this rule in the Security Compliance report - even if you do not select USP B in the Matrix field.-
Export Report:
-
Email: Specify the recipients for notification emails. Press Tab or Enter to separate multiple email addresses.
The email message contains a link to the report in STRE. Reports can be generated as PDF or CSV files, and you can select either option or both (if enabled) to include in the email as an attachment. If the report file is larger than 4 MB, the attachment is compressed as a
.zipfile. -
Remote Repository: STRE can export reports using SFTP. Specify the report format - PDF or CSV.
If the report finished successfully, you can verify that the new files appear in the Reports Folder path, in the remote repository, configured by your administrator (see Send Reports Using SFTP).
-
- Schedule: Configure the following:
- Repeats: Select the frequency by which the report should run. Options include Daily, Weekly, and Monthly.
- Days of the week: Select one or more days on which the report should run.
- Time: Indicate the time at which the report should run.
When scheduling a report to run on a monthly basis, you must choose a single Day of the week value. For whichever weekday you choose (Mon, Tues, Wed, etc.) the report will run on the first of that day every month. Keep in mind, this may not correlate with the first calendar day of that month.
-
-
Click one of the following:
 : Saves the report. The Saved menu lists all saved and scheduled reports.
: Saves the report. The Saved menu lists all saved and scheduled reports. : Runs the report. After a report runs, you can view the results in the Repo menu.
: Runs the report. After a report runs, you can view the results in the Repo menu.
Available Report Formats
When viewing the report output, use the Export menu to save the report data.
You can save the data for this report as a PDF or as a CSV file. The CSV export option is useful when you want to create your own reports based on the specific data from the report configuration.
When exporting a report with more than 1000 rules, only 1000 rules will be included.